Pseudo-wire (PW) dual-homing protection switching method
A protection switching and pseudo-wire technology, applied in the field of communication, can solve the problems of slow switching speed, consumption of system resources, long switching time, etc., and achieve the effect of reducing protection switching time and avoiding repeated refreshing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] Hereinafter, the present invention will be described in detail with reference to the accompanying drawings and examples.
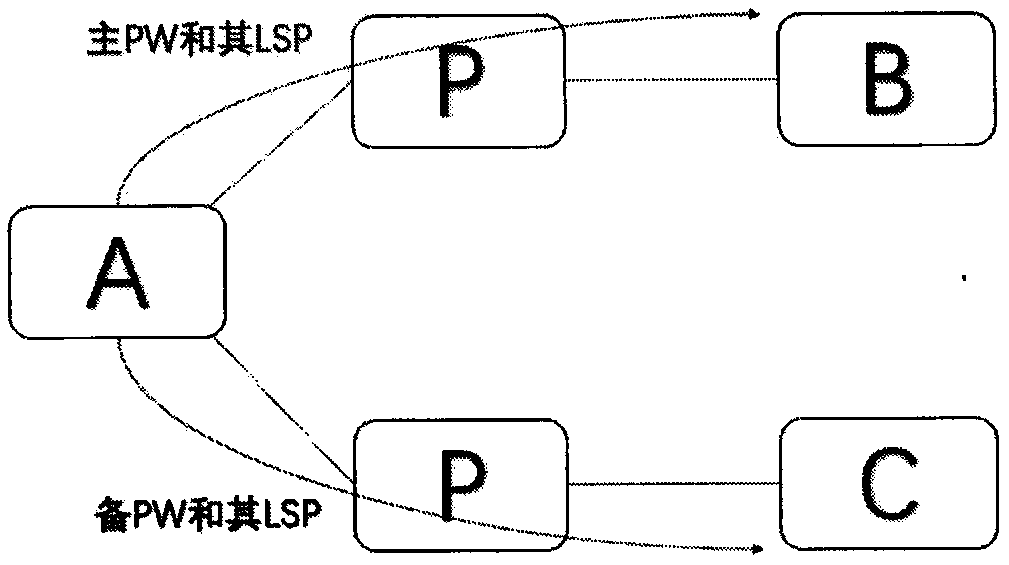
[0022] An embodiment of the present invention provides a protection switching method for a pseudowire PW, see figure 1 As shown in the pseudowire dual-homing network, it usually includes a source node and two next-hop nodes, and the source node and the two next-hop nodes respectively form an LSP.
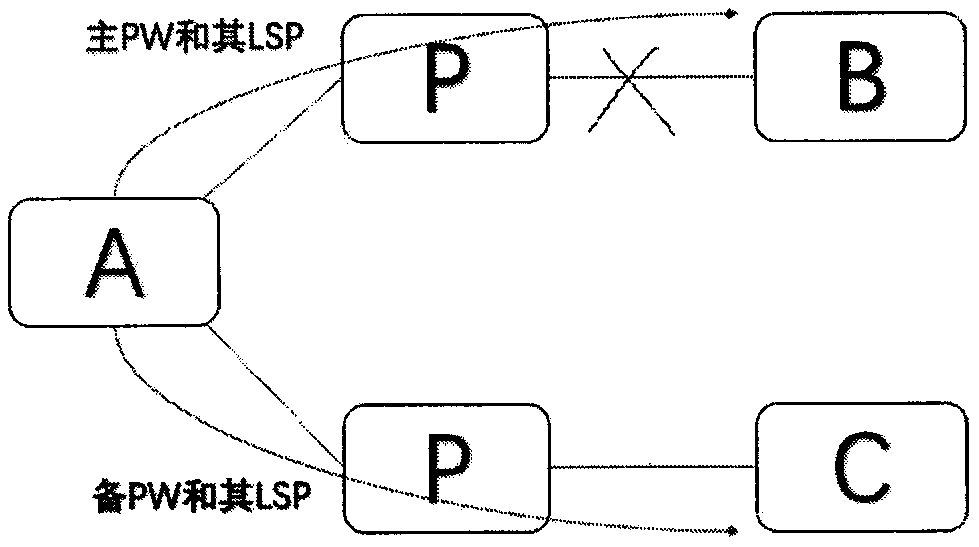
[0023] see figure 2 In this implementation case, the identification bit is set at the source node to associate with the LSP carrying the pseudowire. When the link fails, the status of the identification bit is changed when the pseudowire is deleted through the LSP to trigger a protection switching operation.
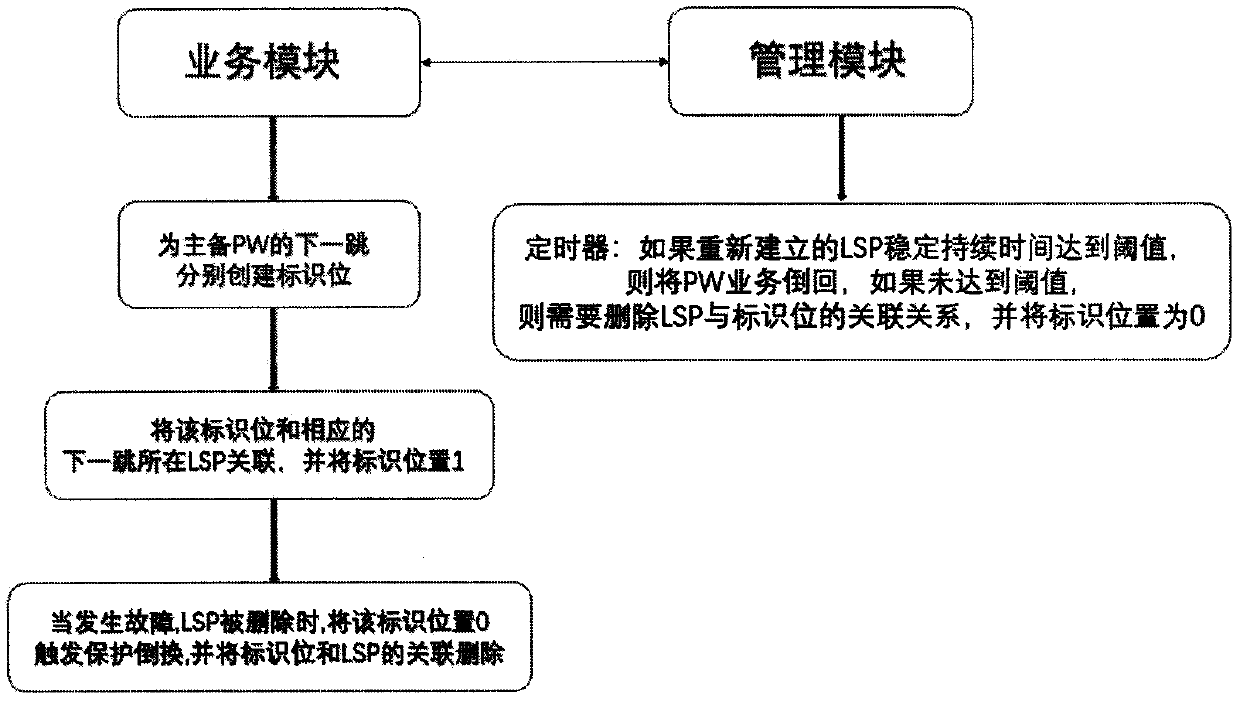
[0024] Specifically, see image 3 :
[0025] When the network is normal, the service module of the source node respectively creates an identification bit for the next hop of the active and standby PWs, associates the identification bit with the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com