An opportunistic network routing method and system based on encrypted fuzzy keywords
A keyword and routing technology, applied in the field of information science, can solve problems such as reducing user interaction in opportunistic networks, lack of clear goals, and obtaining routing information, and achieves the effect of tolerating intermittent connections, protecting user privacy, and improving diffusion rates.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
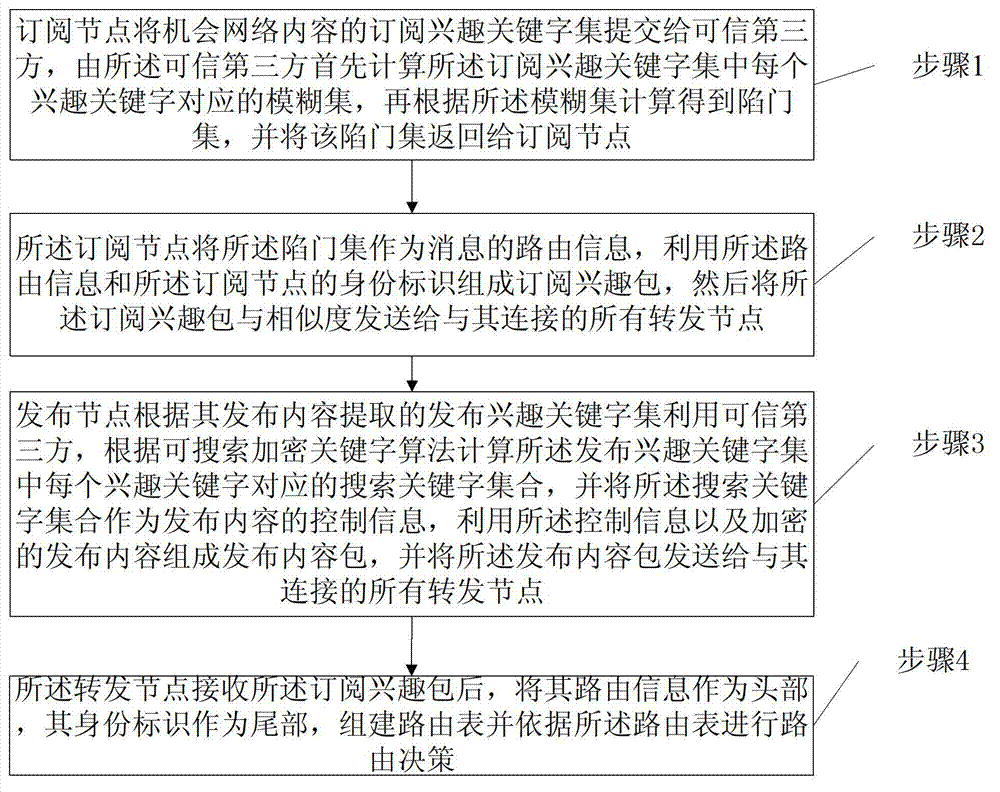
[0043] figure 1 It is a flowchart of an opportunistic network routing method based on encrypted fuzzy keywords in the present invention. Such as figure 1 As shown, the method includes:
[0044] Step 1, the subscribing node submits the subscription interest keyword set of opportunistic network content to a trusted third party, and the trusted third party first calculates the fuzzy set corresponding to each interest keyword in the subscription interest keyword set, and then according to The fuzzy set is calculated to obtain a trapdoor set, and the trapdoor set is returned to the subscribing node;
[0045] Step 2, the subscribing node uses the trapdoor set as the routing information of the message, uses the routing information and the identity of the subscribing node to form a subscription interest packet, and then sends the subscription interest packet and similarity to its All forwarding nodes connected;
[0046] Step 3, using the trusted third party to calculate the search...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com