Integration IP message security reinforcement method and system
A security and message technology, applied in messages/mailboxes/notifications, electrical components, wireless communications, etc., can solve problems such as inability to effectively protect personal sensitive information, personal communication content being disseminated without consent, and improve user experience Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
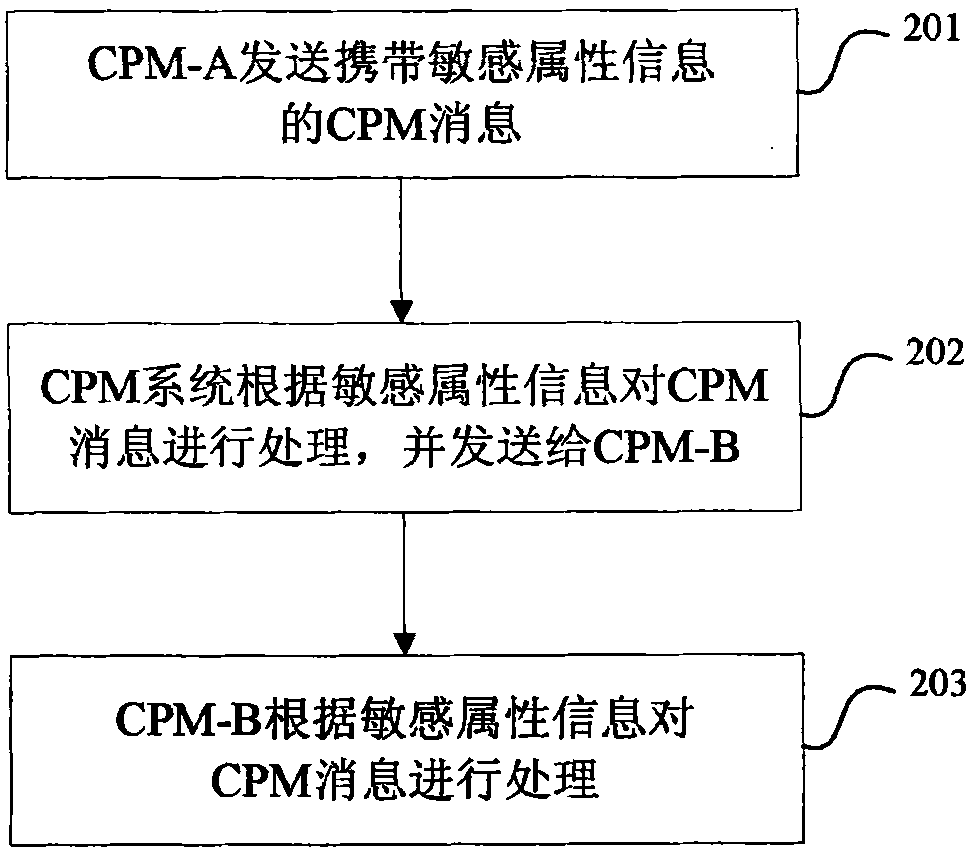
[0088] figure 2 It is a flow chart of the method for enhancing the security of converged IP messages in the first embodiment of the present invention. This embodiment describes that the sender CPM terminal sets sensitive attribute information in the CPM message sent by it, and the CPM system and the receiver CPM terminal set sensitive attribute information according to the sensitive attribute information. The information processes the CPM message accordingly.
[0089] In this embodiment, user A uses the CPM address Addr-A as the sender address to send a CPM message, the CPM client currently used by user A is CPM client A (referred to as CPM-A), and the CPM Participating Function to which Addr-A belongs It is CPM Participating Function-A; the recipient of the above CPM message is user B, the recipient's CPM address is Addr-B, the CPM client currently used by user B is CPM client B (denoted as CPM-B), Addr-B The attributable CPMParticipating Function is CPM Participating Funct...
