Method and device of obtaining banknote security thread boundary
A security thread, banknote technology, applied in the field of obtaining banknote security thread borders
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
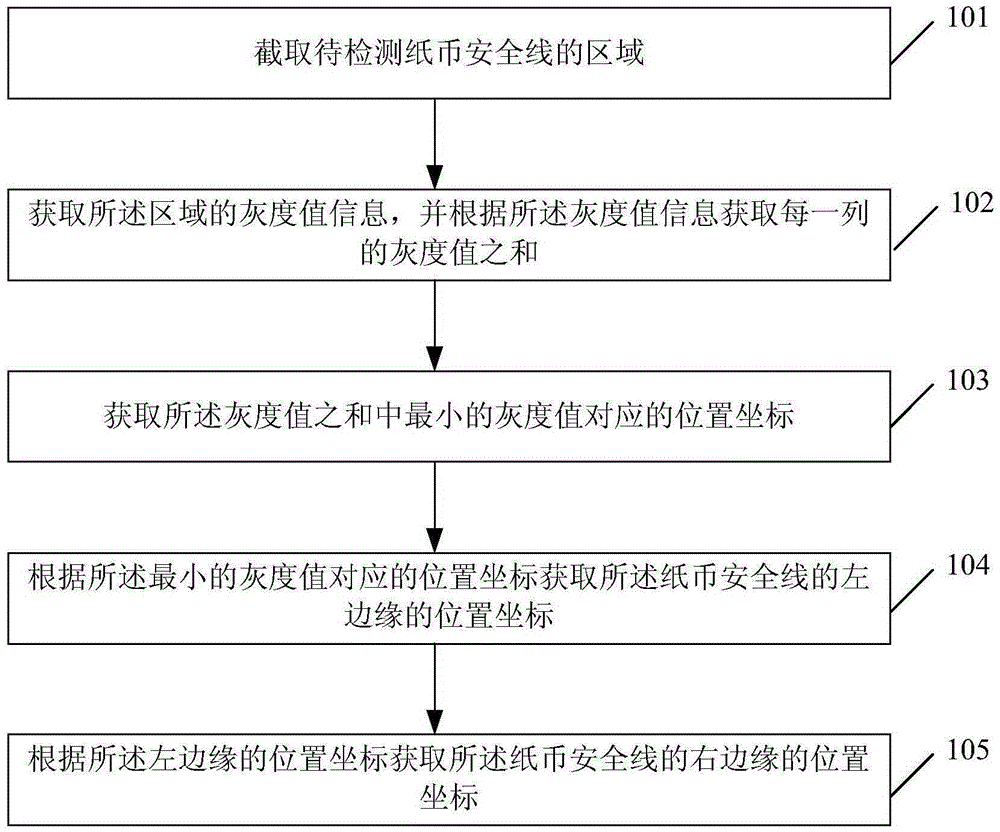
[0075] refer to figure 1 , figure 1 It is a schematic flow chart of a method for obtaining banknote security line boundaries according to an embodiment of the present invention.
[0076] In Embodiment 1, the method for obtaining the banknote security line boundary includes:
[0077] Step 101, intercepting the area of the banknote security line to be detected;
[0078] Preferably, said intercepting the area of the banknote security thread to be detected includes:
[0079] According to the infrared transmission diagram of the banknote to be detected and the area facing the interception security line;
[0080] According to the infrared transmission diagram of the banknote to be detected and the area facing to intercept the security line, it includes:
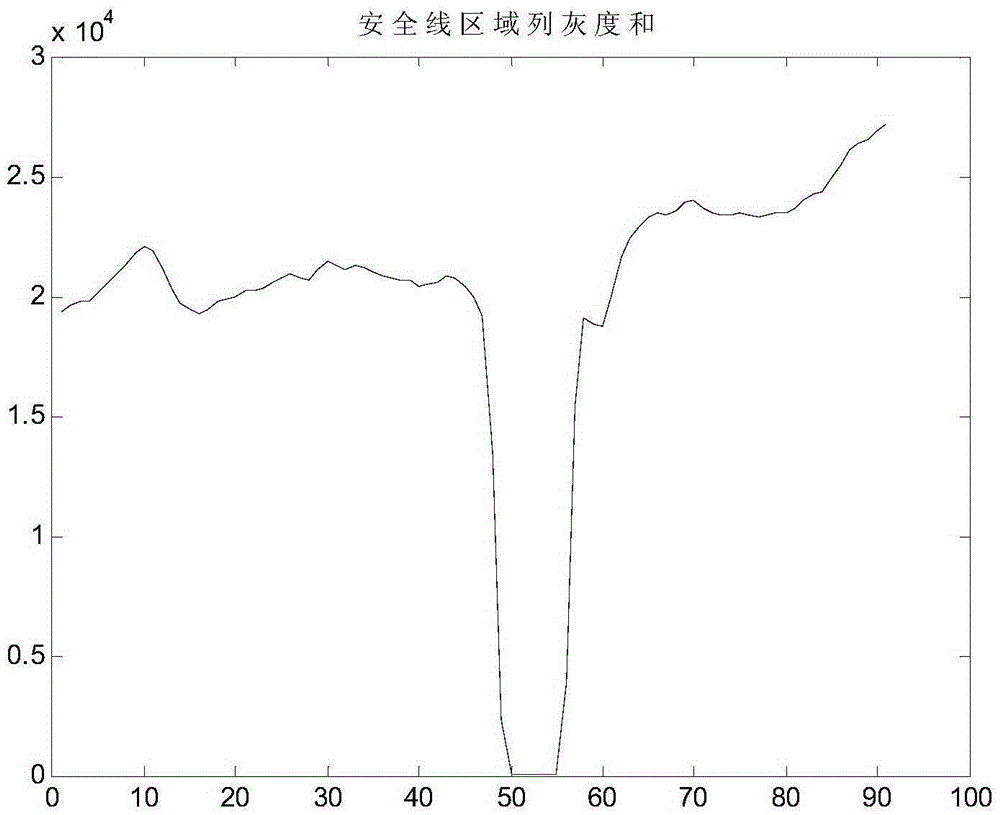
[0081] Select the BD image of the banknote to be detected, and intercept the area of the security line at a resolution of 100dpi as X[320:410], Y[1; end].
