Method for realizing client login through intelligent terminal, server and intelligent terminal
An intelligent terminal, a technology for controlling intelligent terminals, applied in telephone communication, user identity/authority verification, electrical components, etc., can solve the problems of cumbersome operation and inconvenient user operation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
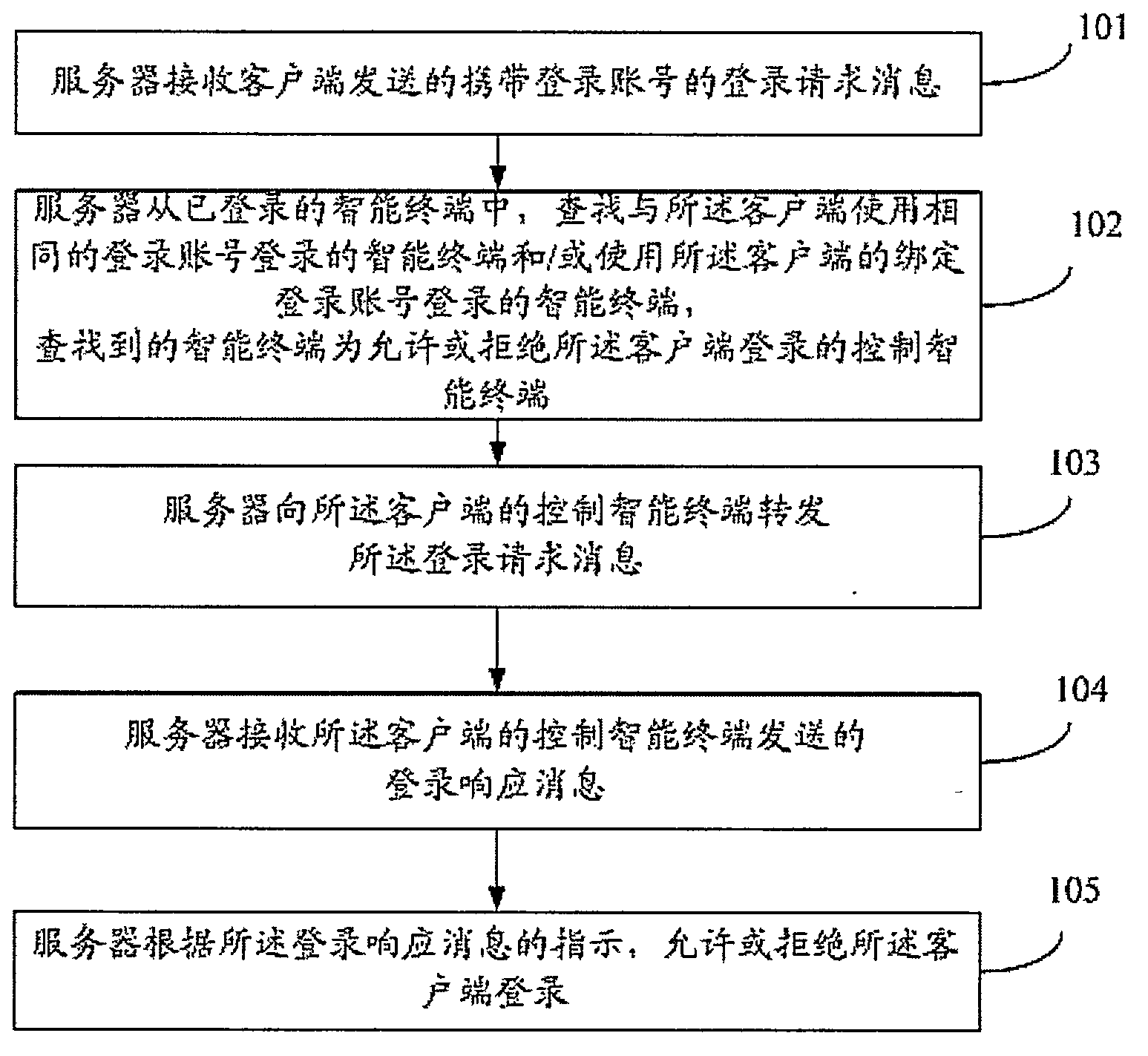
[0124] The first embodiment aims to describe the login process of the client from the perspective of the server side. see figure 1 , which is a flowchart of a method for implementing client login through an intelligent terminal disclosed in Embodiment 1 of the present invention, and the method includes the following steps:
[0125] Step 101: the server receives a login request message that carries a login account and is sent by the client;
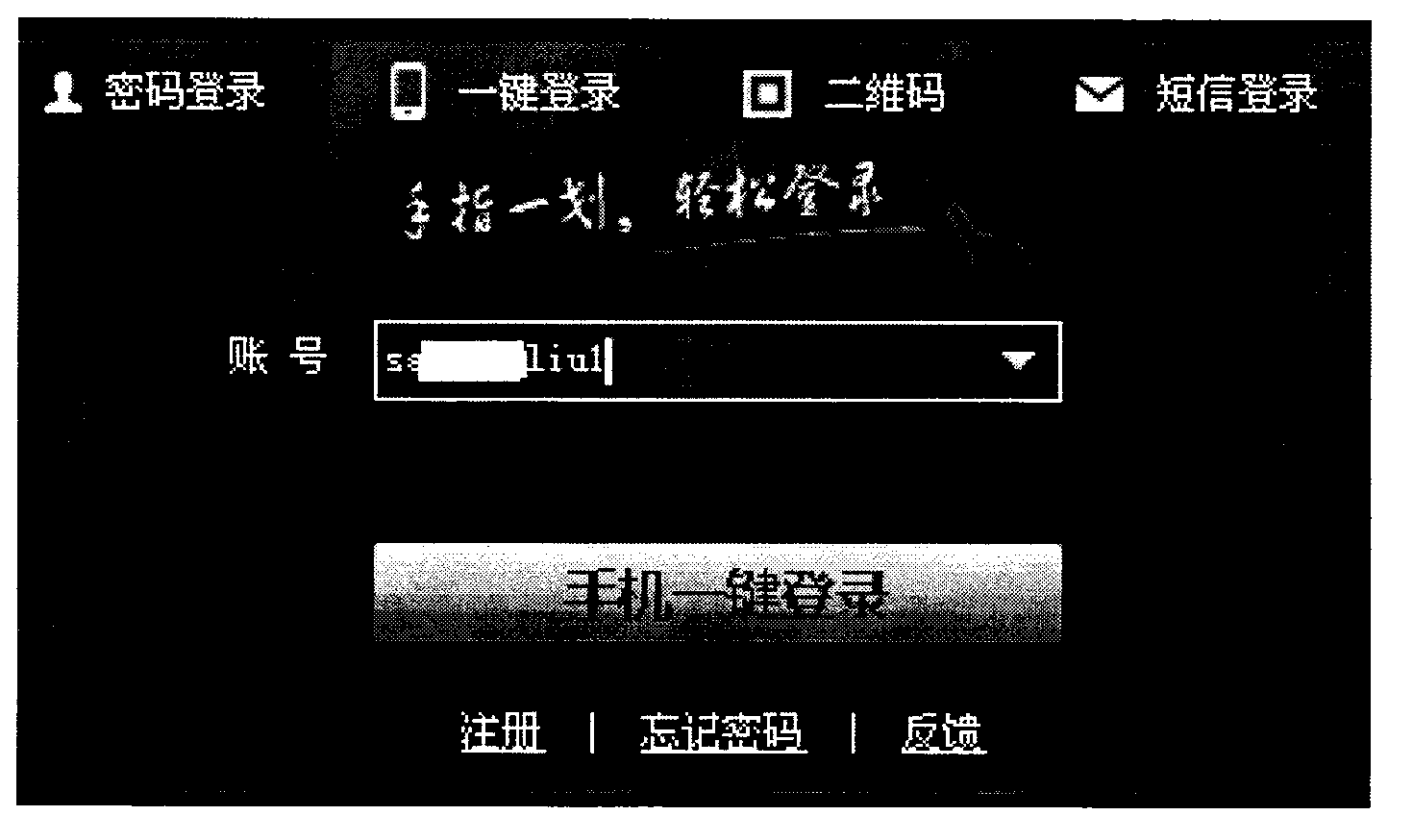
[0126]In order to facilitate the description and understanding of the technical solution of the present invention, all steps in this embodiment are based on a specific application scenario. For example, client A needs to log in to server B that provides a certain application service, such as figure 2 As shown, when the user enters a login account sa******liu1 into client A, and clicks the "Mobile One-Key Login" button, client A will send a login request message carrying sa******liu1 to server B.
[0127] Step 102: From the logged-in sm...
Embodiment 2
[0142] The difference between this embodiment and Embodiment 1 is that after the client successfully logs in, the smart terminal can also log out the logged-in client according to the needs of the user. see Figure 4 , which is a flowchart of a method for realizing client login through a smart terminal disclosed in Embodiment 2 of the present invention, including the following steps:
[0143] Step 401: the server receives the login request message carrying the login account sent by the client;
[0144] Step 402: From the logged-in smart terminals, the server searches for smart terminals logged in with the same login account as the client and / or smart terminals logged in with the client's bound login account, and the found smart terminals are A control smart terminal that allows or denies the client to log in;
[0145] Step 403: the server forwards the login request message to the controlling intelligent terminal of the client;
[0146] Step 404: The server allows or rejects...
