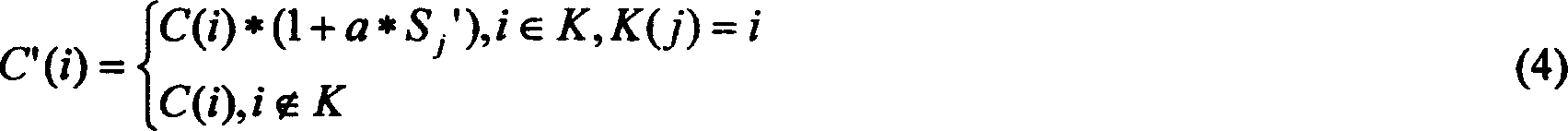Secured communicating method and device for hiding talking voice
A confidential communication and voice technology, applied in the field of information security, can solve the problem of being easily discovered and attacked by attackers, and achieve the effect of solving the problem that voice is easily eavesdropped
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
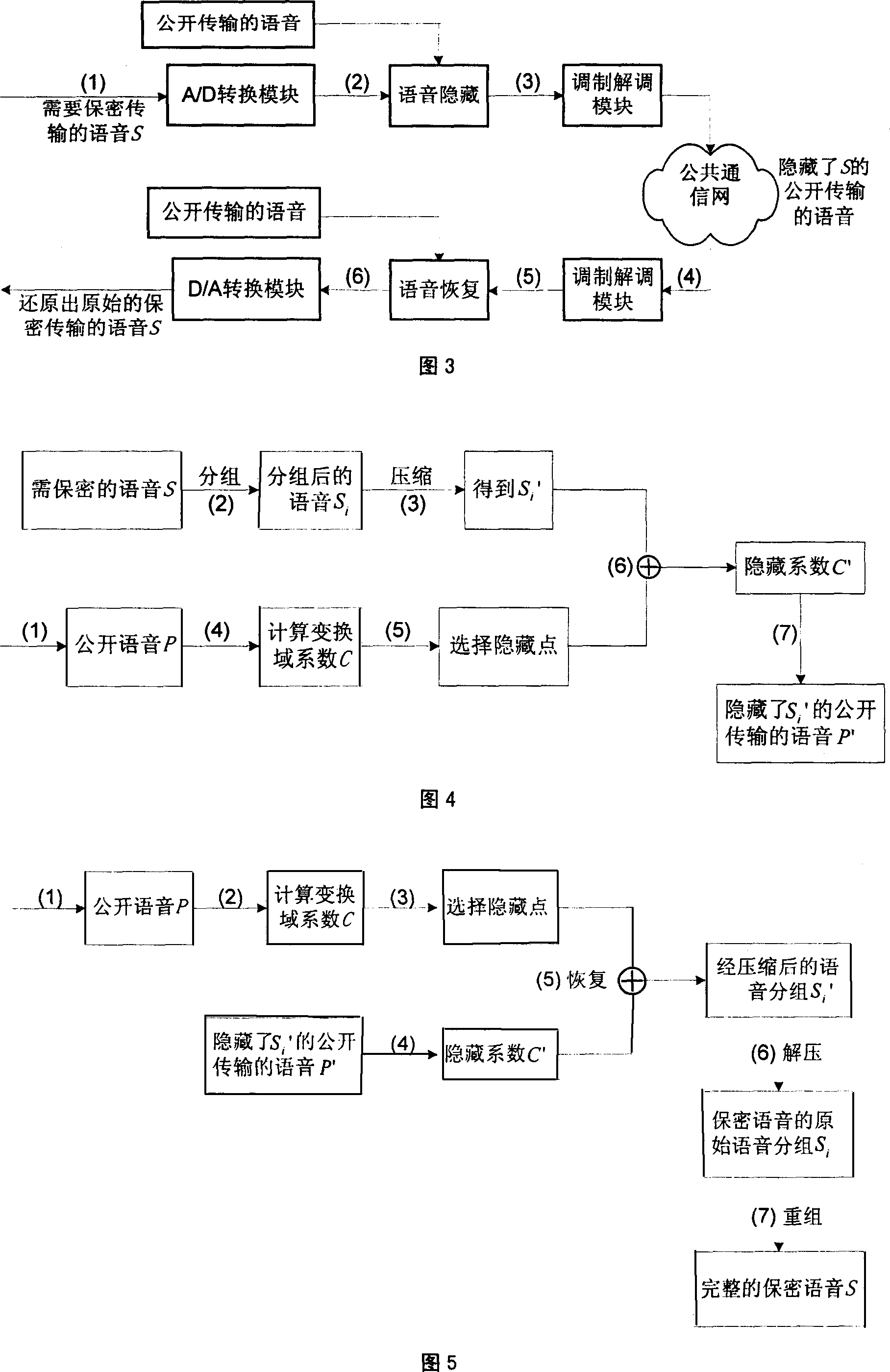
[0012] In order to further illustrate the principles and features of the present invention, the following description will be given in conjunction with the drawings.