[0082] Step 102, obtaining the gray value information of the re...
Embodiment 2
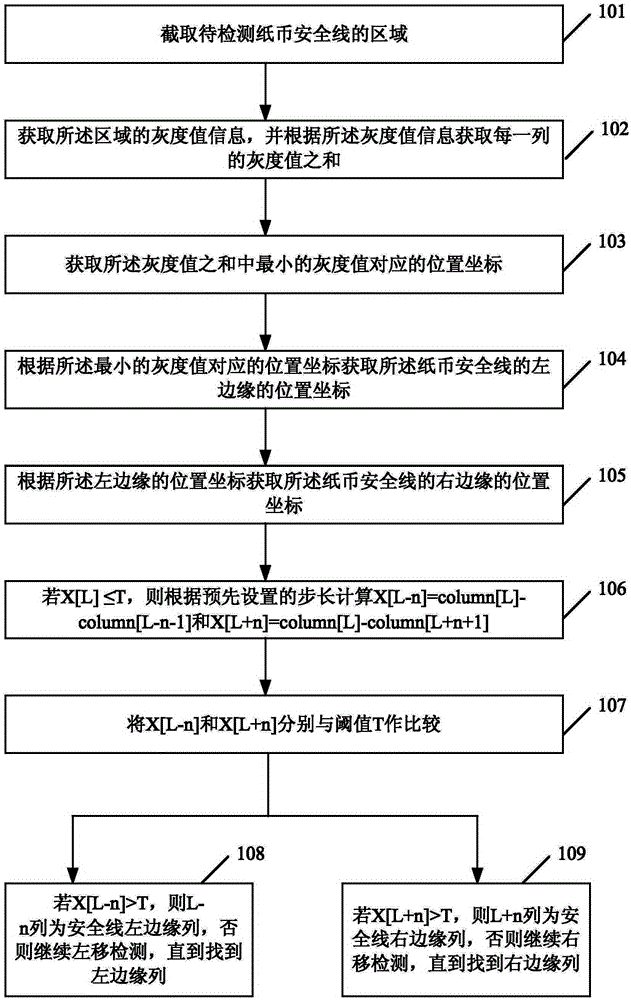
[0100] refer to image 3 , image 3 It is a schematic flow chart of a method for obtaining banknote security line boundaries according to an embodiment of the present invention.
[0101] On the basis of Embodiment 1, the method for obtaining the banknote security line boundary further includes:
[0102] Step 106, if X[L]≤T, then calculate X[L-n]=column[L]-column[L-n-1] and X[L+n]=column[L]-column[ L+n+1];
[0103] Step 107, comparing X[L-n] and X[L+n] with threshold T respectively;
[0104] Step 108, if X[L-n]>T, then the L-n column is the left edge column of the security line, otherwise continue to move left and detect until the left edge column is found;
[0105] Step 109, if X[L+n]>T, then the column L+n is the right edge column of the safety line, otherwise continue to move right and detect until the right edge column is found.
[0106] Specifically, if X[L]T, then L-1 is the left edge column of the safety line, otherwise continue to move to the left until Find the l...
Embodiment 3
[0108] refer to Figure 4 , Figure 4 It is a schematic flow chart of a method for obtaining banknote security line boundaries according to an embodiment of the present invention.
[0109] On the basis of embodiment one or embodiment two, on the basis of embodiment one, the method also includes:
[0110] Step 110, obtaining the width W=L2-L1-2 of the security line according to the position coordinates of the left and right edges of the security line, where L1 is the left edge of the security line, and L2 is the right edge of the security line;
[0111] Step 111, comparing the width W with the security thread width range of normal banknotes;
[0112] Step 112, if the W is within the width range of the security thread of the normal banknote, then determine that the security thread is normal;
[0113] Step 113, if the W is outside the width range of the security thread of the normal banknote, it is determined that the security thread is abnormal.
[0114] Specifically, compar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com