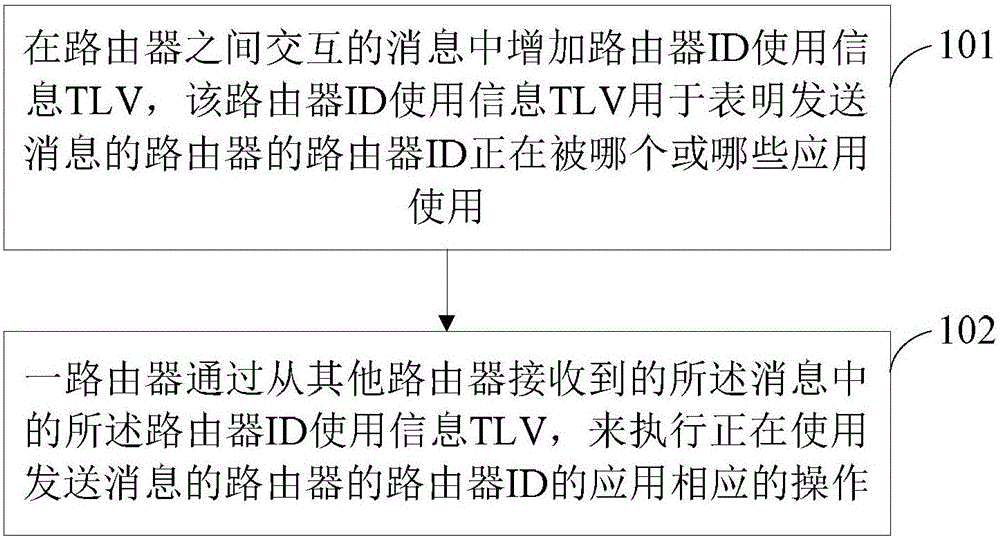
Message exchange method and device for routers
A message interaction and router technology, applied in data exchange network, digital transmission system, electrical components, etc., can solve problems such as redundant operation and waste of resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] The specific format of router ID usage information TLV in the embodiment of the present invention is defined as follows:
[0051] Router ID Usage Information – This optional TLV should appear at most once in the LSP to indicate the usage of the router ID.
[0052] Type code – undetermined
[0053] length – the total length of the content
[0054] content-
[0055] Sub-TLV Type Code – 1 or 2.
[0056] Sub-TLV Length – Sub-TLV content length.
[0057] Sub-TLV content –
[0058]
[0059] Among them, sub-TLV type 1: IPv4 router ID usage information
[0060] This sub-TLV contains IPv4 routing ID usage information, and it should appear at most once in the router ID usage information TLV. In consideration of flexibility and easy expansion, the length of the sub-TLV is not fixed at 1 byte (eight bits).
[0061] Sub-TLV Type 2: IPv6 Router ID Usage Information
[0062] This sub-TLV contains IPv6 routing ID usage information, and it should appear at most once in the ro...
application example 1
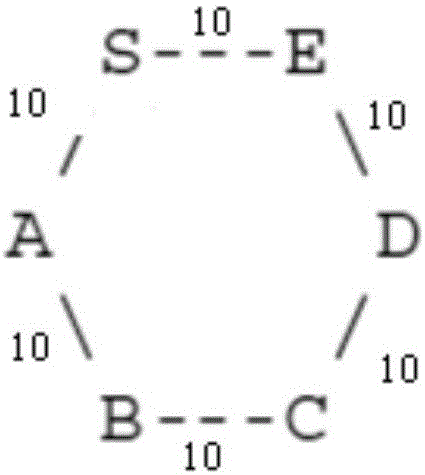
[0066] suppose as figure 2 In the network topology, the directly connected nodes are interconnected, and the two-way Metric cost value (10 in the figure) is the same. Now try to generate a Remote-LFA standby route for link S-E, and it can be known that node C is a candidate PQ node according to the algorithm. If the information TLV used by analyzing the router ID of node C finds that the router ID carried by node C does not apply to Remote-LFA, then node S will immediately abandon the standby topology from node S to node C, and will also give up trying to establish a slave topology. A tunnel from node S to node C.
application example 2
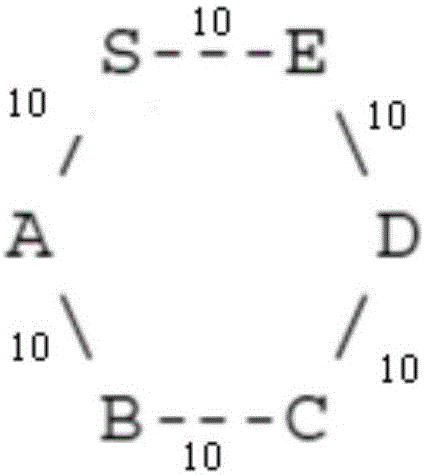
[0067] Application Example 2: Assume that image 3 In the network topology, directly connected nodes are interconnected, and the two-way metric value is the same. Now establish a TE tunnel for the S node to the E node. Although the router ID is obtained from the LSP of the E node, if it is found that the router ID carried by the E node does not apply to the TE by analyzing the router ID usage information TLV of the E node, then the S node will immediately give up the establishment of a link from the S node to the E node. The TE tunnel of the node.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com