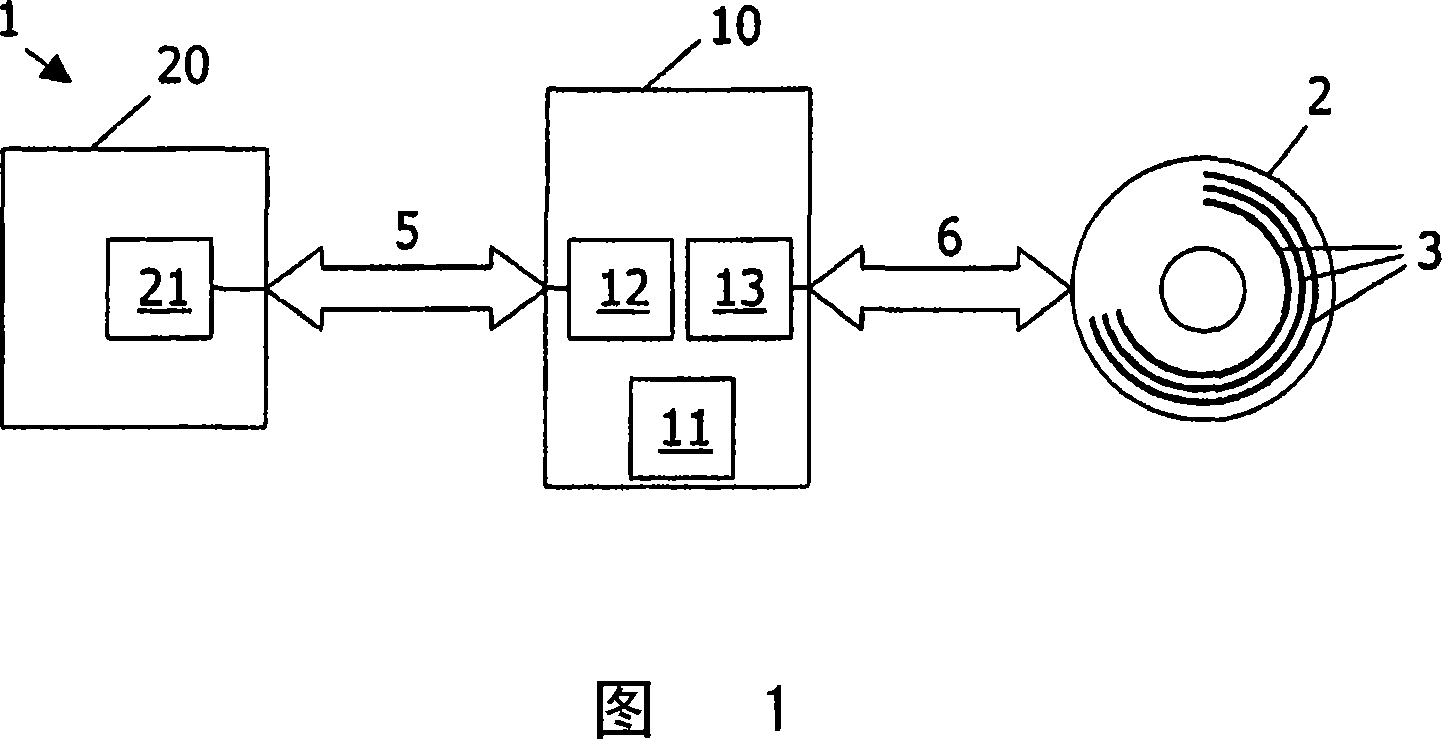
Method and device for storing data on a record medium and for transferring information
A technology for user data and equipment, which is applied in recording information storage, recording signal processing, special data processing applications, etc., and can solve complex problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0035] Example 1: Write (12) command (W12)
[0036] Figure 5 is a table illustrating a W12 command descriptor block adapted in accordance with the present invention.
[0037] As illustrated by the table in Figure 5, the W12 command consists of 12 bytes of 8 bits each. Byte 0 contains the opcode, bytes 2-5 are used to indicate the logical block address of the memory space where the data sector 30 should be stored, and bytes 6-9 are used to indicate the length of the data sector 30 to be transferred. Byte 11 is the control byte.
[0038] Bits 5-7 of Byte 1 and Bits 0-6 of Byte 10 are reserved for future definitions, ie they have no defined meaning yet. Therefore, it is possible to use any one of these bits as the encryption bit EB, which indicates that the W12 command is to be used as the write encrypted sector command WESC.
[0039] In the embodiment illustrated in Figure 5, the first four bits 0-3 of byte 10 are used as the encryption key identifier EKI. A value of EKI=0 m...
example 2
[0049] Example 2: Read (12) command (R12)
[0050] Figure 7 is a table illustrating the R12 command descriptor block adapted in accordance with the present invention.
[0051] As illustrated by the table in Figure 7, the R12 command consists of 12 bytes of 8 bits each. Byte 0 contains the opcode, bytes 2-5 are used to indicate the logical block address of the storage space of the data sector 30 that should be read, and bytes 6-9 are used to indicate the length of the data sector 30 to be transferred. Byte 11 is the control byte.
[0052] Bits 5-7 of Byte 1 and Bits 0-6 of Byte 10 are reserved for future definitions, ie they have no defined meaning yet. Therefore, it is possible to use any of these bits as an encryption bit indicating that the R12 command is to be used as the read encrypted sector command RESC.
[0053] In the embodiment as illustrated in Figure 7, the first four bits 0-3 of byte 10 are used as the encryption key identifier EKI. A value of EKI=0 means "no e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com