Safety protecting method for digital user line cut-in multiplexing device
A digital subscriber line and access multiplexer technology, which is applied in the field of computer network and telecommunication network, can solve the problems of high CPU usage rate of DSLAM equipment, the danger of device reset, high CPU usage rate, etc., to achieve convenient operation management and equipment safety , the effect of reducing the occupancy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
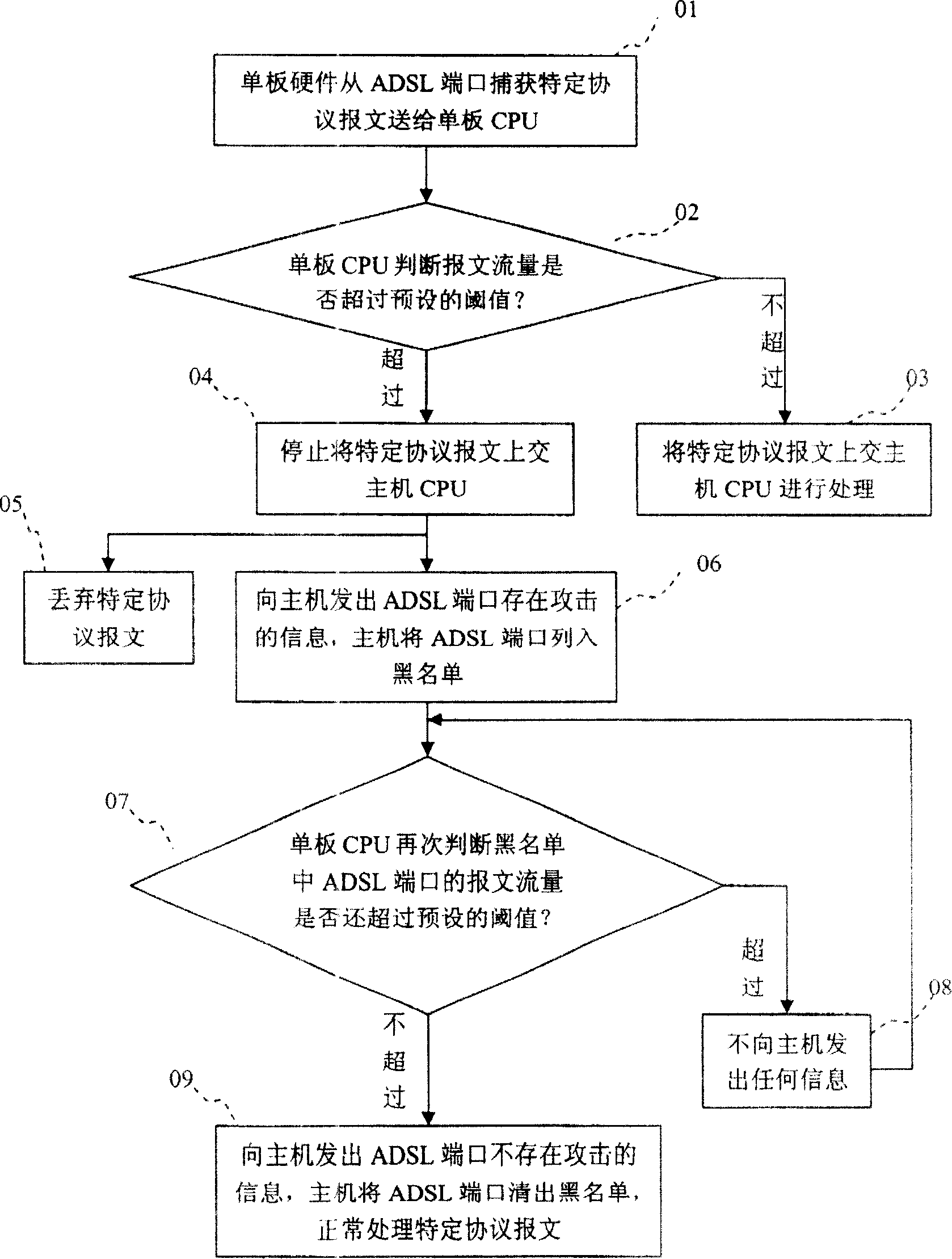
[0018] Taking ADSL (Asymmetric Digital Subscriber Line) as an example below in conjunction with accompanying drawing the present invention is further elaborated:
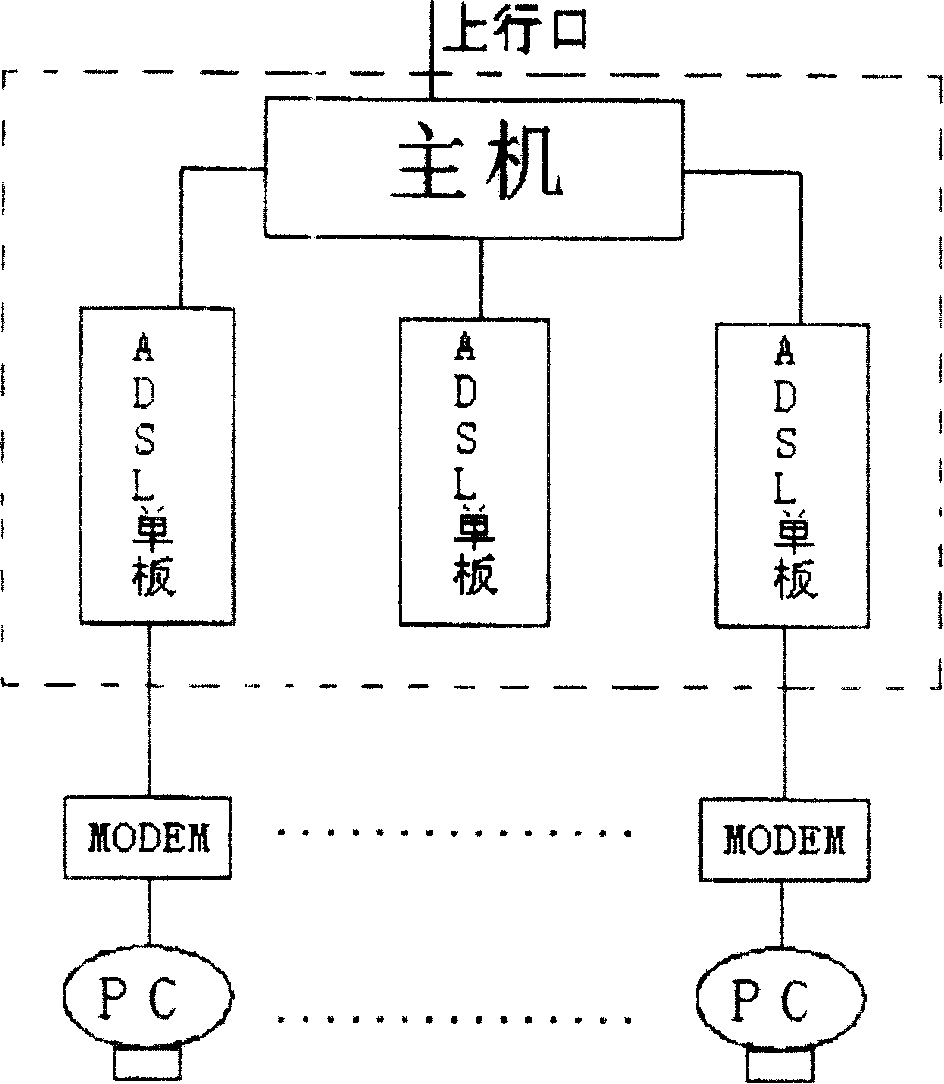
[0019] Such as figure 1 As shown, it is a schematic diagram of the network of the distributed bus mechanism of the DSLAM device. The dotted line box in the figure is the DSLAM device, which includes a host and multiple ADSL boards. The multiple ADSL boards are connected to the host respectively. The uplink port is connected to the upper-layer network, and the PC on the user side is connected to the corresponding ADSL board through the MODEM. The host computer is provided with a host CPU, and each ADSL board is also provided with its own single-board CPU. When the network is normal, various protocol packets sent by the PC on the user side are transmitted to the host through the MODEM and the ADSL board in turn. When the protocol packets are sent from the PC on the user side to the ADSL board, the single The board ha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com