System for product authentication by mobile phone
a mobile phone and product technology, applied in the field of product authentication, can solve problems such as the likelihood of fake products
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
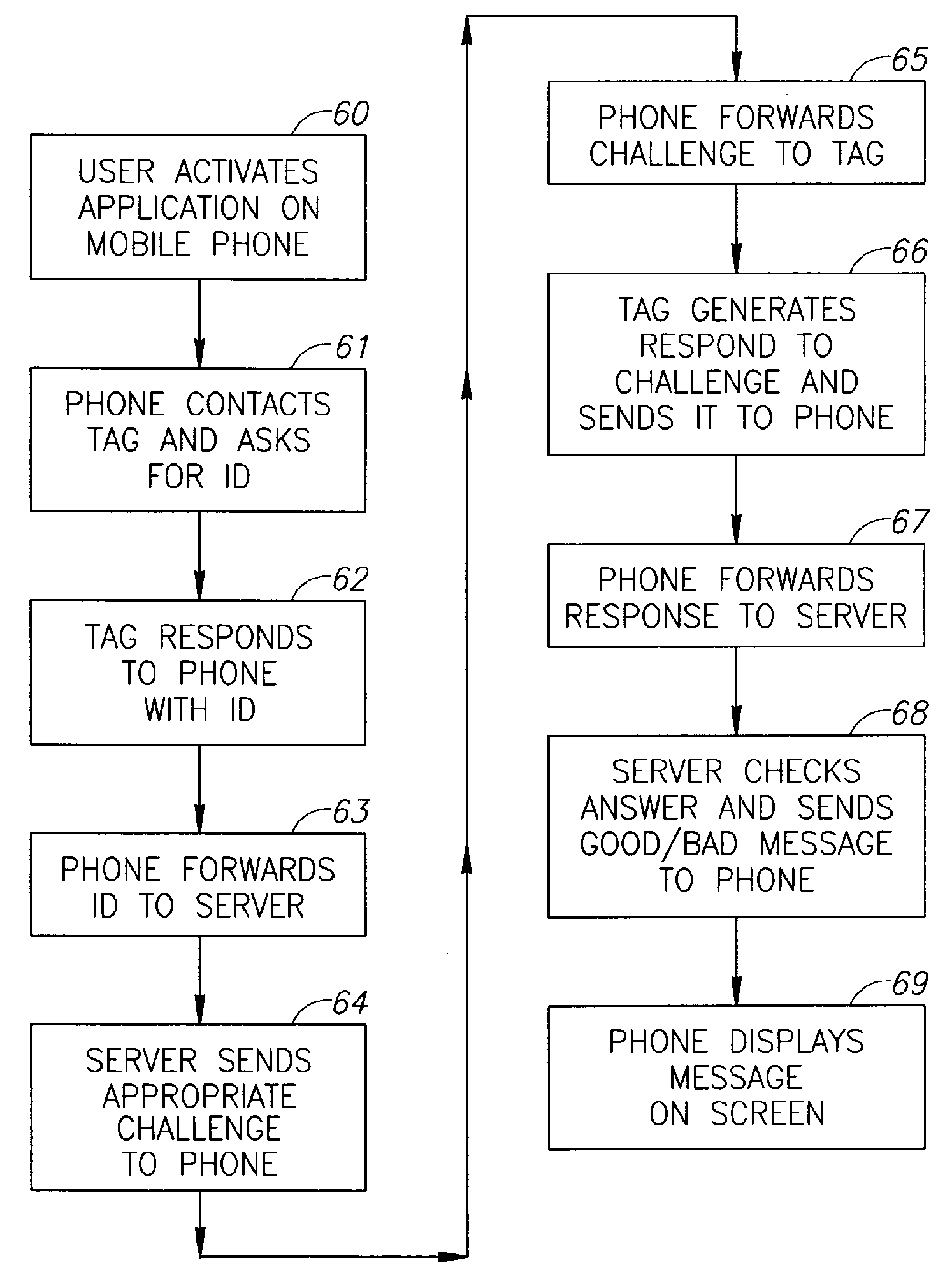
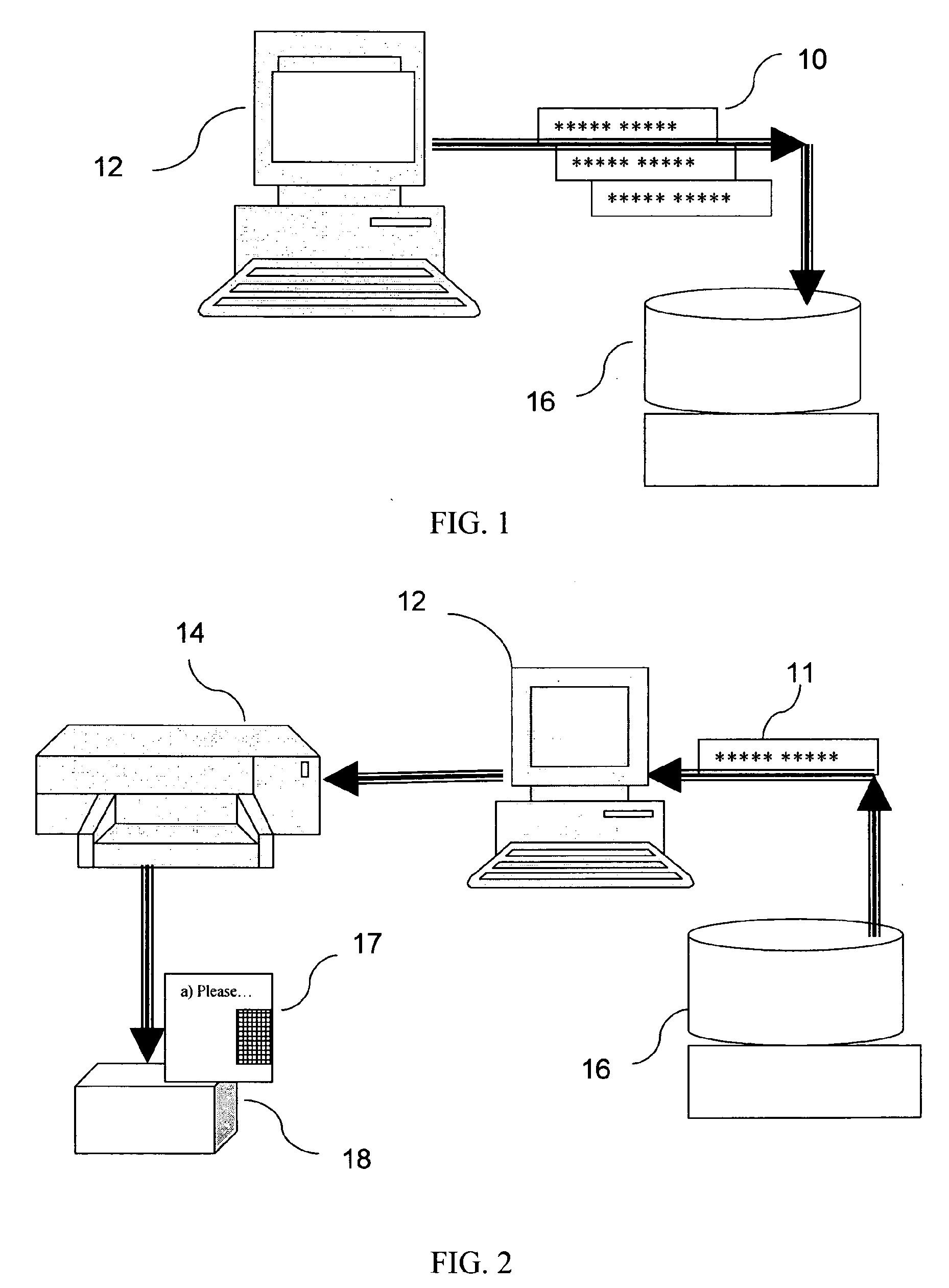
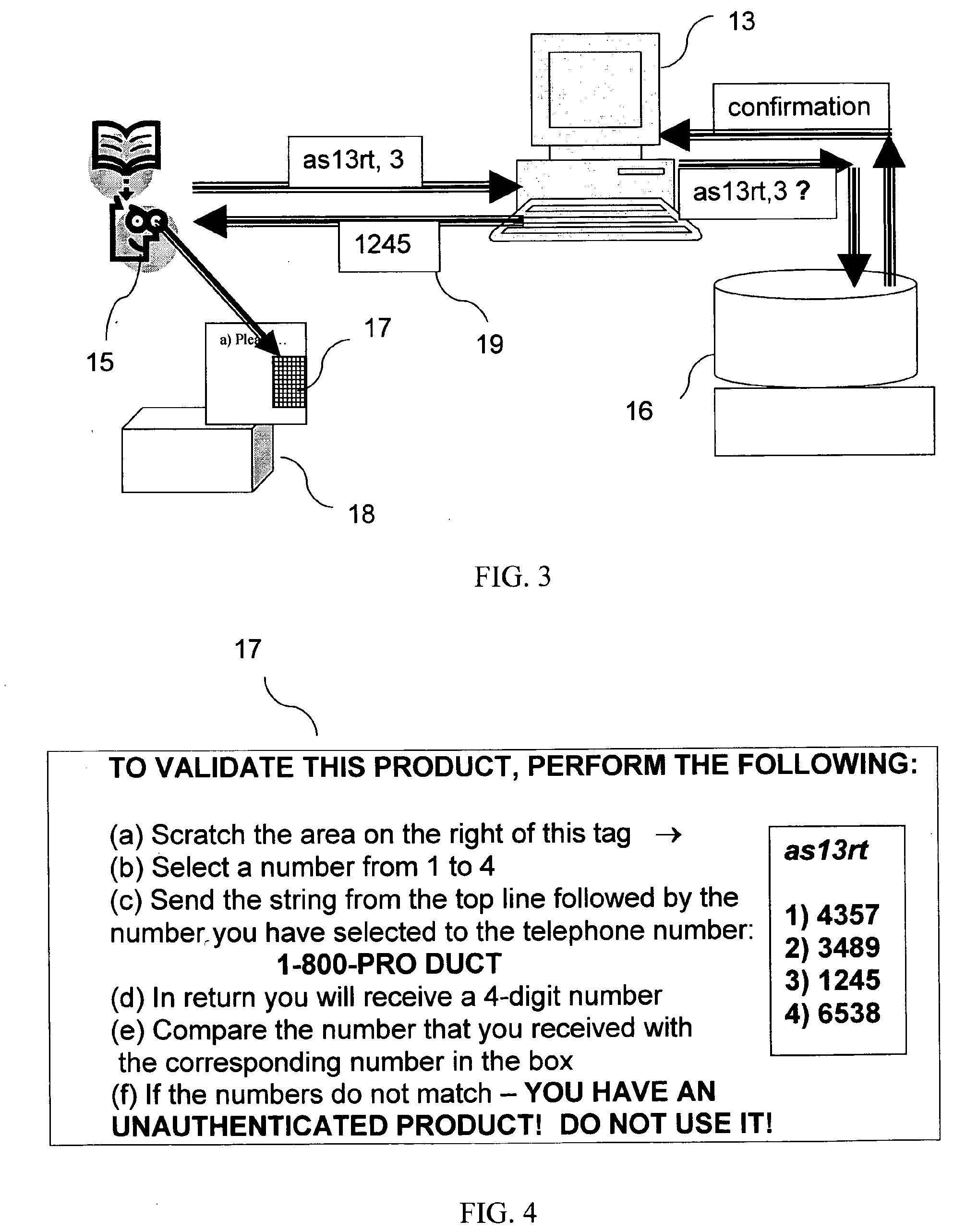
[0066]Though the first preferred embodiment of this invention can be executed in its simplest form using a simple single string of digits and / or letters as the secret number set, there are a number of reasons for preferred use of a more complex secret number format, as will be used below in this detailed description of preferred embodiments of the invention, where a multiple selection response number system is described. Firstly, a more complex set decreases the likelihood of unauthorized access to the system using forged or stolen number sets. In addition, the preferred embodiment described involves the purchaser's active participation in the validation process, thus increasing customer confidence in the system. Thirdly, using multiple sets of response numbers, it is possible to repeat each query for a specific product that number of times for additional safety, on condition that the checking system has been programmed to allow such multiple challenge. Finally, in the event that on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com