Trojan detection method and device based on Linux system
A detection method and detection device technology, applied in the direction of computer security devices, instruments, electrical digital data processing, etc., can solve the problems of a large number of data comparison, low efficiency, large system resources, etc., and achieve high efficiency without data comparison Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
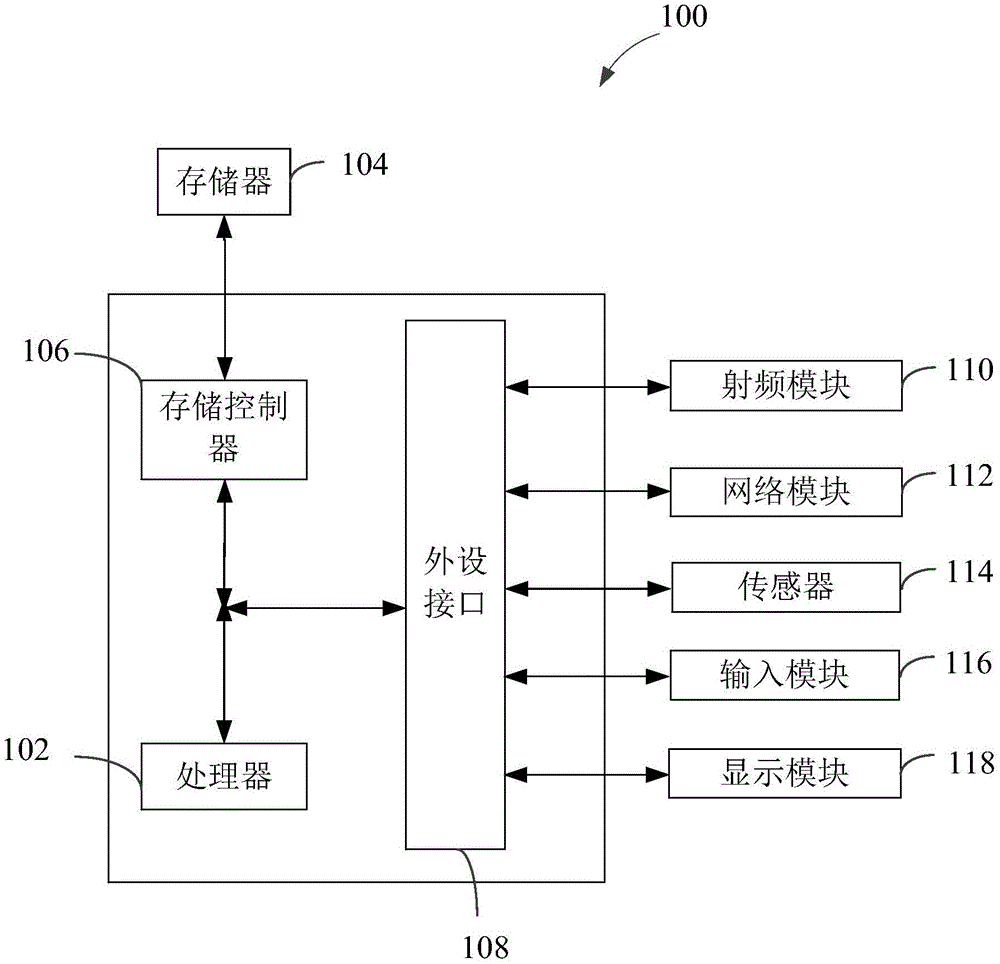
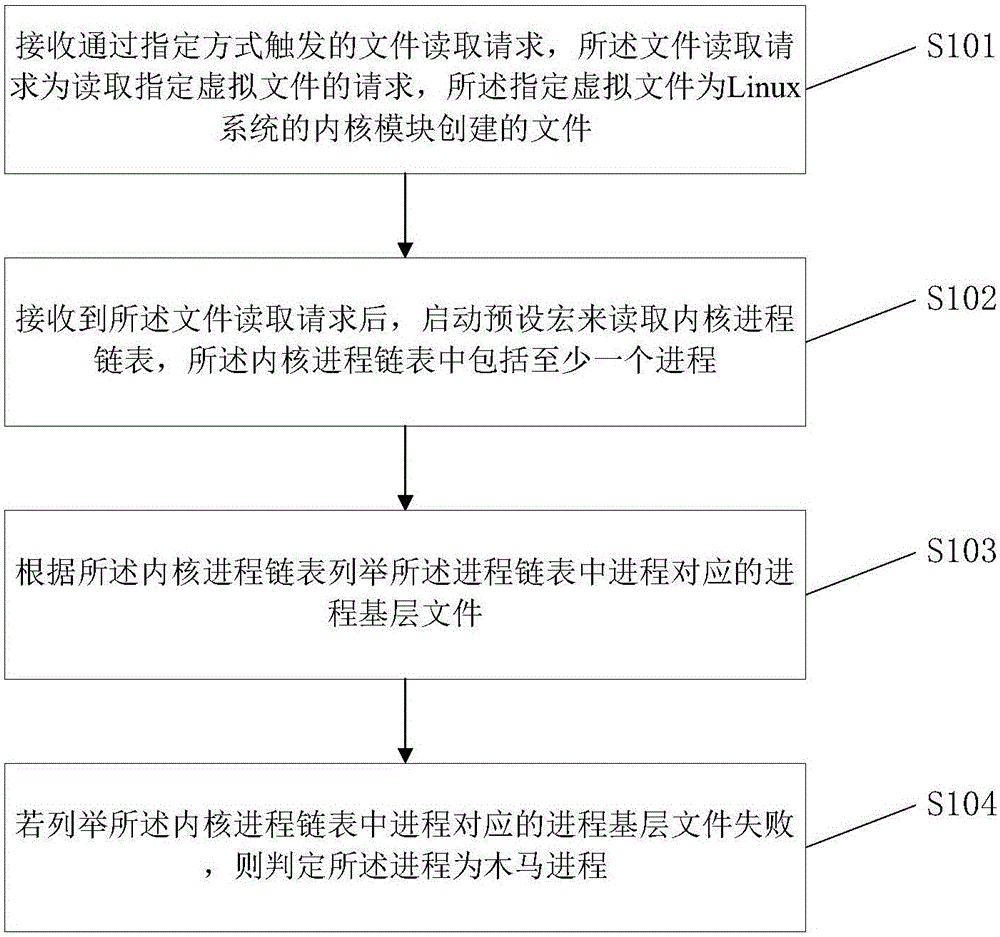
[0036] The present embodiment provides a kind of Trojan detection method based on Linux system, and the method of the present embodiment can be used for figure 1 As shown in the electronic terminal 100, such as figure 2 As shown, the method of the present embodiment includes the following steps:
[0037] Step S101. Receive a file read request triggered by a specified method, the file read request is a request to read a specified virtual file, and the specified virtual file is a file created by a kernel module of the Linux system.
[0038] The specified method may be to trigger a specified button in the security guard's Trojan killing function interface, such as the "quick scan" or "full scan" button in the interface, thereby triggering the file read request. In detail, the virtual file is the / proc / ps_list virtual file created by the kernel module of the Linux system. The virtual files constitute a virtual system VFS (Virtual File System), and the VFS is also called a virtu...
