Multi-dimensional unlocking method for user equipment and user equipment
A user equipment, multi-dimensional technology, applied in branch office equipment, data processing input/output process, unauthorized/fraudulent call prevention, etc., can solve the problems of reducing the security of user equipment unlocking and leaking privacy, and achieve Improve unlocking security and protect personal information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
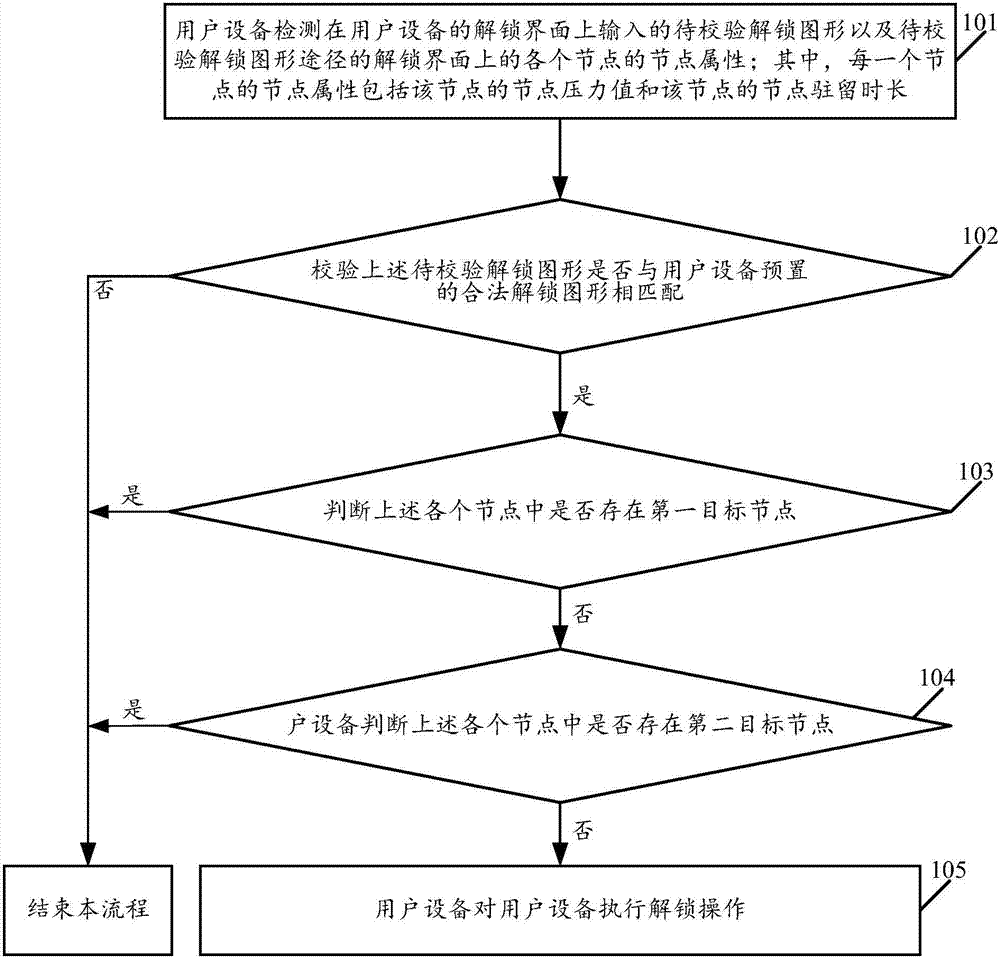
[0055] see figure 1 , figure 1 It is a schematic flowchart of a method for controlling user equipment disclosed in an embodiment of the present invention. like figure 1 As shown, the method for controlling the user equipment may include the following steps.
[0056] 101. The user equipment detects the unlock graphics to be verified input on the unlock interface of the user equipment and the node attributes of each node on the unlock interface of the unlock graphic path to be verified; wherein, the node attributes of each node include the node of the node The pressure value and the node dwell time of the node.
[0057] In the embodiment of the present invention, the user equipment may include but not limited to mobile phones, mobile tablets, notebook computers, personal digital assistants (Personal Digital Assistant, PDA), mobile Internet devices (Mobile Internet Device, MID) and other devices that can unlock the screen. Terminal equipment; Wherein, the operating system of ...
