LDDoS attack time synchronization and flow convergence method based on cross correlation
A technology of time synchronization and traffic aggregation, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of lack of actual data, staying in theory and simulation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
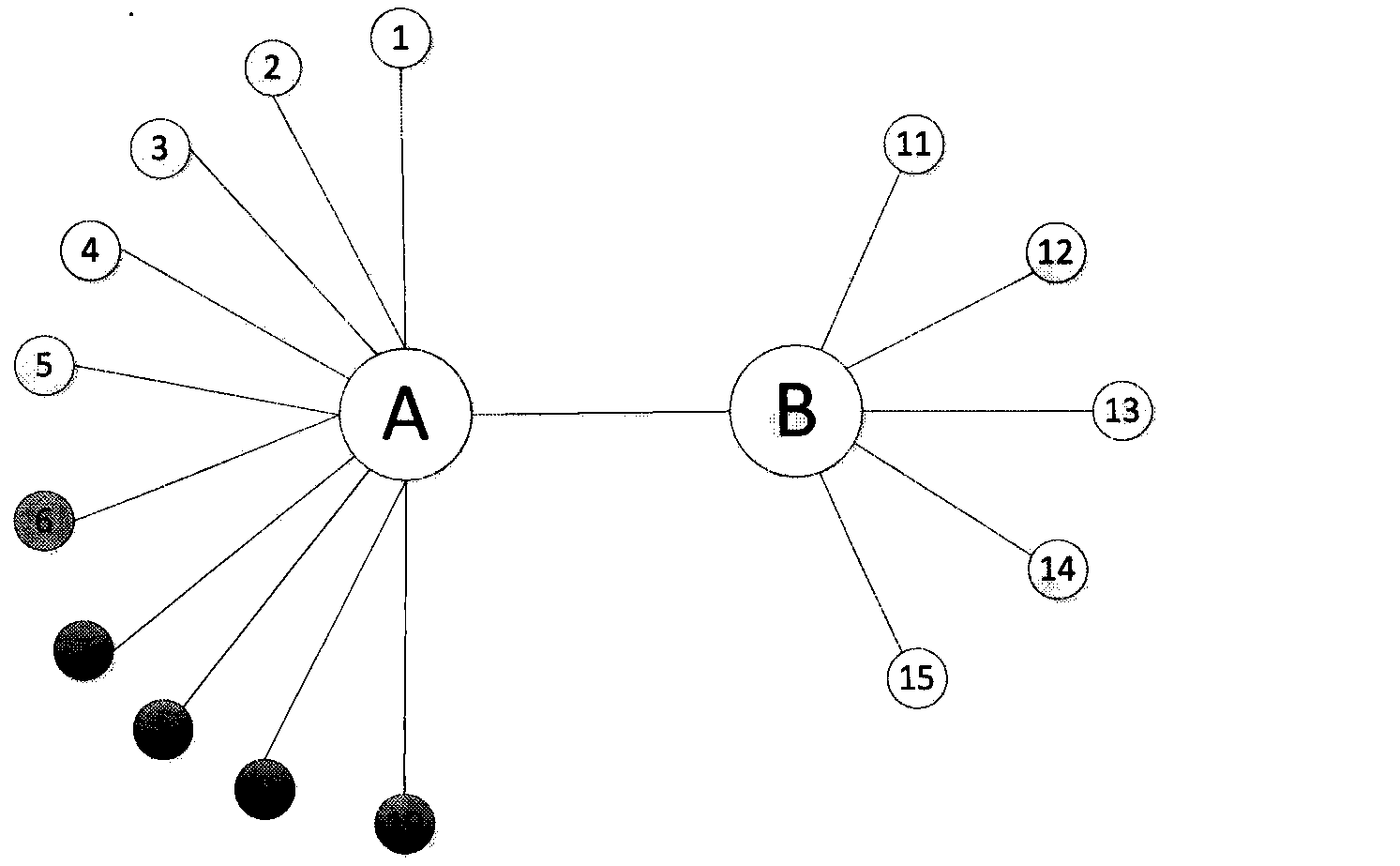
[0028] 1. In the attached image 3In the simulated LDDoS scenario, there