Cipher key updating method and device under active state
A key update and state technology, applied in the field of communication, can solve problems such as not involving new keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 3
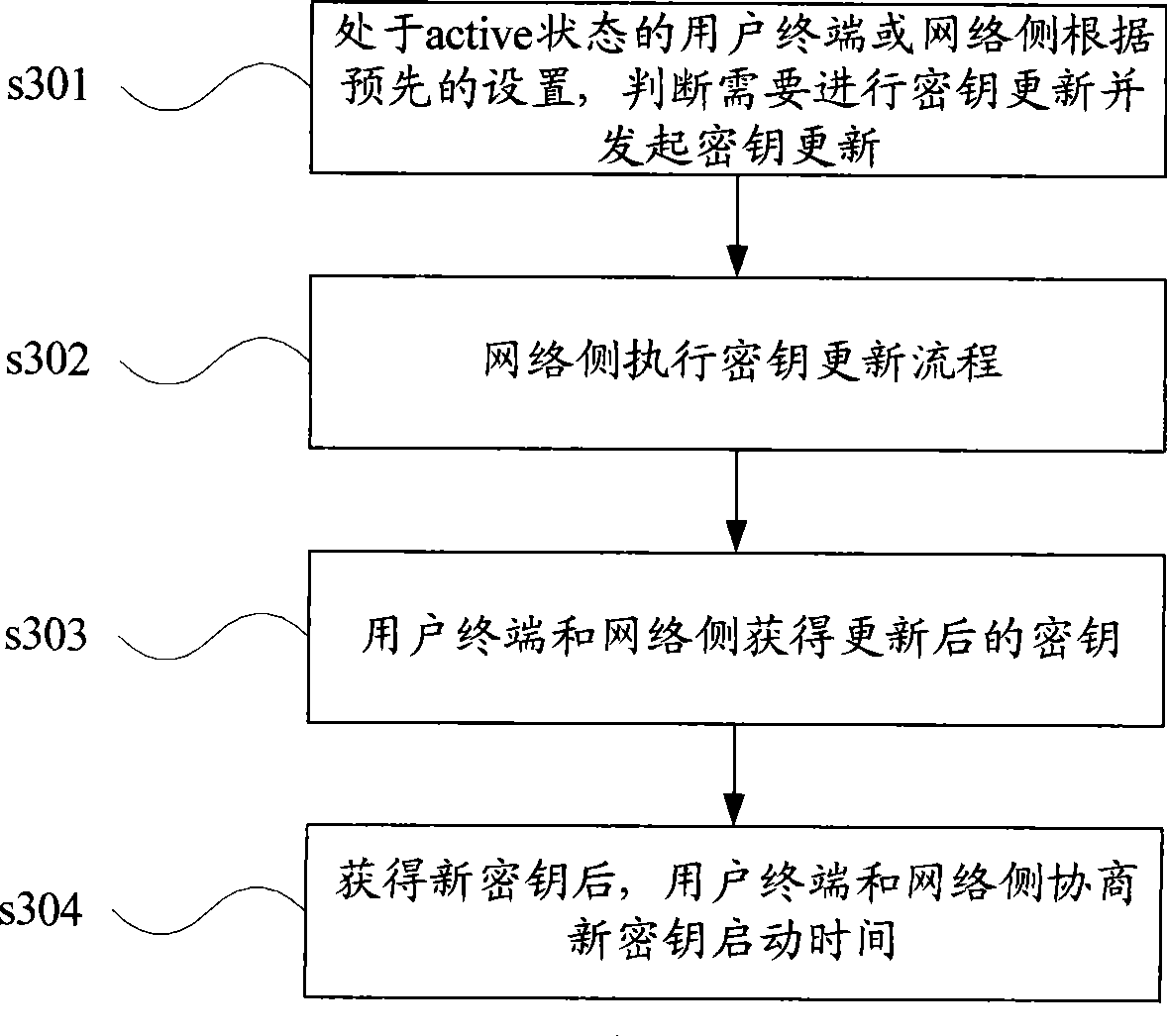
[0061] The key update process in Embodiment 3 is described as follows:
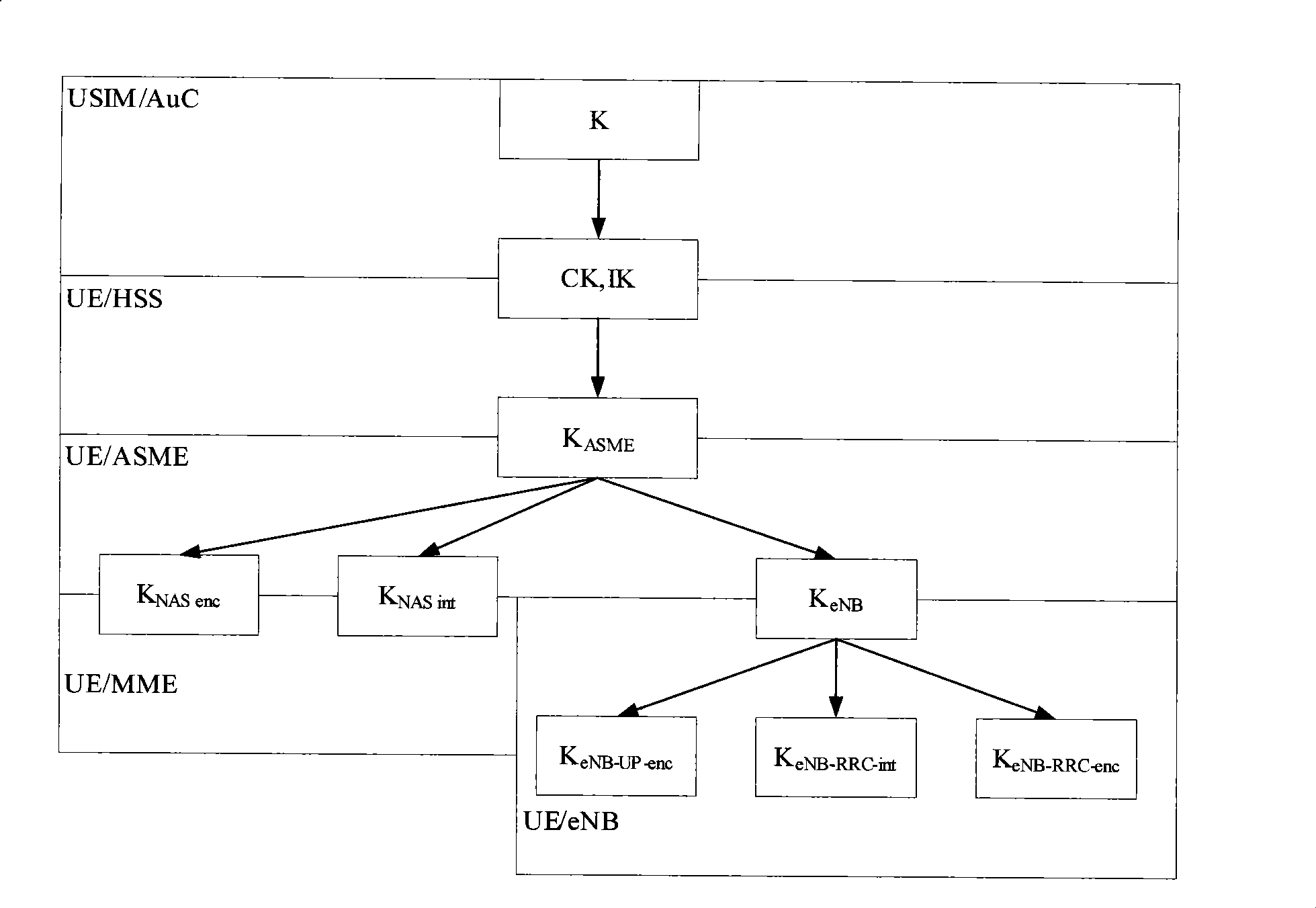
[0062] Step s501. When the eNB finds that the key needs to be updated according to the above security requirements, it sends a key update request message to the MME, requesting the MME to generate a new K eNB ; MME will start from K ASME Derive new K from eNB ;
[0063] The key update request message may be: (1) a request message specifically for the eNB to request the MME to update the key, and the request message requires a response from the MME. (2) A notification type message. Informing the MME that a key needs to be updated, the notification message does not require a response from the MME.
[0064] Step s502, MME according to the situation for the key K eNB to update. where K eNB It can be MME through the existing K ASME Derived, it may also be that the MME has updated K through the AKA process ASME calculated later.
[0065] Step s503, the MME sends the new K eNB sent to eNB. The MME ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com