A flow diversion method and device
A traffic and equipment technology, applied in the computer field, can solve the problems of expensive bandwidth and limited access bandwidth for defense capabilities, and achieve the effect of improving the defense against DDOS attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
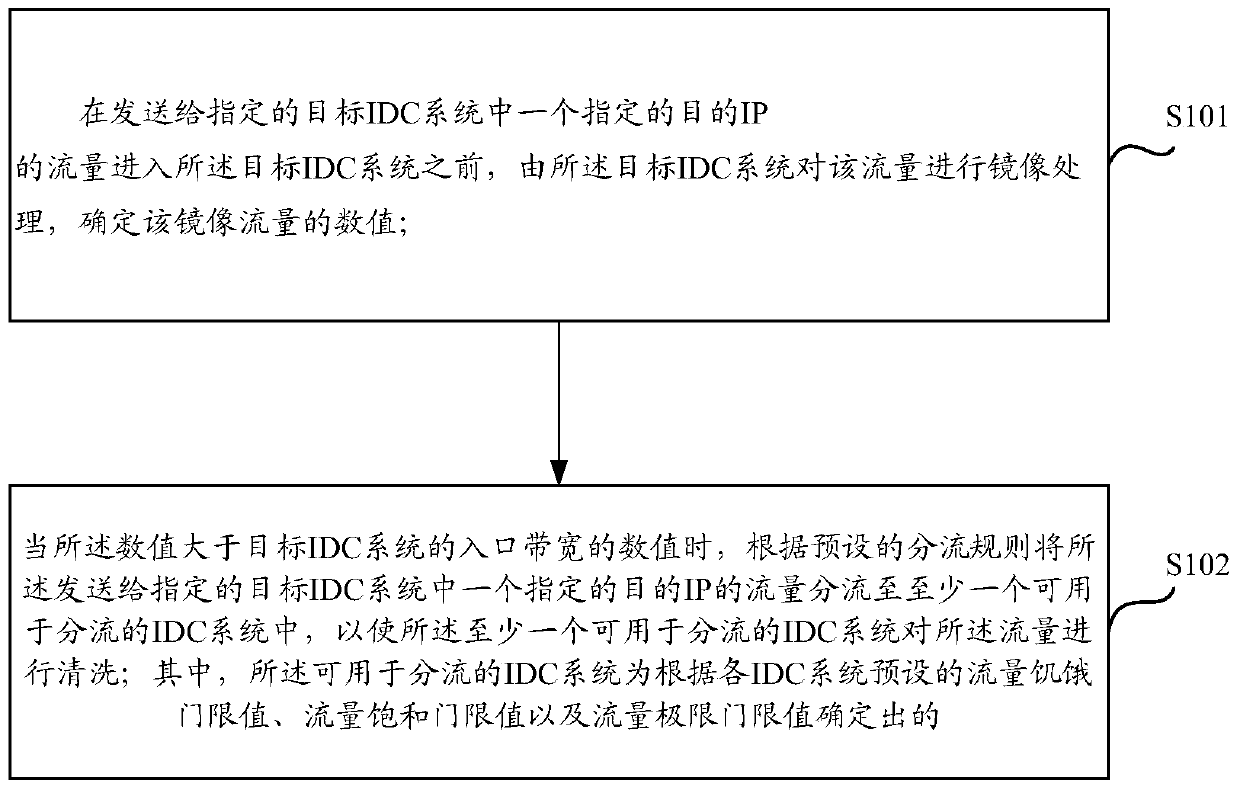
[0023] The following will describe in detail with reference to the embodiments of the present application.