are two routers A and B, 5 legitimate TCP senders (nodes 1-5), 5 attackers (nodes 6-10), and 5 TCP receivers (nodes 11-15) . The bandwidth of the bottleneck link between routers A and B is 10Mbps. The detailed parameters are shown in the table below:
[0029]
RTT(ms)
Bandwidth (Mb)
Node 1 to A
10
100
Node 2 to A
50
100
Node 3 to A
100
100
Node 4 to A
150
100
Node 5 to A
200
100
Nodes 6-10 to A
5
100
Node A to B
50
20
Node B to 11
10
100
Node B to 12
50
100
Node B to 13
100
100
Node B to 14
150
100
Node B to 15
200
100
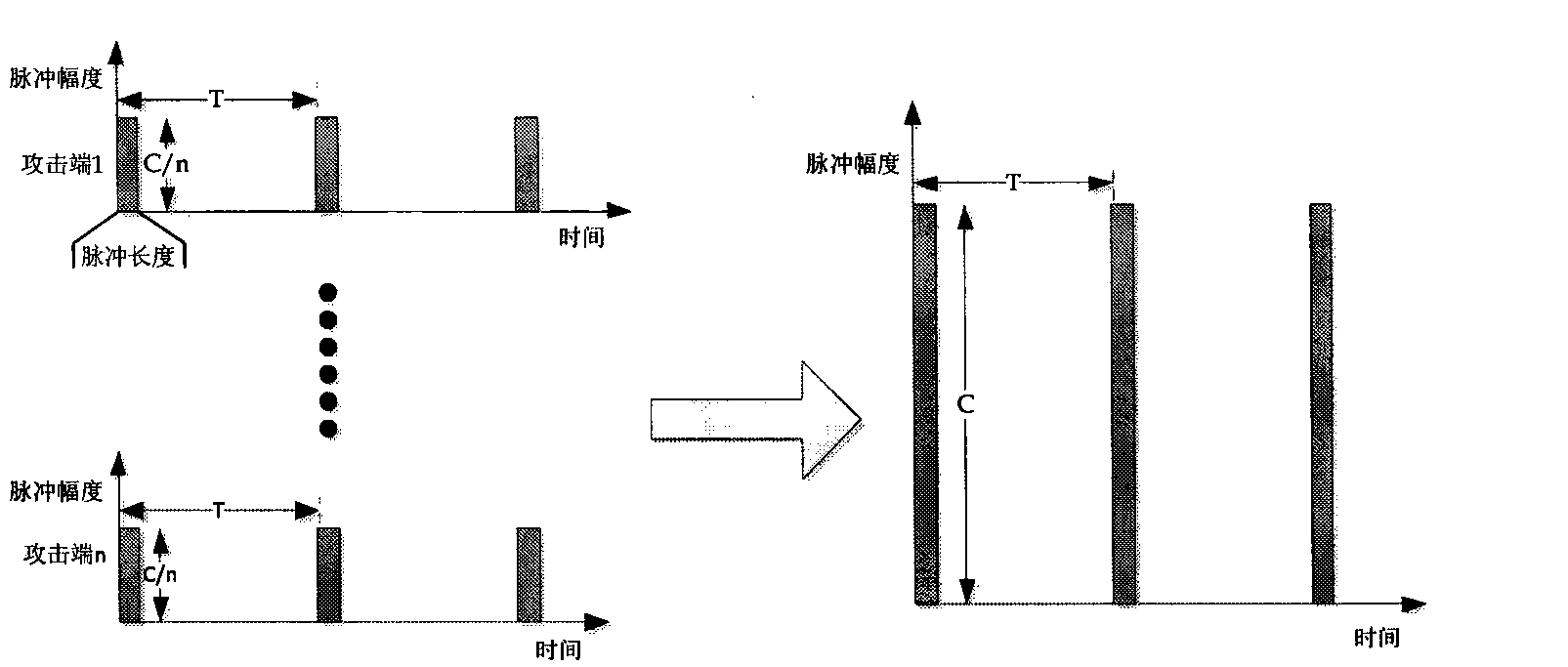
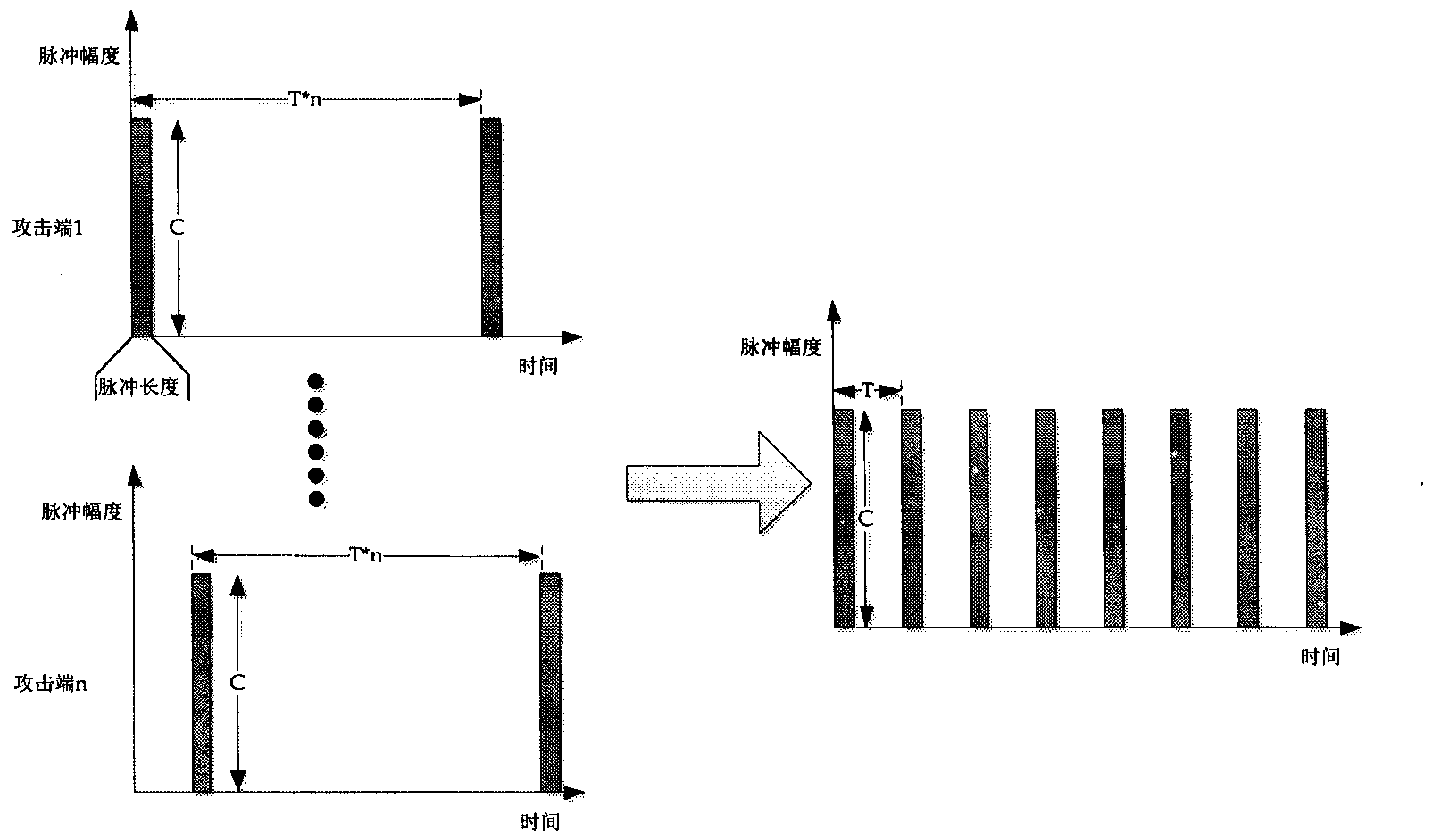
[0030] Here we select the attack parameters of pulse period T=1000ms, pulse length L=250ms, and pulse amplitude R=20Mb as the finally converged waveform of the multi-source LDDoS attac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com