Incoming call confidentiality method, system and mobile communication terminal
A security method and security system technology, applied in the field of mobile communication terminals, can solve the problems of low security and easy leakage of incoming call numbers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0023] see figure 1 , is the implementation flow of the incoming call privacy method provided by the first embodiment of the present invention, which includes the following steps:
[0024] In step S101, when there is an incoming call, extract the incoming call number;
[0025] In step S102, part of the numbers in the extracted caller number are replaced with symbols other than Arabic numerals;
[0026] Wherein, preferably, the symbols other than the Arabic numerals may be any combination of one or more of asterisk "*", English letters, punctuation marks, or unit symbols and the like.
[0027] In another preference, the digits of part of the numbers in the caller number may be the last four digits of the caller number, the middle four digits of the caller number, or the first 6 digits of the caller number, etc. It can be understood that the number of digits of some numbers in the caller number can be set by the user.
[0028] In step S103, display the caller number in which ...
Embodiment 2
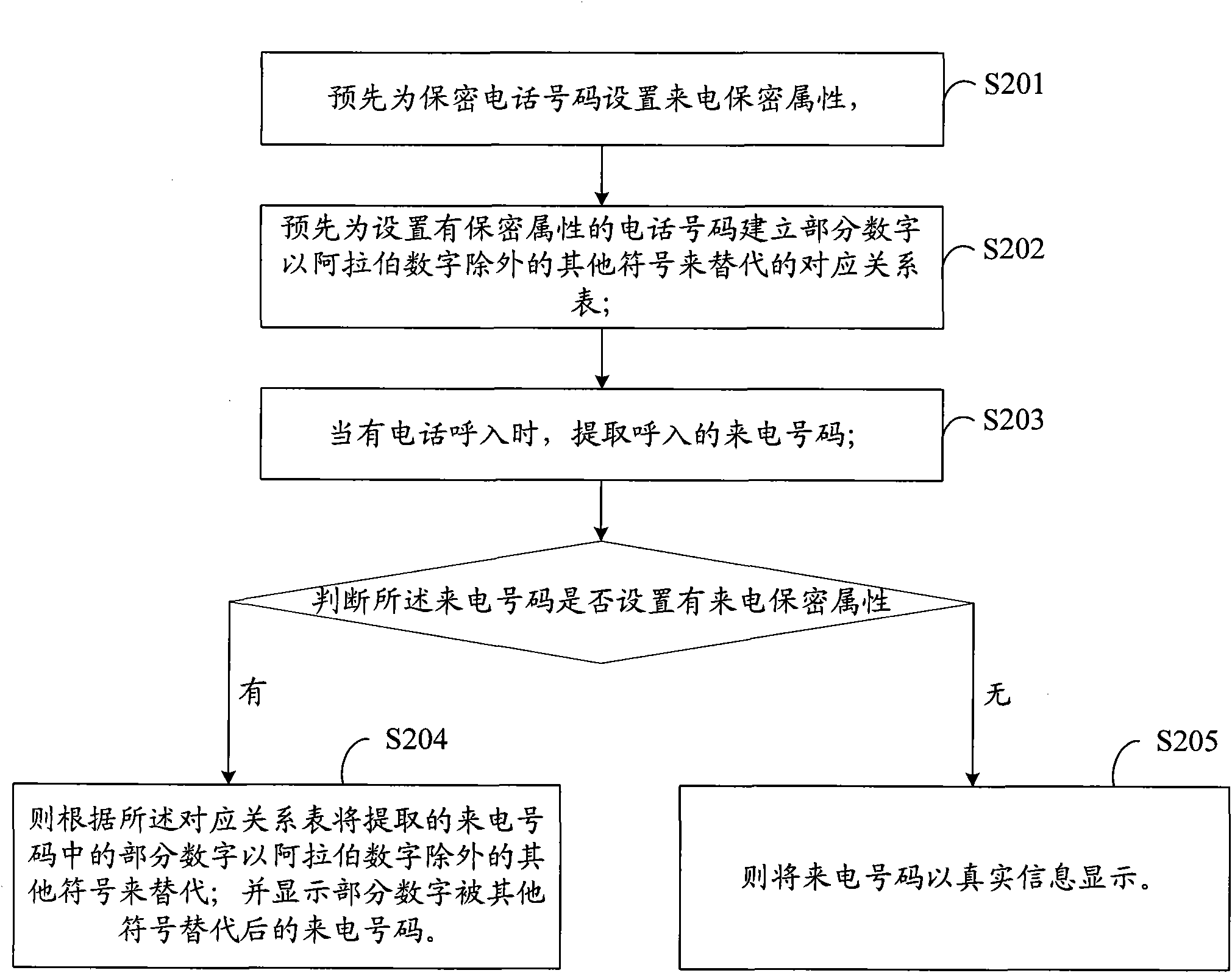
[0031] see figure 2 , is the implementation flow of the incoming call privacy method provided in the second embodiment of the present invention, which includes the following steps:
[0032] In step S201, the confidentiality attribute of the incoming call is set for the confidential telephone number in advance, and the confidentiality attribute of the incoming call is: a confidentiality attribute in which part of the numbers in the telephone number are replaced by symbols other than Arabic numerals;
[0033] In step S202, a correspondence table in which some numbers are replaced by symbols other than Arabic numerals is established in advance for telephone numbers with confidentiality attributes;
[0034] In step S203, when there is an incoming call, extract the incoming call number;
[0035] In step S204, it is judged whether the caller number is provided with the caller confidentiality attribute, and if the caller’s confidentiality attribute is set, then according to the cor...