no. 2 example
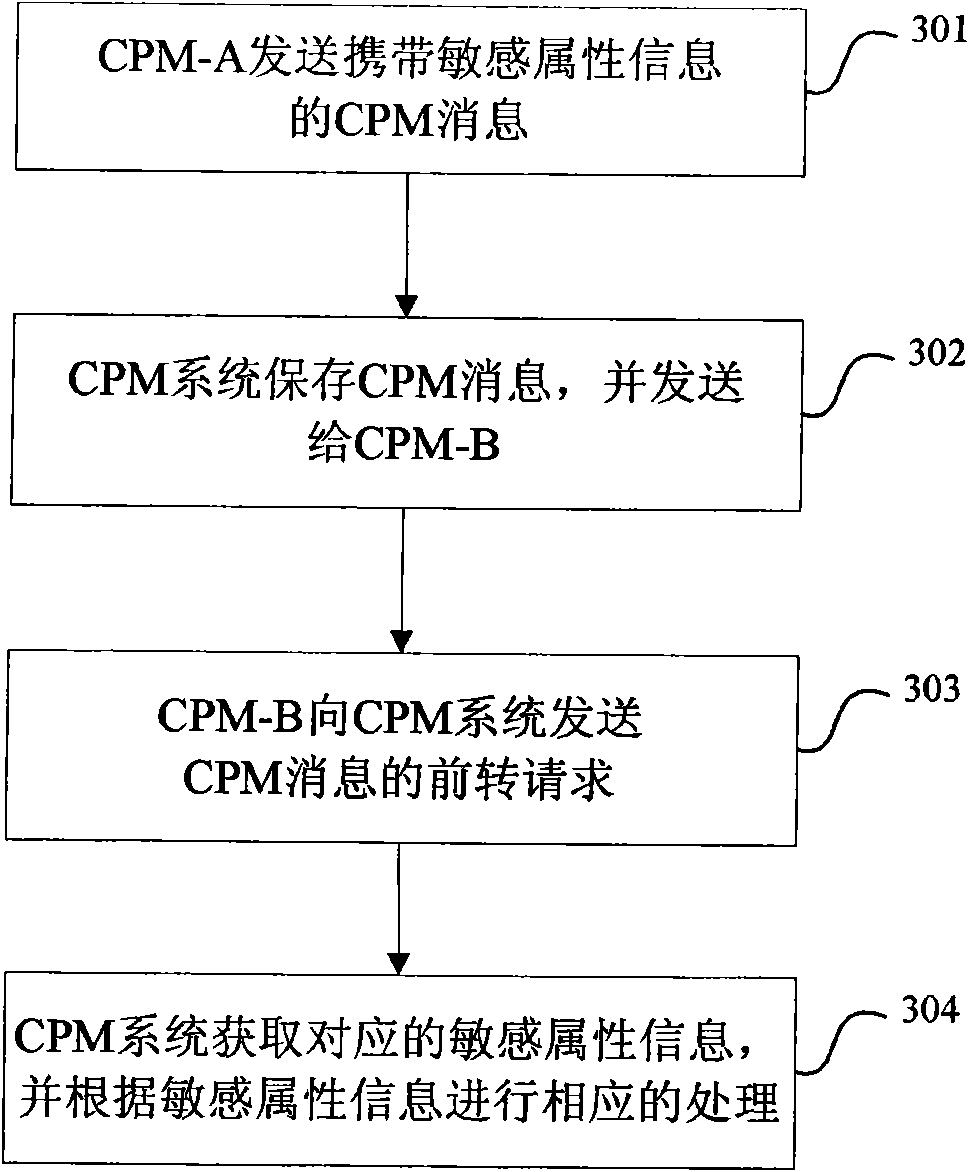
[0123] image 3 It is a flow chart of the method for enhancing the security of converged IP messages in the second embodiment of the present invention. This embodiment describes the process in which the CPM system performs corresponding processing according to the sensitive attribute information of the CPM message after receiving the forwarding request of the CPM message.
[0124] In this embodiment, user A uses the CPM address Addr-A as the sender address to send a CPM message, the CPM client currently used by user A is CPM client A (referred to as CPM-A), and the CPM Participating Function to which Addr-A belongs It is CPM Participating Function-A; the recipient of the above CPM message is user B, the recipient's CPM address is Addr-B, the CPM client currently used by user B is CPM client B (denoted as CPM-B), Addr-B The attributable CPMParticipating Function is CPM Participating Function-B; after user B receives the CPM message, the method includes the following steps:
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com