Embodiment 2
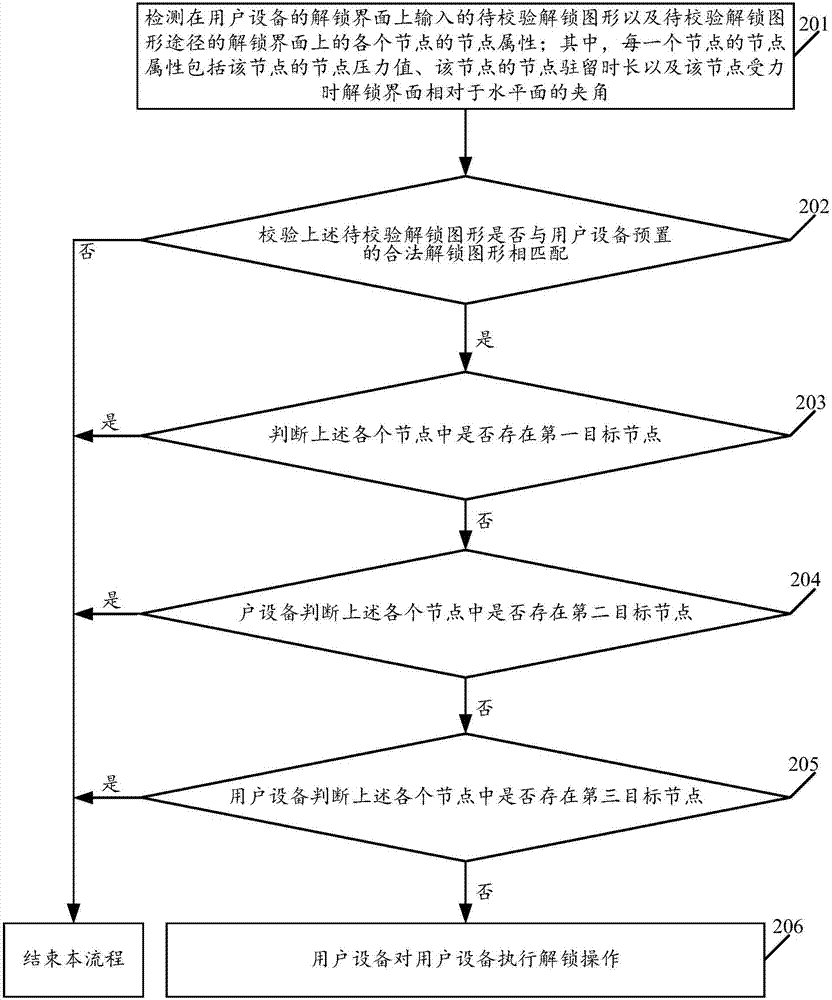
[0070] see figure 2 , figure 2 It is a schematic flowchart of another user equipment control method disclosed in the embodiment of the present invention. like figure 2 As shown, the method for controlling the user equipment may include the following steps.
[0071] 201. The user equipment detects the node attribute of each node on the unlocking interface of the unlocking figure to be verified inputted on the unlocking interface of the user equipment and the path of the unlocking figure to be verified; wherein, the node attribute of each node includes the node of the node The pressure value, the node dwell time of the node, and the included angle of the unlocking interface relative to the horizontal plane when the node is under force.
[0072]For example, the user equipment detects that the unlock pattern to be verified input by the user on the unlock interface of the user equipment is "L", and the node attributes of the four nodes on the unlock interface that the unlock ...
Embodiment 3
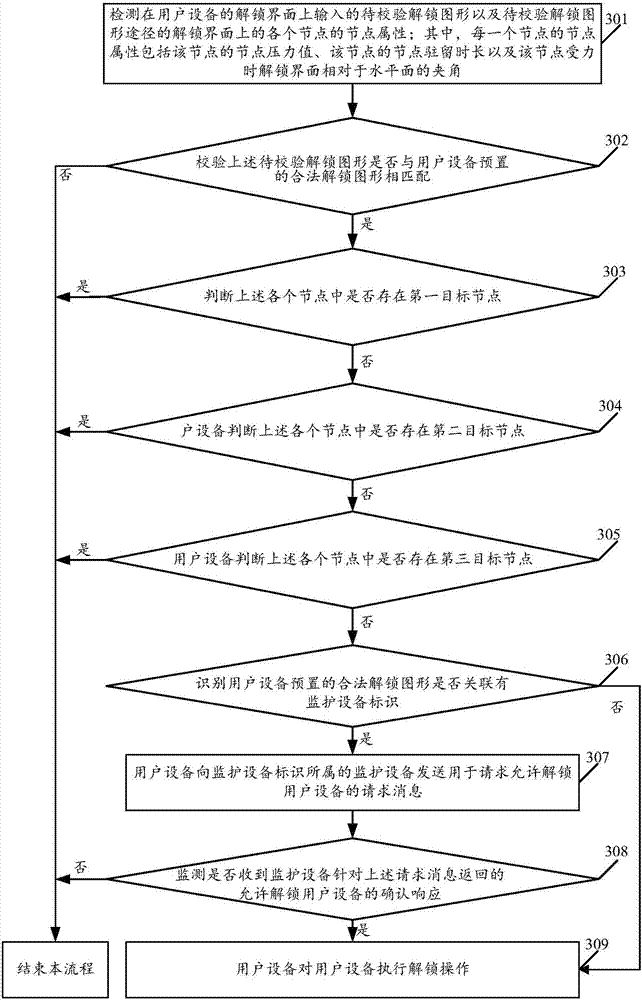
[0084] see image 3 , image 3 It is a schematic flowchart of another user equipment control method disclosed in the embodiment of the present invention. like image 3 As shown, the method for controlling the user equipment may include the following steps.
[0085] 301. The user equipment detects the unlock graphic to be verified input on the unlock interface of the user equipment and the node attributes of each node on the unlock interface of the unlock graphic path to be verified; wherein, the node attribute of each node includes the node of the node The pressure value, the node dwell time of the node, and the included angle of the unlocking interface relative to the horizontal plane when the node is under force.
[0086] For example, the user equipment detects that the unlock pattern to be verified input by the user on the unlock interface of the user equipment is "L", and the node attributes of the four nodes on the unlock interface that the unlock pattern "L" to be ver...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com