Application permission management method and system, and equipment
A technology for applying permissions and management methods, applied in the terminal field, which can solve the problems of low security and inflexible management mechanism.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
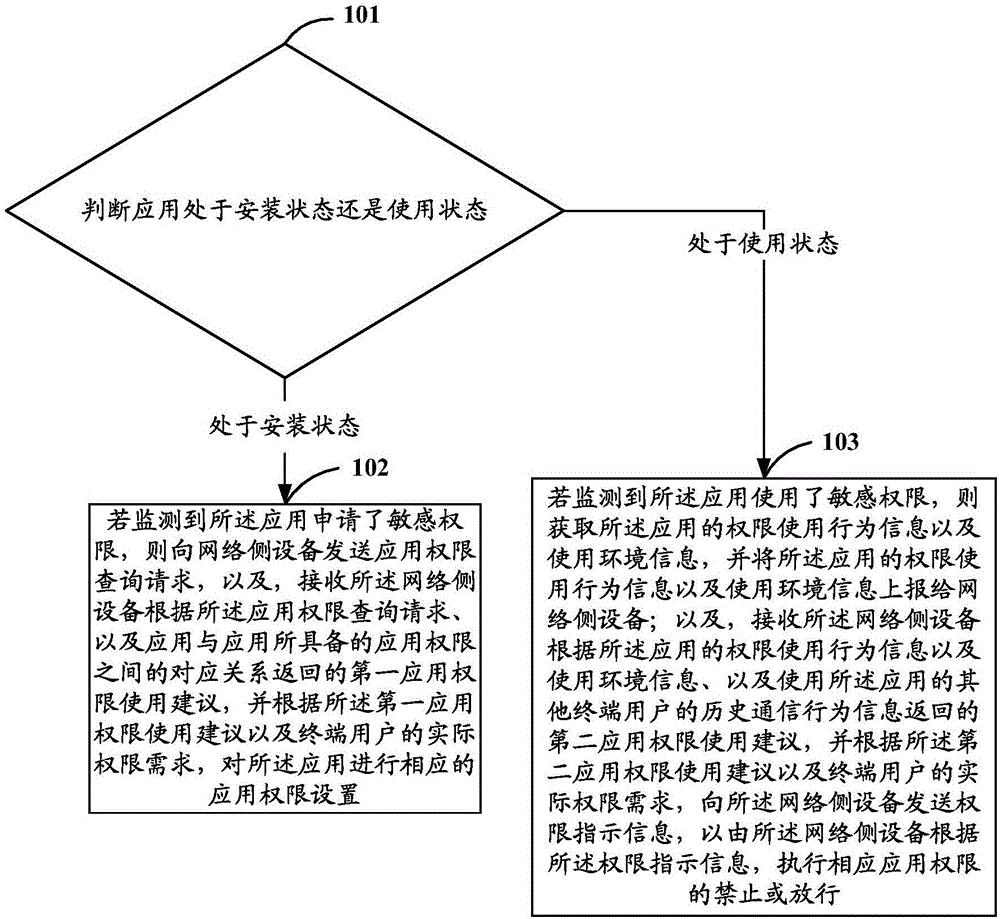
[0046] Embodiment 1 of the present invention provides a method for managing application rights, specifically, as figure 1 As shown, it is a schematic flowchart of the method for managing application rights described in Embodiment 1 of the present invention, and the method for managing application rights may include the following steps:
[0047] Step 101: Determine whether the application is installed or in use, and if it is installed, execute step 102; if it is in use, execute step 103.
[0048] Step 102: If it is detected that the application has applied for sensitive permissions, send an application permission query request to the network side device, and receive the network side device according to the application permission query request, and the application and the application permissions possessed by the application Corresponding relationship between the returned first application permission usage suggestion, and according to the first application permission usage sugges...
Embodiment 2
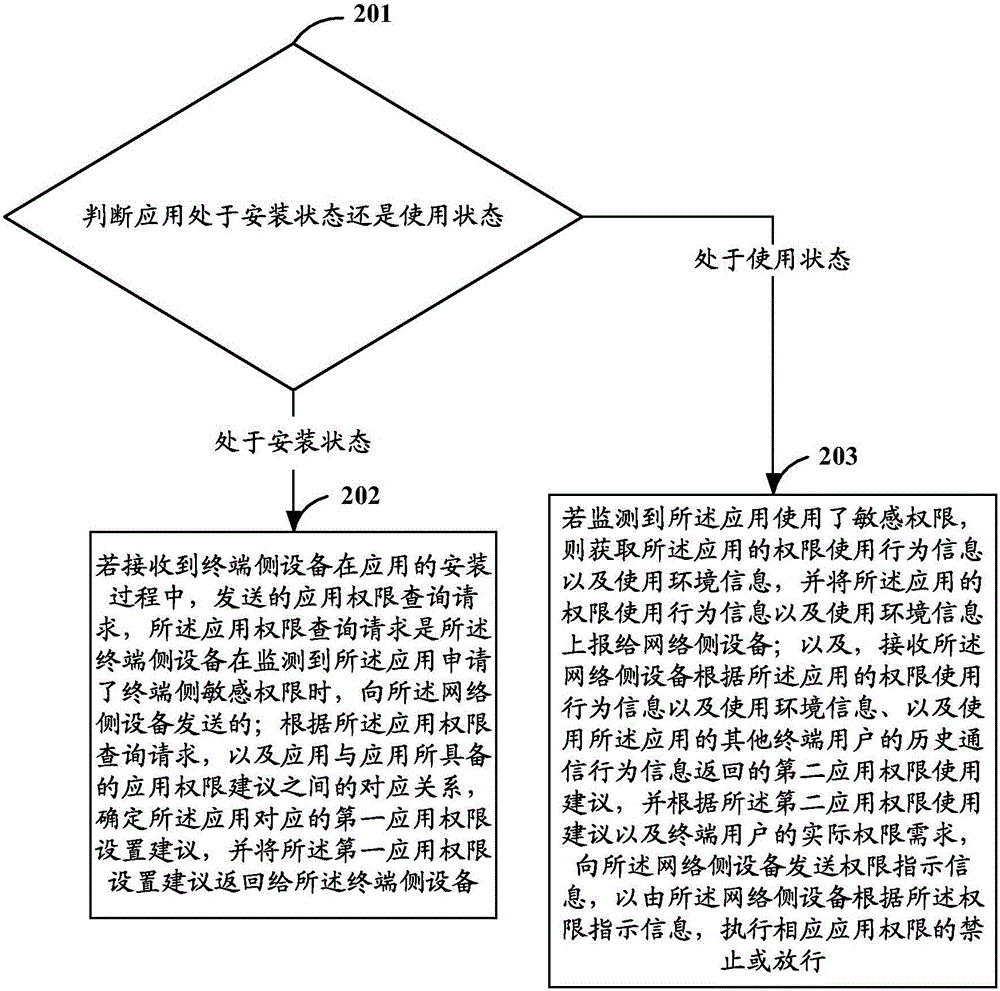
[0100] Embodiment 2 of the present invention provides a method for managing application permissions with a network-side device as the execution subject, specifically, as figure 2 As shown, it is a schematic flowchart of a method for managing application rights described in Embodiment 2 of the present invention. The method for managing application rights may include the following steps:
[0101] Step 201: Determine whether the application is installed or in use, and if it is installed, execute step 202; if it is in use, execute step 203.
[0102] Step 202: If an application permission query request sent by the terminal-side device during the application installation process is received, the application permission query request is sent to the terminal-side device when it detects that the application has applied for sensitive permissions. sent by the network side device; according to the application permission query request and the corresponding relationship between the applicat...
Embodiment 3
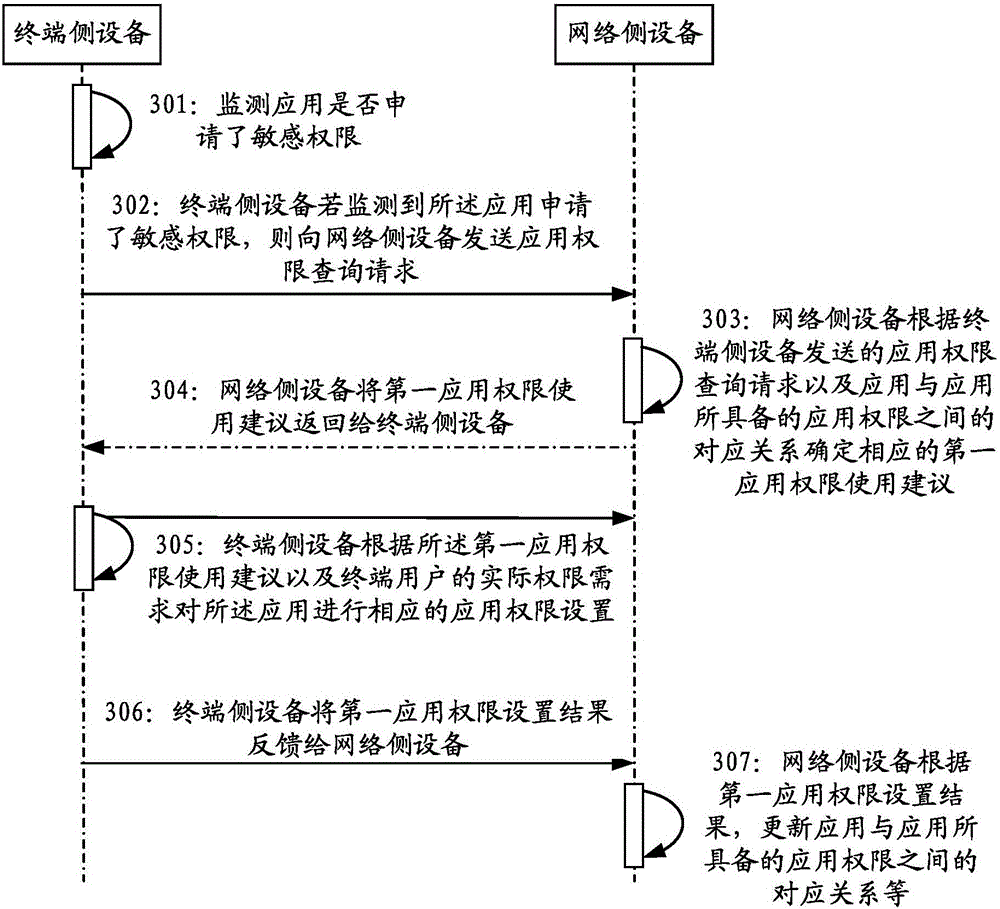
[0140] In the following, the method for managing application rights involved in Embodiment 1 and Embodiment 2 of the present invention will be specifically described by taking interactive execution between a terminal-side device and a network-side device as an example.
[0141] like image 3 As shown, it is a schematic flowchart of the first application rights management method described in Embodiment 3 of the present invention. The first application rights management method is applicable to application installation scenarios, and includes the following steps:
[0142] Step 301: During the application installation process, the terminal-side device monitors whether the application has applied for sensitive permissions.
[0143] Specifically, the terminal-side device can monitor whether the application has applied for sensitive permissions by analyzing the configuration file of the application (such as manifest.xml, etc.).
[0144] Step 302: If the terminal-side device detects ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com