Safety control method and exchanger
A security control and security processing technology, applied in the field of communications, can solve the problems of reducing security control effect, occupying global resources, limited capacity of network interface usage policies, etc., so as to improve security control effect, save global resources, improve manageability and The effect of update speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
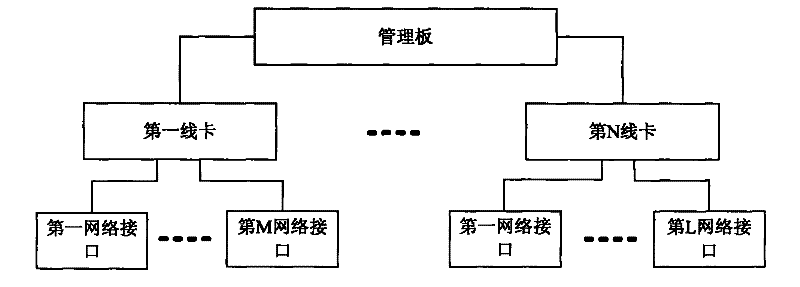
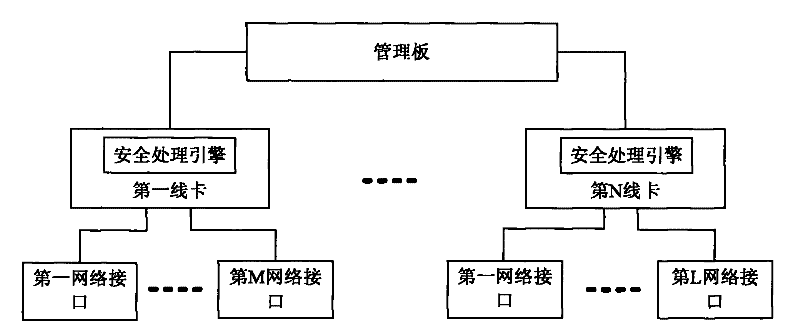
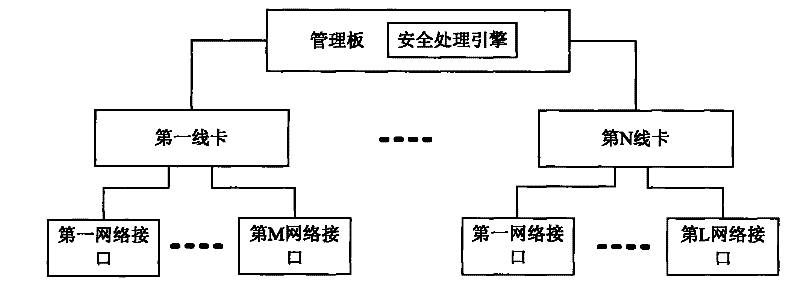
[0033] In the embodiment of the present invention, the first security processing engine is set on the line card, and the interface security processing policy is deployed therein, thereby realizing the first filtering of data packets, and the second security processing engine is set on the management board, and Deploy the global security processing strategy in it, based on which the secondary filtering of data packets is realized, the storage capacity of the security processing strategy on the line card and the switch is reasonably utilized, and the capacity utilization rate of the security processing engine on the line card and the switch is improved. And effectively realize the security control of the data message.
[0034] Figure 4 It is a flowchart of an embodiment of the security control method of the present invention. The process of this embodiment can be implemented by a chassis-type centralized forwarding switch. Such as Figure 4 As shown, the process of this embo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com