Two-dimensional dynamic contact inquiry list inquiring method and system based on double-hash structure
A technology of hash list and query method, which is applied in special data processing applications, instruments, electrical digital data processing, etc. It can solve the problems of reducing and occupying the retrieval speed of contact data, and achieves improved access efficiency, low system overhead, and achieve simple effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] This embodiment provides a method for querying a two-dimensional dynamic contact query list based on a double-hash structure. The method for querying a two-dimensional dynamic contact query list based on a double-hash structure is performed in a mobile terminal environment, and the method is executed. Mobile terminals include mobile phones, PDAs, and the like. see figure 1 , which is shown as the flow of the two-dimensional dynamic contact query method based on the double hash structure, including:
[0037] S1, constructing a contact query hash list, and storing the constructed contact query hash list in the buffer pool of the mobile terminal; the contact query hash list is composed of multiple two-dimensional tables, and multiple two-dimensional tables Stored in order of contact name. Each two-dimensional table is composed of multiple records, fields, record attributes, field attributes, and data content. The records and fields in each two-dimensional table are stored...
Embodiment 2
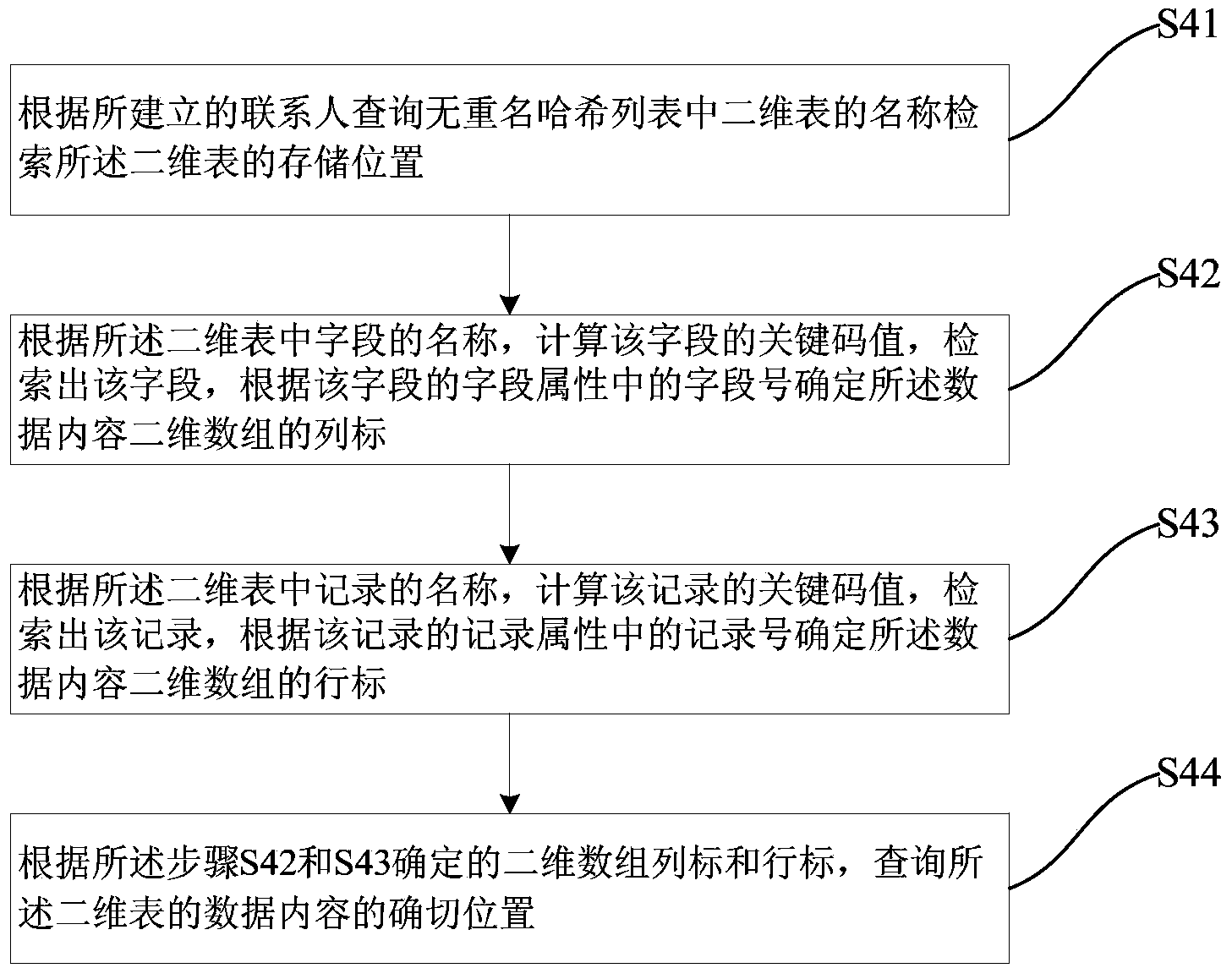
[0080] This embodiment provides a two-dimensional dynamic contact query list query system based on a double hash structure, and the two-dimensional dynamic contact query list query system based on a double hash structure is included in a mobile terminal. see Figure 4 , showing the principle structure of a two-dimensional dynamic contact query list query system based on a double hash structure, including: a list generation module 1, a storage module 2, an operation module 3, a monitoring module 4, a first query module 5, and a second query module 6.
[0081] The list generating module 1 is configured to construct a contact query hash list; the contact query hash list includes a contact query duplicate name hash list and a contact query non-duplicate name hash list. The storage module 2 connected with the list generation module 1 is used for storing the constructed contact query hash list in the buffer pool of the mobile terminal. The computing module 3 connected to the stora...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com