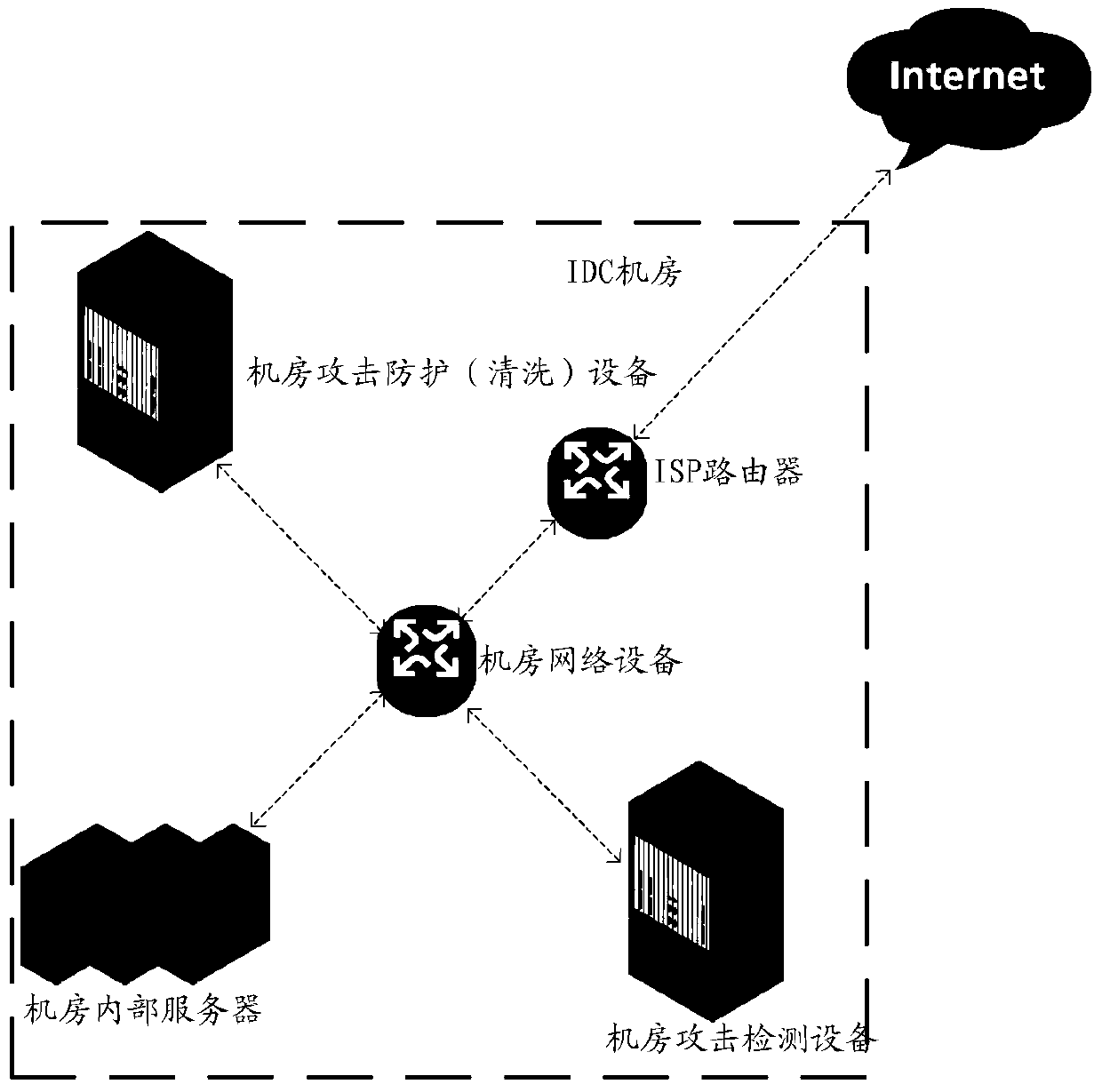
[0024] Black hole processing refers to a method of discarding all traffic sent to the destination IP in the target IDC system, which is mostly seen on the ISP side device.