Embodiment 3
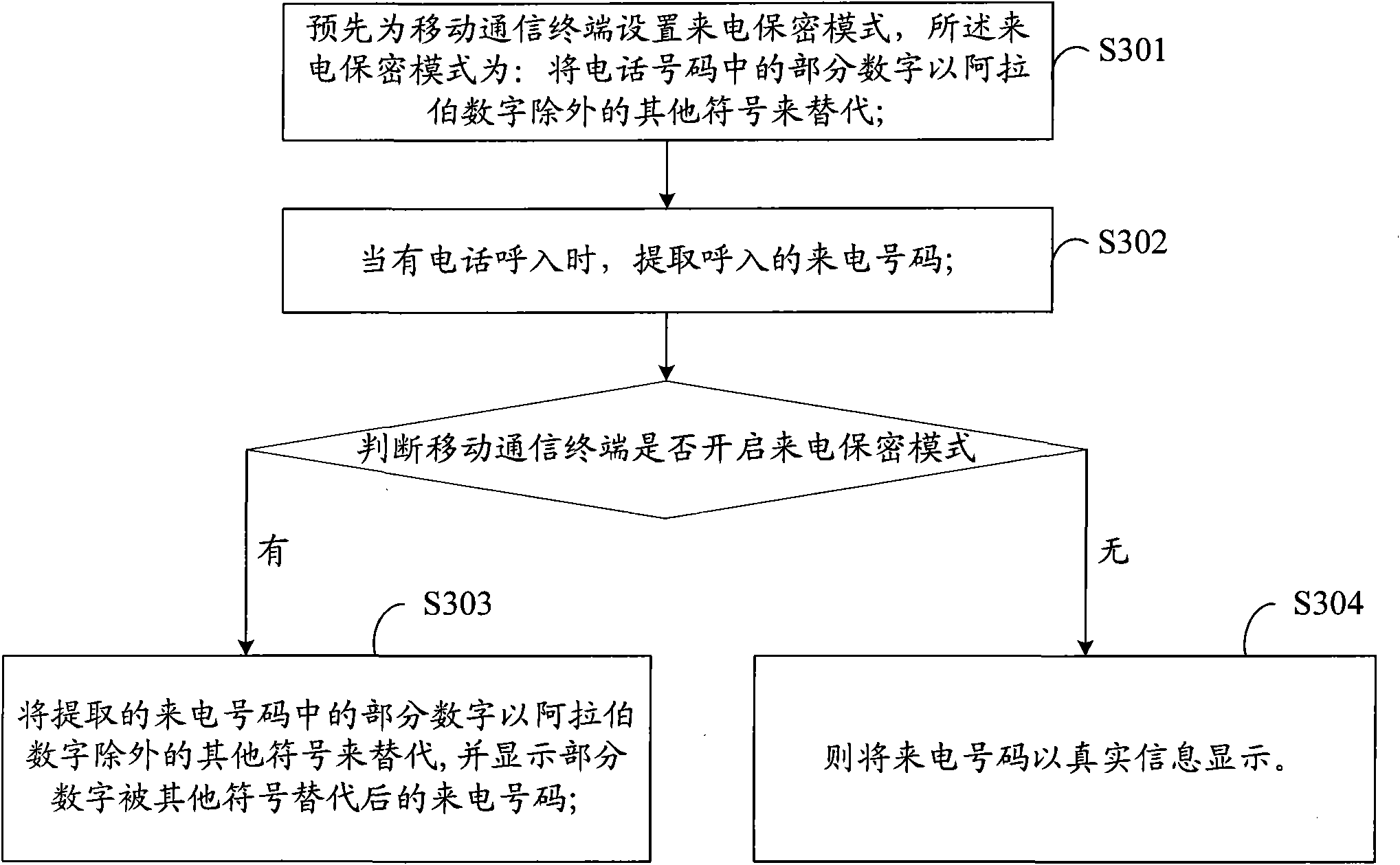
[0041] see image 3 , is the implementation flow of the incoming call privacy method provided by the third embodiment of the present invention, which includes the following steps:
[0042] In step S301, the incoming call security mode is set for the mobile communication terminal in advance, and the incoming call security mode is: replacing part of the numbers in the phone number with symbols other than Arabic numerals;
[0043] In step S302, when there is an incoming call, extract the incoming call number;
[0044] In step S303, it is judged whether the mobile communication terminal has turned on the incoming call privacy mode, if the incoming call privacy mode is turned on, then part of the digits in the extracted incoming call number will be replaced by symbols other than Arabic numerals, and the display will show that part of the numbers are replaced by other symbols caller number;
[0045] In step S304, if the incoming call privacy mode is not turned on, the incoming cal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com