A collocation method and system of alarming shielding
A configuration method and a configuration system technology, applied in the field of network management, can solve the problems of cumbersome and time-consuming network management alarm configuration operations, and achieve the effect of improving usability and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
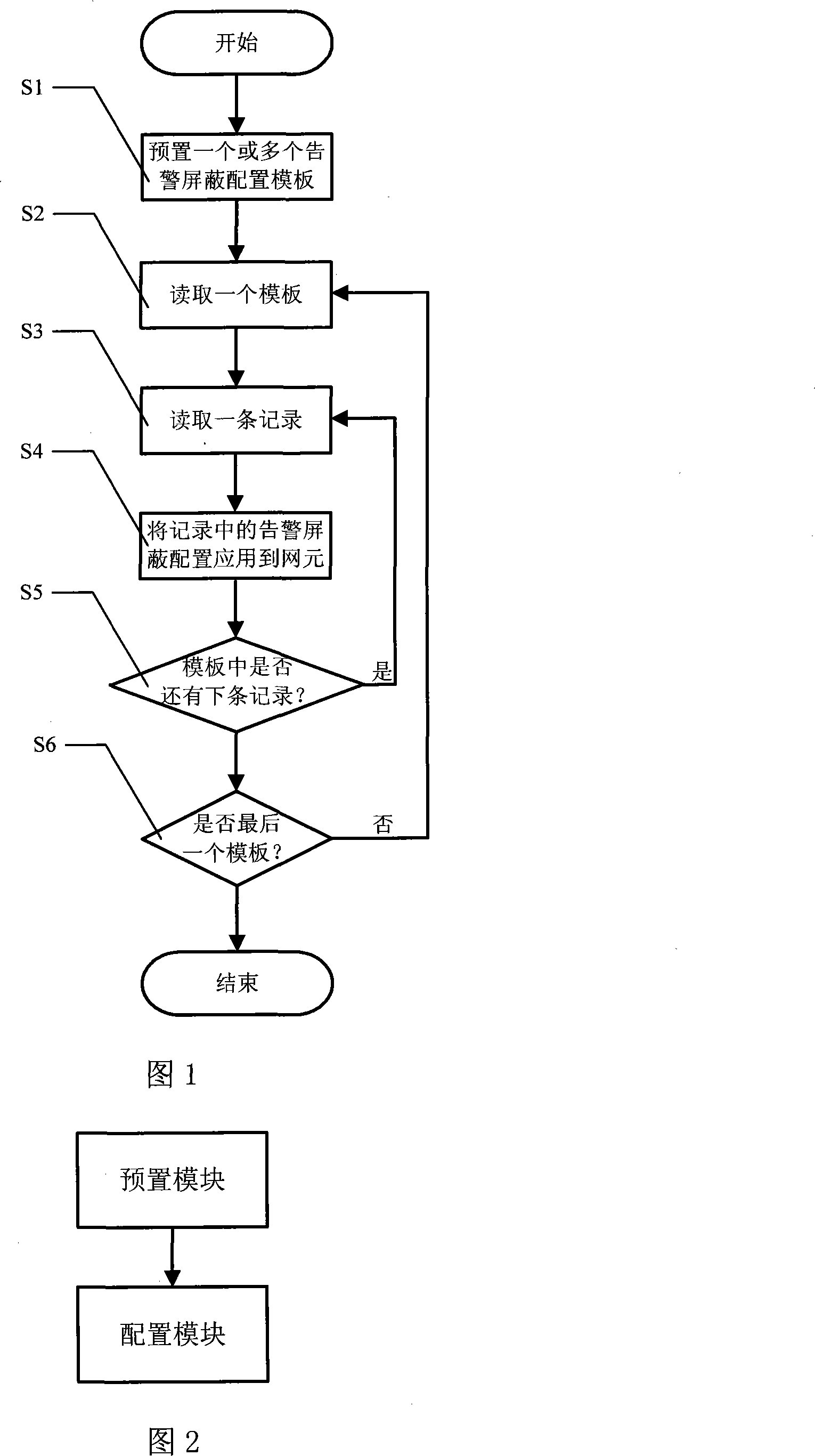
[0021] The present invention will be further described below with reference to the accompanying drawings and specific embodiments.
[0022] As shown in Figure 1, the method steps of the specific embodiment of the method are as follows:
[0023] S1: Preset one or more alarm masking configuration templates, and the content of the template is composed of one or more alarm masking configuration records. Each record contains one or more alarm shielding configuration items;
[0024] S2: Read the first template among the templates that have not been configured yet;
[0025] S3: Read the first record in the records that have not been configured in the template;
[0026] S4: For the read records, search for alarms that meet the recording conditions in each network element and perform alarm masking configuration in the records.
[0027] S5: If there is an unconfigured record in the currently read template, return to S3, otherwise proceed to S5.
[0028] S6: If there is an unconfigur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com