Anti-theft protection method for mobile terminal
A mobile terminal and screen technology, applied in the direction of digital data protection, internal/peripheral computer component protection, etc., can solve the problem of insufficient protection security and achieve good anti-theft protection effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
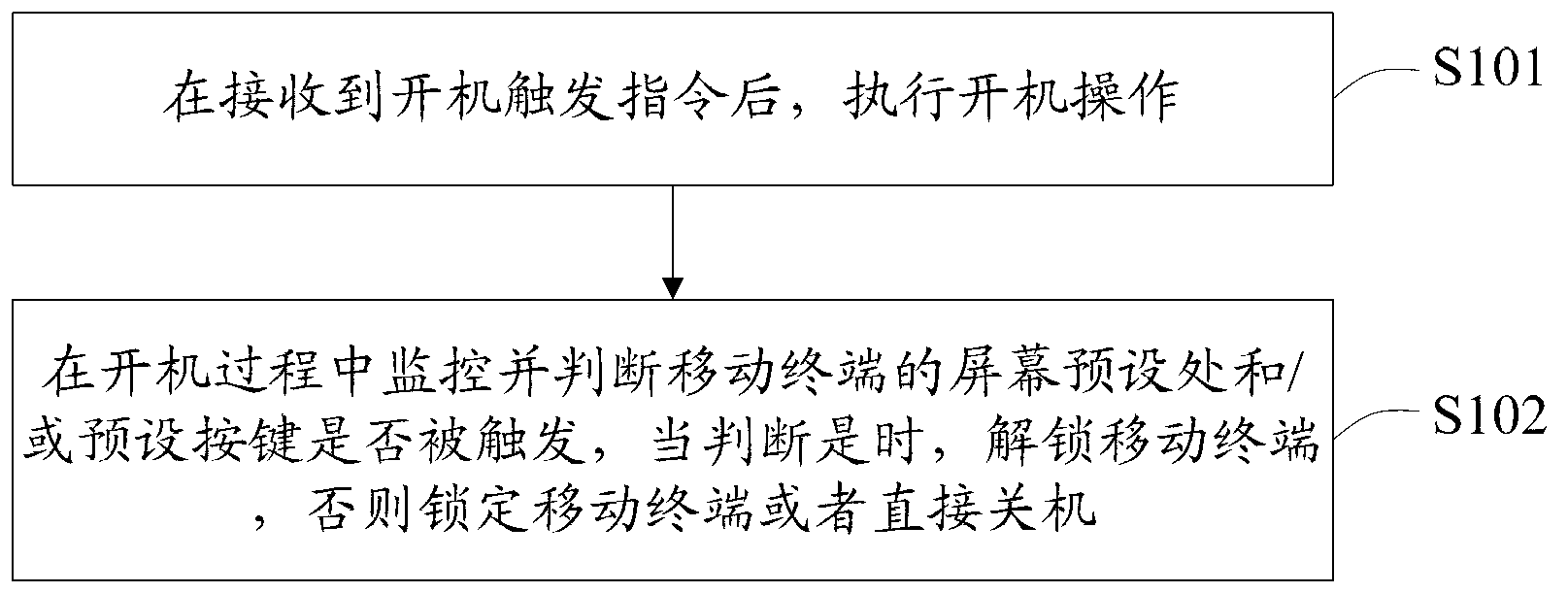
[0018] figure 1 The flow of the anti-theft protection method for a mobile terminal provided by the first embodiment of the present invention is shown, and only the parts related to the embodiment of the present invention are shown for convenience of description.
[0019] The mobile terminal anti-theft protection method provided in this embodiment includes the following steps:
[0020] Step S101 , after receiving a power-on trigger instruction, perform a power-on operation.
[0021] In the embodiment of the present invention, as long as the judgment and verification of the user's operation action is completed during the boot process, the mobile terminal is unlocked when the requirements are met, and the mobile terminal operation interface is normally entered. Therefore, the user first needs to turn on the mobile terminal in the shutdown state. After the power switch on the mobile terminal is triggered, a start-up trigger command is generated, and the start-up process begins at...
