Arc-shaped anti-fake method and arc-shaped anti-fake element
A technology of anti-counterfeiting components and arcs, which is applied in the field of anti-counterfeiting to achieve unique anti-copying, increase anti-counterfeiting and information hiding, and good anti-counterfeiting effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
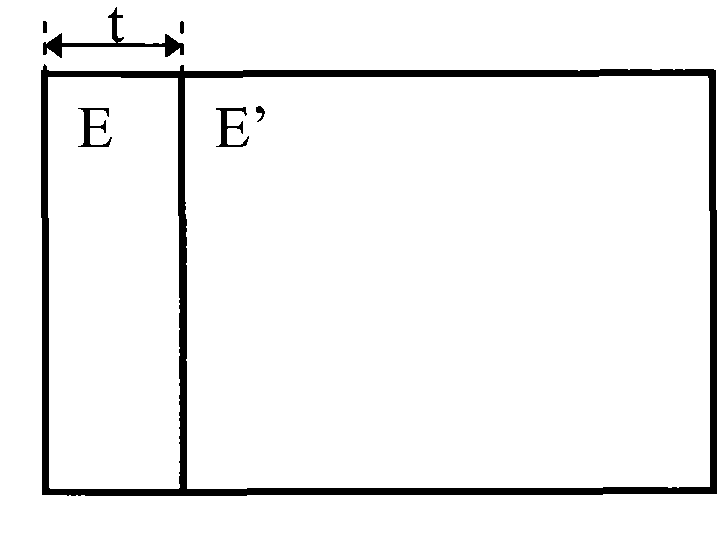
[0051] Refer below Figure 5-7 A first embodiment of the present invention is described. The first embodiment discloses a method for constructing a rectangular anti-counterfeiting icon by using the single-image visual sharing technique. Specifically, Figure 5 An original security image according to the first embodiment of the present invention is shown. Such as Figure 5 As shown, the original security image is a binary (black and white) rectangular security image S containing the letter pattern "Tsinghua", with a height of row=126, and a width of col=471. The horizontal offset and vertical offset of the target single visible encrypted image are s=12 and t=12 respectively. The following describes the use of a single visual sharing scheme according to the first embodiment of the present invention (that is, the method for recovering a secret image by using only a single sharing image (encrypted image) and its copy) according to Figure 5 The secret image S shown is generat...
no. 2 example
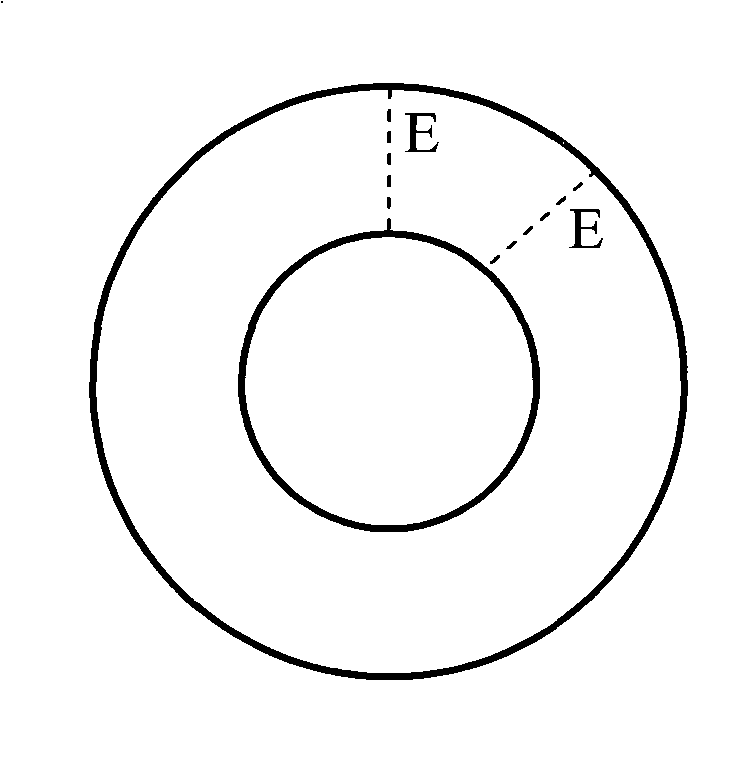
[0065] Refer below Figure 8-10 A second embodiment of the present invention is described. The second embodiment discloses a method for constructing a ring-shaped anti-counterfeiting icon by using the single-image visual sharing technology. Specifically, Figure 8 An original security image according to a second embodiment of the present invention is shown. Such as Figure 8 As shown, the original security image is a binary (black and white) rectangular security image S containing the letter pattern "Tsinghua", the height is row=76, and the width is col=338, where white pixels are represented by 0 and black pixels are represented by 1.
[0066] The steps of constructing the circular anti-counterfeit icon are as follows: First, similar to the first embodiment disclosed above, a binary rectangular encrypted icon E is constructed. Then, map the rectangular encryption icon E into a ring encryption icon (such as Figure 9 shown). Here, those skilled in the field of image proc...
no. 3 example
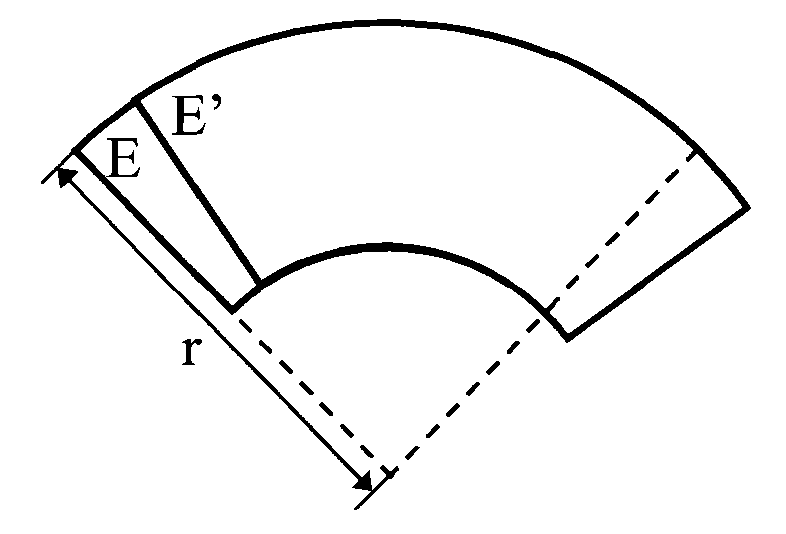
[0069] Refer below Figures 11 to 13 A third embodiment of the present invention is described. The third embodiment discloses a method for constructing an arc-shaped anti-counterfeiting icon by using the single-image visual sharing technology. Specifically, Figure 11 An original security image according to a third embodiment of the present invention is shown. Such as Figure 11 As shown, the original security image is a binary (black and white) rectangular security image S containing the letter pattern "Tsinghua", the height is row=76, and the width is col=87, where white pixels are represented by 0 and black pixels are represented by 1.
[0070] The steps of constructing an arc-shaped anti-counterfeiting icon are as follows: firstly, similar to the aforementioned second embodiment, a binary rectangular encrypted icon E is constructed. Then, utilize any known image processing software to map the encrypted icon E into an arc, and make two identical transparent sheets E and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com