Data desensitization method and device and electronic equipment
A data desensitization and desensitization technology, applied in the field of data processing, can solve the problem that the data before and after desensitization cannot be guaranteed to be mapped one-to-one, and it cannot be ruled out that multiple original encoded data correspond to the same desensitized data, which requires a large amount of calculation. And other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
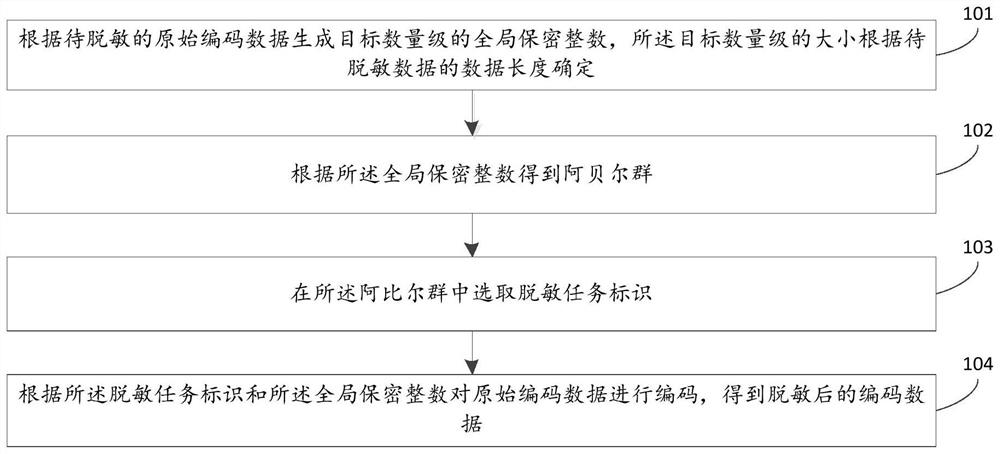
[0053] As an optional implementation of the present invention, the method also includes:
[0054] (1) Input the coding data C to be traced;
[0055] (2) Calculate the greatest common divisor g=(M, N) of the original coded data M and N, which can be obtained quickly by using the Euclidean algorithm.
[0056] (3) Calculate the multiplicative inverse element (M / g) of the original coded data M / g under the modulus N / g -1 , then there is M / g·(M / g) -1 = 1(mod N / g);
[0057] (4) The data traceability party (that is, the data provider) calculates the traceability identification ID' according to the following formula, and completes the traceability operation:
[0058] ID'=C / g·(M / g) -1 (mod N / g) (3)
[0059] In the formula: ID' is the identification obtained from traceability; C is the coded data after desensitization; g is the greatest common divisor of M and N; (M / g) -1 is the multiplicative inverse of M / g under modulo N / g. According to formula (1) C=M·ID, obtain ID'=C / g·(M / g) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com