Embodiment 2
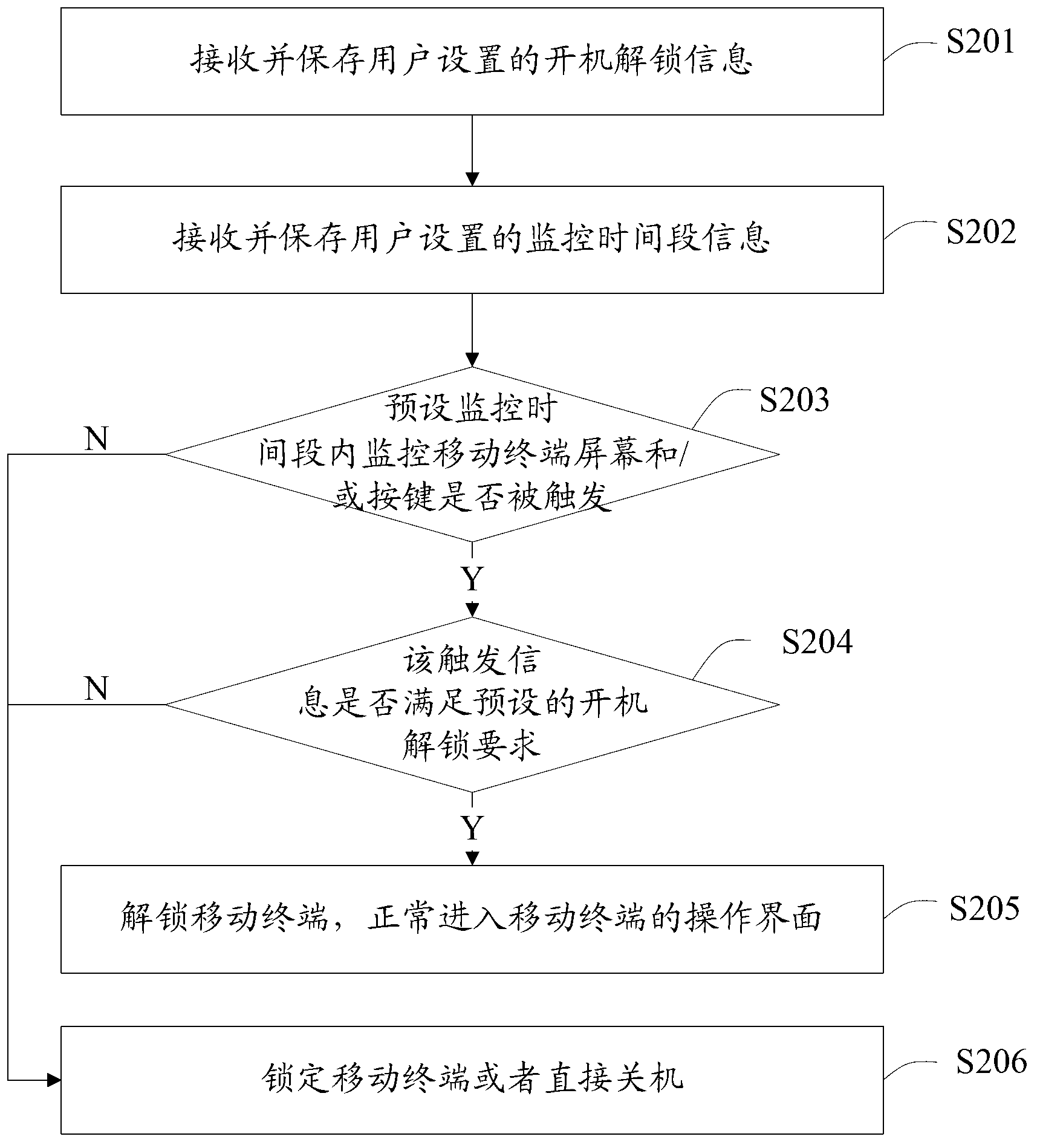
[0025] figure 2 The flow of the mobile terminal anti-theft protection method provided by the embodiment of the present invention is shown, and only the parts related to the embodiment of the present invention are shown for convenience of description.