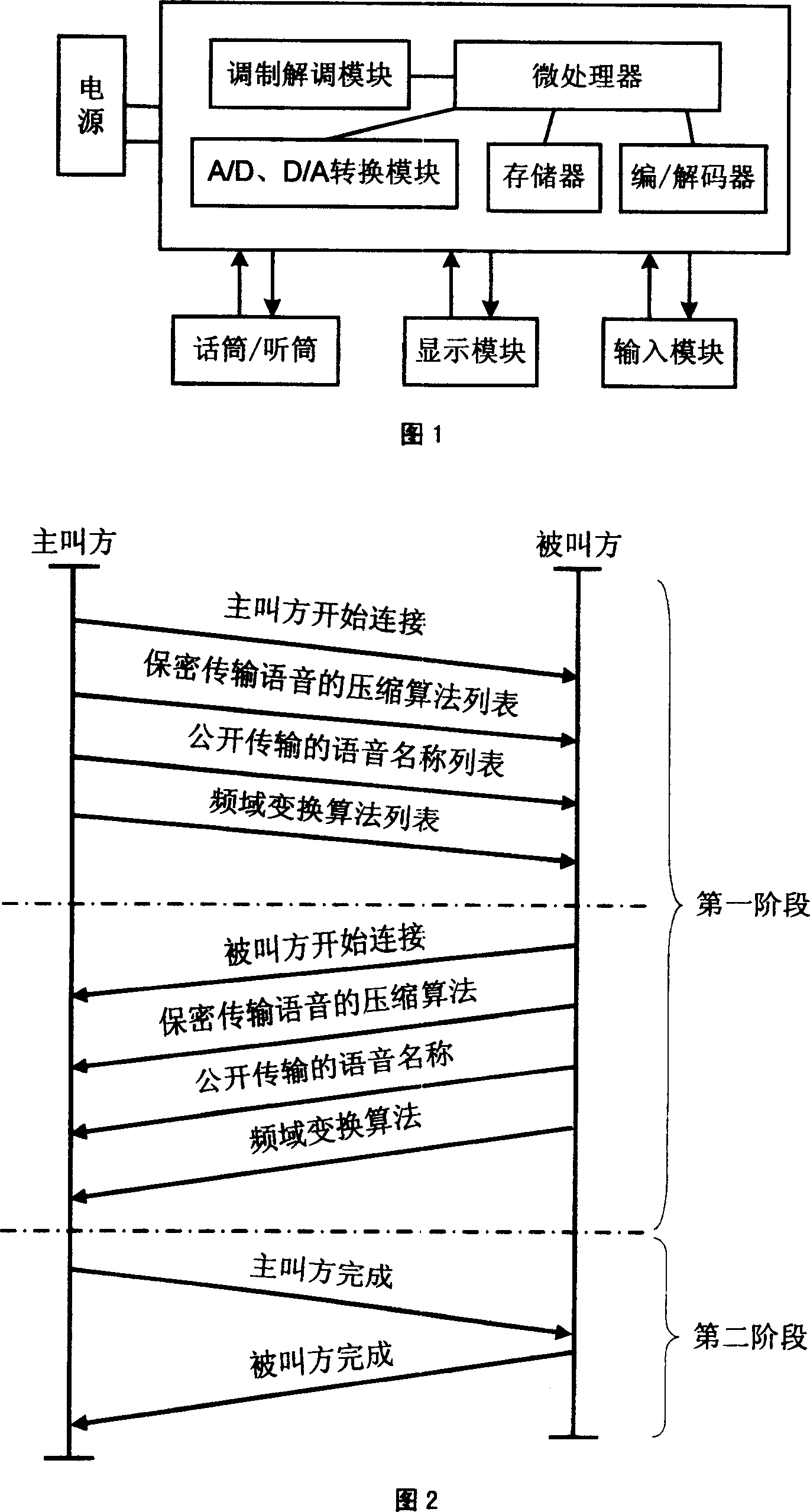
[0013] Fig. 1 is a hardware structure diagram of the present invention.
[0014] As shown in Fig. 1, the hardware circuit of the present invention is simple, and its main calculation is completed by a microprocessor. The memory is composed of flashmemory, which stores the main control program and publicly transmitted voices. The main control program performs most of the functions of the device, including the grouping, reorganization, concealment, recovery of voices that need to be kept secret, and the selection of publicly transmitted voices; The voice is selected by the user through the input module. The encoder / decoder completes the compression and decompression of the user's voice by the phone. The microphone converts the sound signal into an analog signal, sends it to the A / D conversion module, and converts it i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com