Embodiment 3
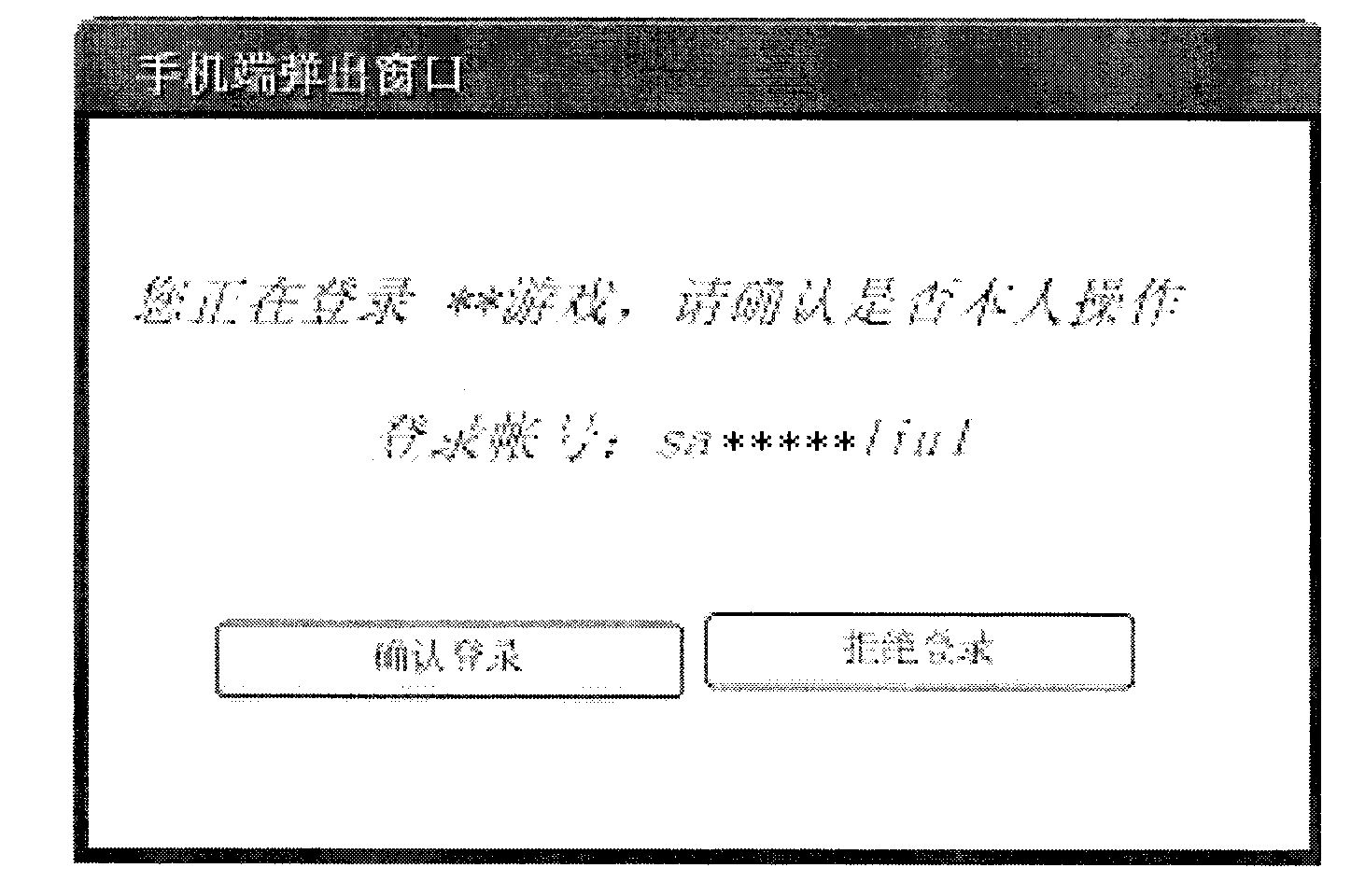
[0166] The difference between this embodiment and the first embodiment is that the server further randomly generates a verification code, sends the verification code to the client, and also sends a login request message carrying the verification code to the control intelligent terminal of the client. see Figure 5 , which is a flowchart of a method for implementing client login through an intelligent terminal disclosed in Embodiment 3 of the present invention, including the following steps:
[0167] Step 501: the server receives a login request message carrying a login account sent by the client;
[0168] Step 502: The server searches for the smart terminal logged in with the same login account as the client and / or the smart terminal logged in with the bound login account of the client from the logged in smart terminals, and the found smart terminal is: Allowing or denying the control intelligent terminal that the client logs in;
[0169] Step 503: The server randomly genera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com