[0026] The mobile terminal anti-theft protection method provided in this embodiment includes the following steps:
[0027] Step S201, receiving and saving the power-on unlocking information set by the user;
[0028] Step S202, receiving and saving the monitoring time period information set by the user.
[0029] In this embodiment, the user can set the power-on unlocking information and monitoring period information by himself. Only when the preset unlocking operation is completed within the monitoring time period can the unlocking be completed and the system can be entered normally. For example, it can be set to 10 minutes after power-on within seconds. The power-on unlock information is the data information corresponding to...
Embodiment 3
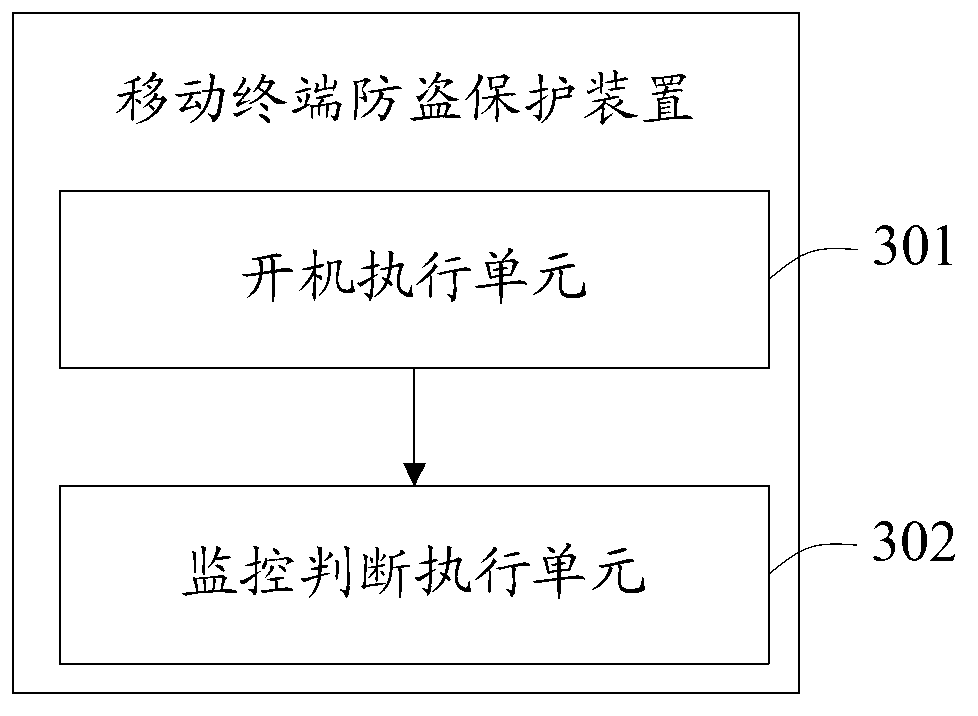
[0038] image 3 The structure of the mobile terminal anti-theft protection device provided by the embodiment of the present invention is shown, and only the parts related to the embodiment of the present invention are shown for convenience of description.
[0039] The mobile terminal anti-theft protection device provided in this embodiment includes:
[0040] The power-on execution unit 301 is configured to perform a power-on operation after receiving a power-on trigger instruction;
[0041] The monitoring and judging execution unit 302 is used to monitor and judge whether the screen preset and / or the preset button of the mobile terminal is triggered during the boot process, and if it is judged to be yes, unlock the mobile terminal, otherwise lock the mobile terminal or directly shut down.
[0042]Each functional unit 301, 302 provided in this embodiment correspondingly realizes steps S101, S102 in the first embodiment. Specifically, the boot execution unit 301 executes the bo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com