Method for establishing network flow classified model and corresponding system thereof
A network traffic and classification model technology, applied in the transmission system, digital transmission system, data exchange network, etc., can solve the problems of low recognition rate, inapplicability of online real-time recognition, and the influence of extracted features, and achieve high recognition accuracy and fast The effect of the application layer traffic identification method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
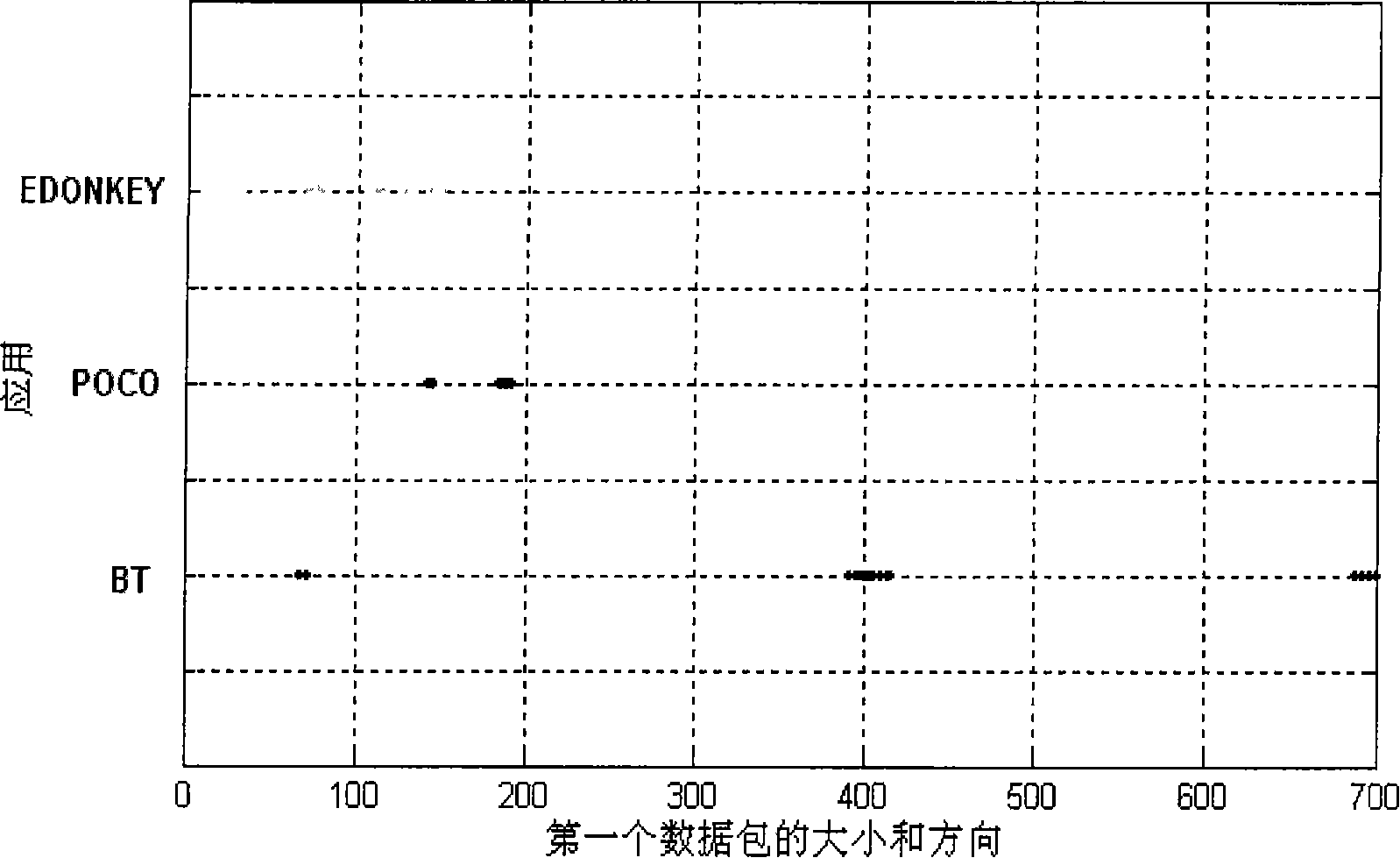
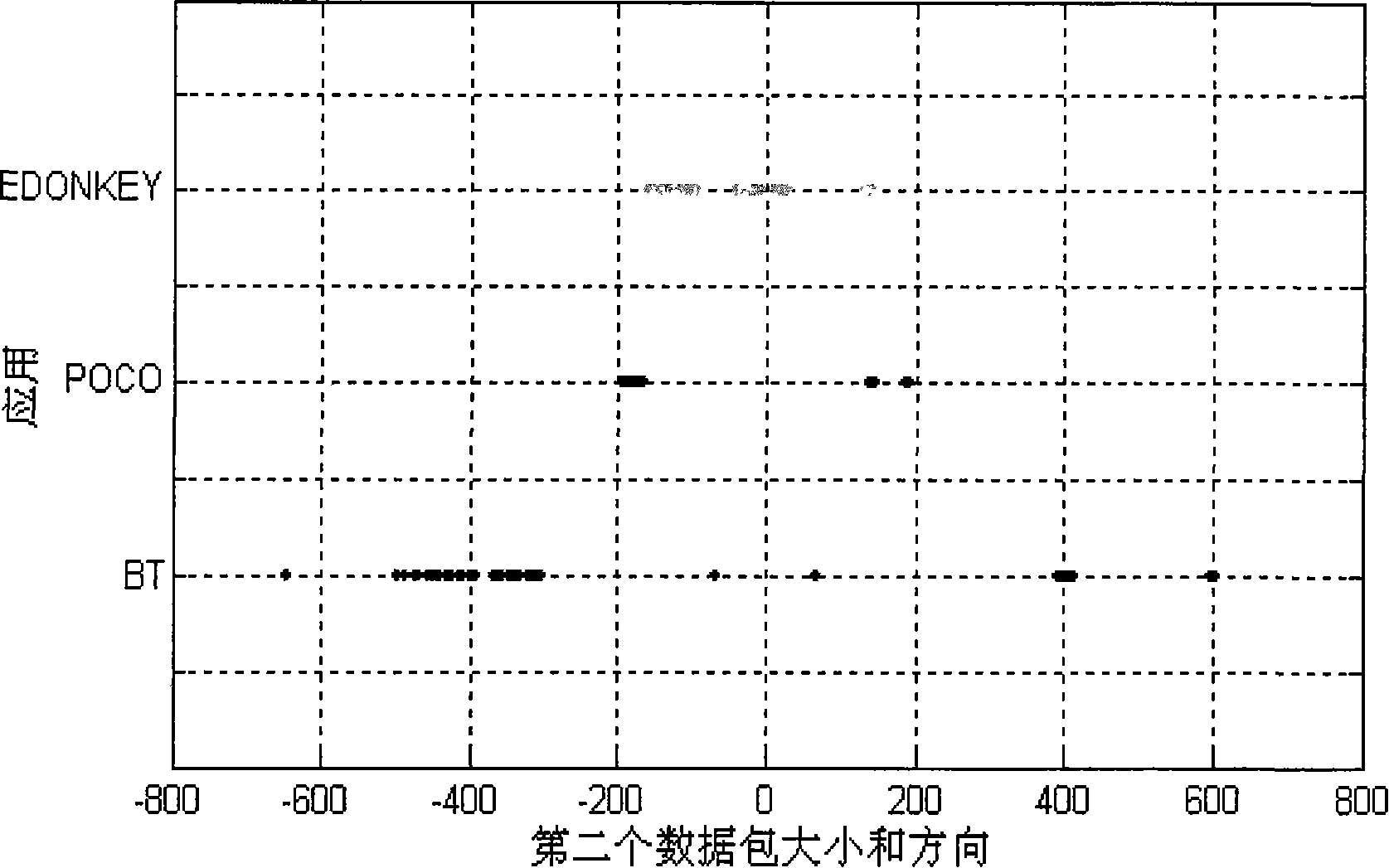
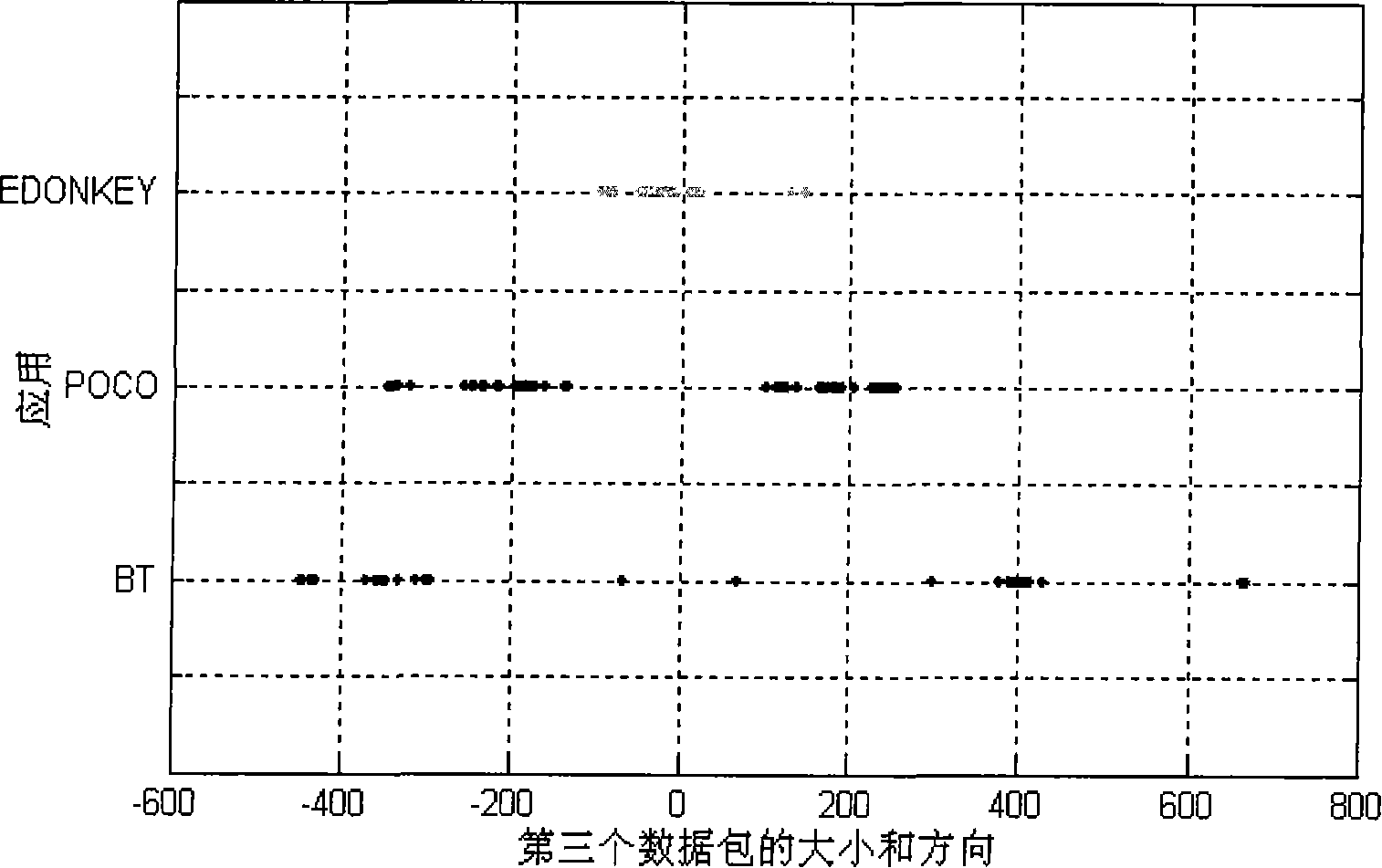
[0062] In the process of classifying network traffic, a segment of network traffic is firstly intercepted, and then the segment of network traffic is analyzed, and then flows in the network traffic are divided into specific applications. The stream is a quintuple including source IP, destination IP, source port, destination port and protocol of dual communication. In this process, the possible types of applications to which the flows belong are known, and the key lies in how to classify these flows and divide them into corresponding applications. In the process of classifying the streams, a network traffic classification model needs to be adopted, and what the present invention aims to solve is how to establish a network traffic classification model.
[0063] The establishment of the network traffic classification model is based on the analysi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com