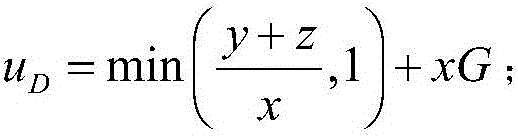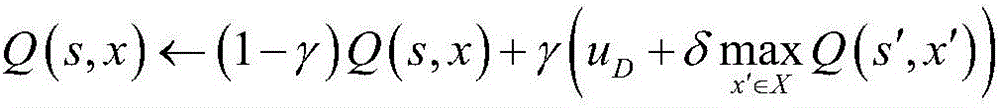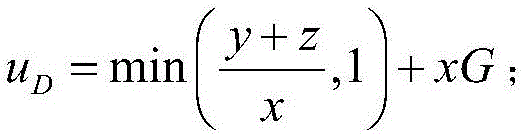Method for detecting persistent attack of cloud storage system
A cloud storage system and detection method technology, applied in transmission systems, electrical components, etc., can solve problems such as the uncertainty of attack behavior and increase the difficulty of attack detection, so as to suppress attack motivation, suppress attack behavior, and improve data privacy performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The following examples will further illustrate the present invention.
[0024] Embodiments of the present invention include the following steps:
[0025] 1) The defense system quantifies the scanning time interval x into 10 levels, x∈X=[0.1,0.2,...,1]. At the same time, observe the attack time interval and duration of the cloud storage device being attacked, and quantify the attack interval y and duration z into 10 levels, y∈[0.1,0.2,..,1], z∈[0.1,0.2 ,..,1]. The defense system provides detection services for all cloud storage devices on the cloud platform, and independently selects a scanning interval for each cloud storage device.
[0026] 2) Initialize the Q value matrix to 0, and the Q value matrix is Q(s,x), which represents each available state s of the defense system, and assigns a corresponding Q value to all optional scanning time intervals x; where the defense system The state s of the state is the sum y+z of the attack time interval and duration of the p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com