Process protection method
A process and process list technology, applied in the field of computer security, can solve problems such as increasing complexity and increasing system resource consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The specific implementation manners of the present invention will be described in further detail below in conjunction with the accompanying drawings and examples. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
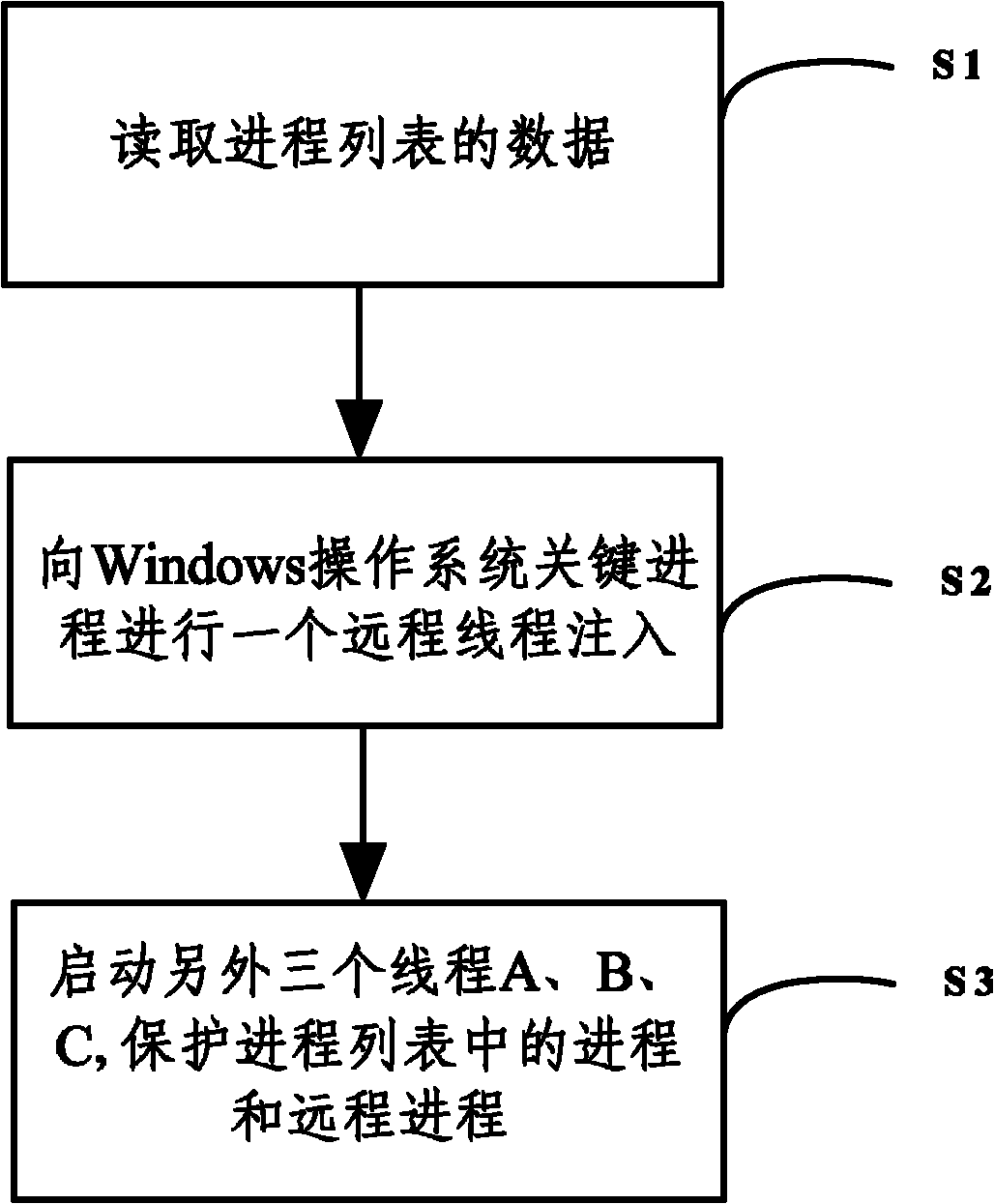
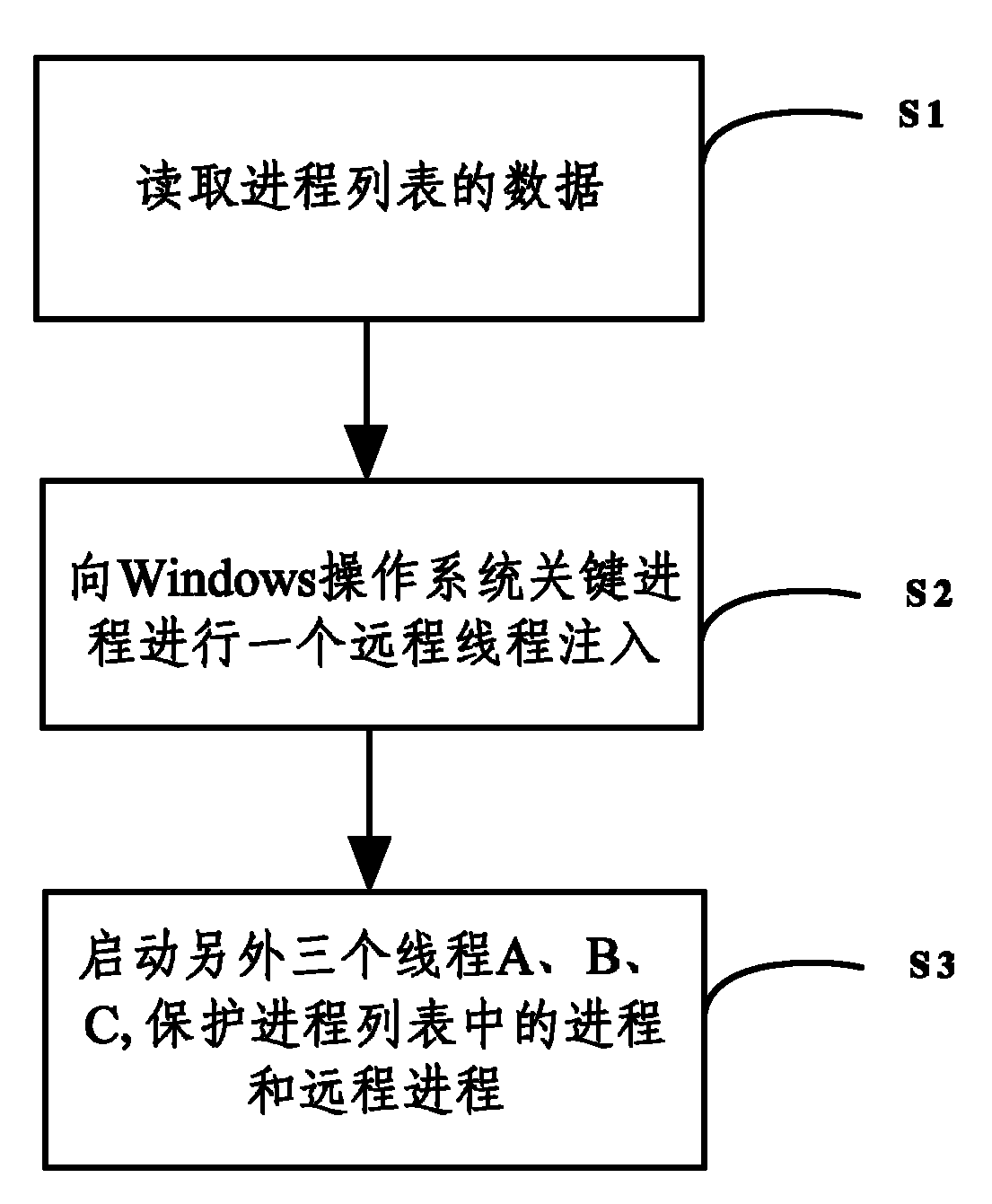
[0018] Such as figure 1 Shown, method of the present invention comprises the following steps:
[0019] S0, create the list of user processes (comprising ordinary processes and service processes) that need to be protected, this list can be freely configured by the user; service process refers to the process of running in Windows service form, such as Windows firewall service, its process name is svchost.exe ; A process that does not run as a Windows service is a normal process, such as notepad.exe.
[0020] S1. Read the data of the process list;
[0021] S2. Injecting a remote thread into a key process of the Windows operating system.
[0022] S3. Start three threads, whic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com