no. 2 example
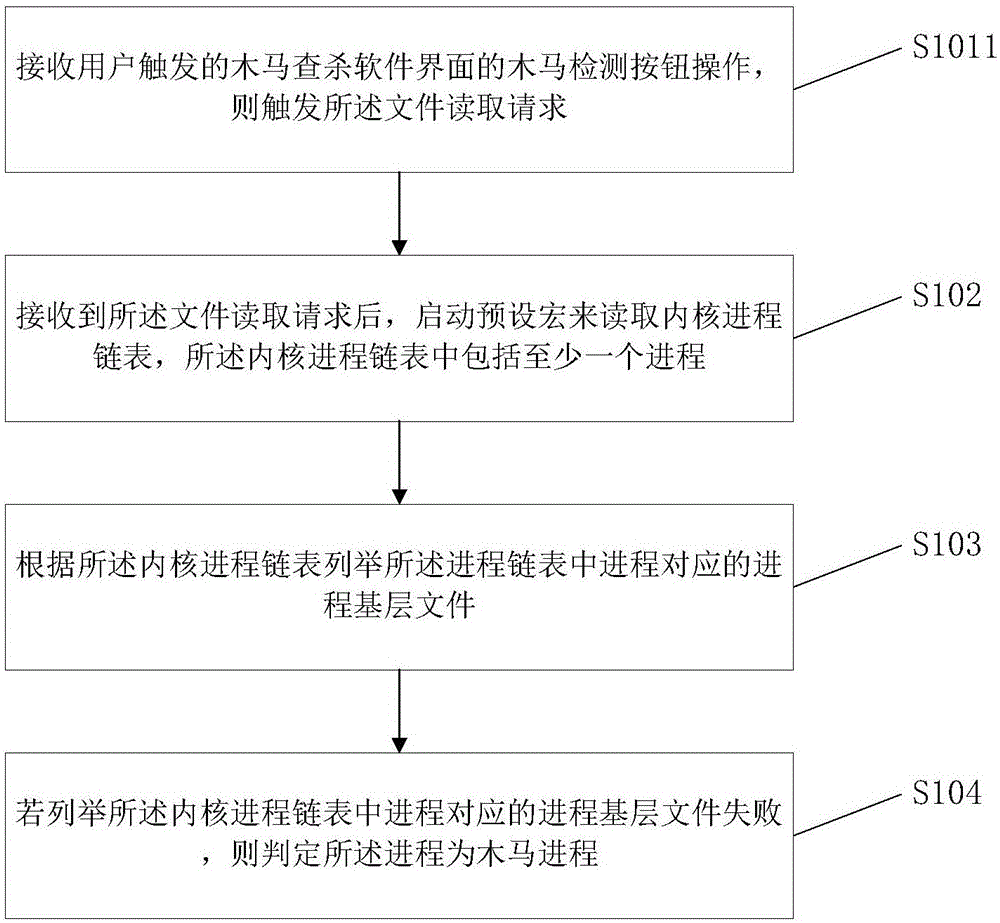
[0056] This embodiment provides a method for detecting a Trojan horse based on a Linux system. This embodiment is similar to the first embodiment, the difference is that please refer to image 3 or Figure 4 , the method of this embodiment includes:
[0057] Step S101 may specifically include:
[0058] Step S1011 , receiving the operation of the Trojan horse detection button on the Trojan horse detection and killing software interface triggered by the user, and triggering the file read request.
[0059] Alternatively, step S1012, receiving a preset time interval set by the user to perform Trojan horse scanning and killing operations, the preset time interval automatically triggering the file read request.
[0060] In detail, the application background of the first embodiment may be a software for detecting and killing Trojan horses. image 3 It is a flow chart of a method in an embodiment manner of this embodiment. The receiving of the file reading request triggered by a s...
no. 3 example
[0069] This embodiment provides a method for detecting a Trojan horse based on a Linux system. This embodiment is similar to the first embodiment, the difference is that please refer to Figure 5 , the method of this embodiment includes:
[0070] Step S101. Receive a file read request triggered by a specified method, the file read request is a request to read a specified virtual file, and the specified virtual file is a file created by a kernel module of the Linux system.
[0071] Step S102 , after receiving the file read request, start a preset macro to read the kernel process link list, and the kernel process link list includes at least one process.
[0072] Further, the processes in the kernel process linked list are the processes currently running in the electronic terminal 100 .
[0073] Step S103, including:
[0074] Step S1031, read the processes in the kernel process linked list one by one.
[0075] Specifically, the process ID can uniquely identify a process, and t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com