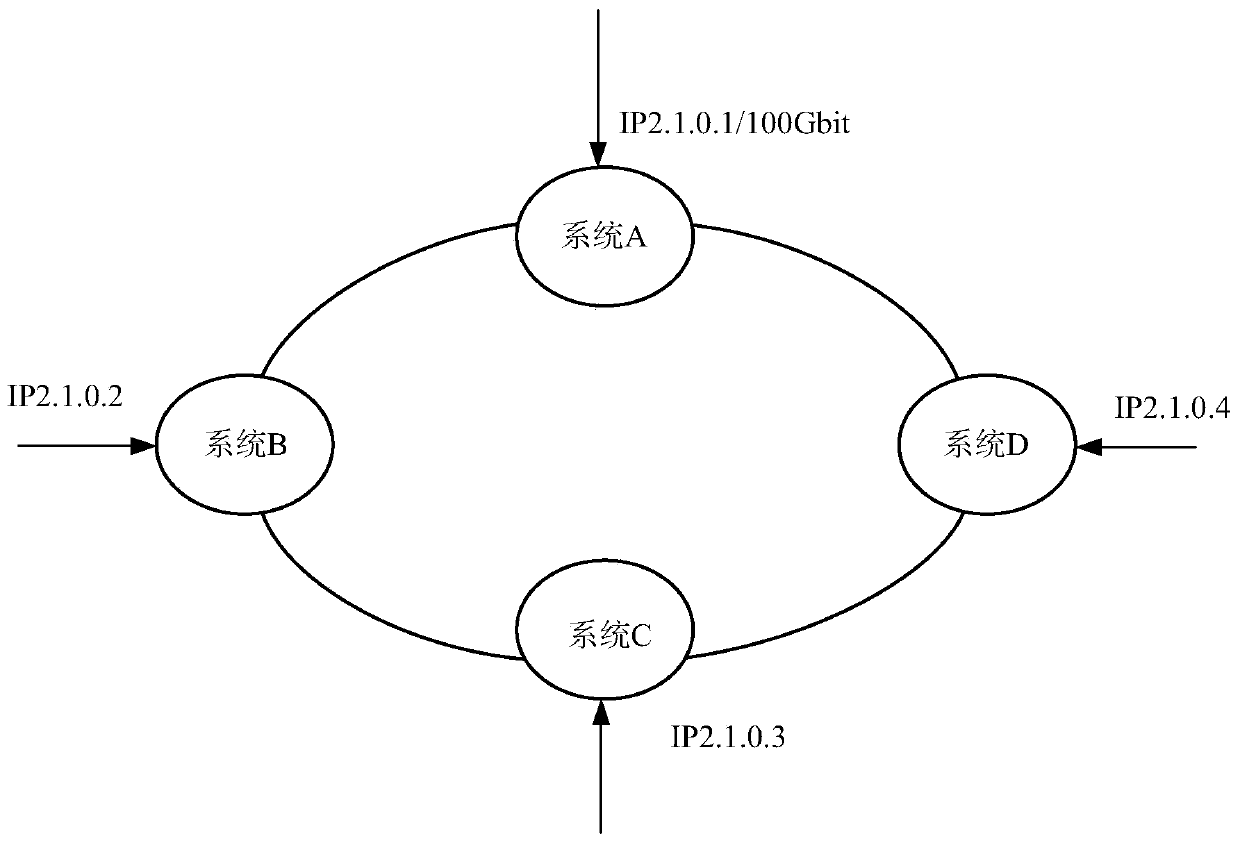
[0025] The specific black hole processing process, such as figure 2 Shown: When the destination IP 2.1.0.1 in the target IDC system A suffers 100Gbit DDOS attack traffic, and the size of the DDOS attack traffic exceeds the ingress bandwidth of the target IDC system A, in the actual application scenario, the IDC The ingress bandwidth of the system is generally 20Gbit; according to the traditional DDOS defense scheme, in order to protect other IPs (such as IP 2.2.0.1, IP 2.3.0.1, etc.) in the target IDC system A from being affected, the destination IP 2.1.0.1 Inform the upstream ISP side of the target IDC system A to directly perform black hole processing; in this way, although the traffic sent to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com