Illegal outgoing mailbox identification system, method, device and storage medium
An identification method and identification system technology, applied in the field of data mining, can solve problems such as increasing investigation time, reducing investigation accuracy, internal data leakage, etc., and achieve the effect of shortening investigation time and improving investigation accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
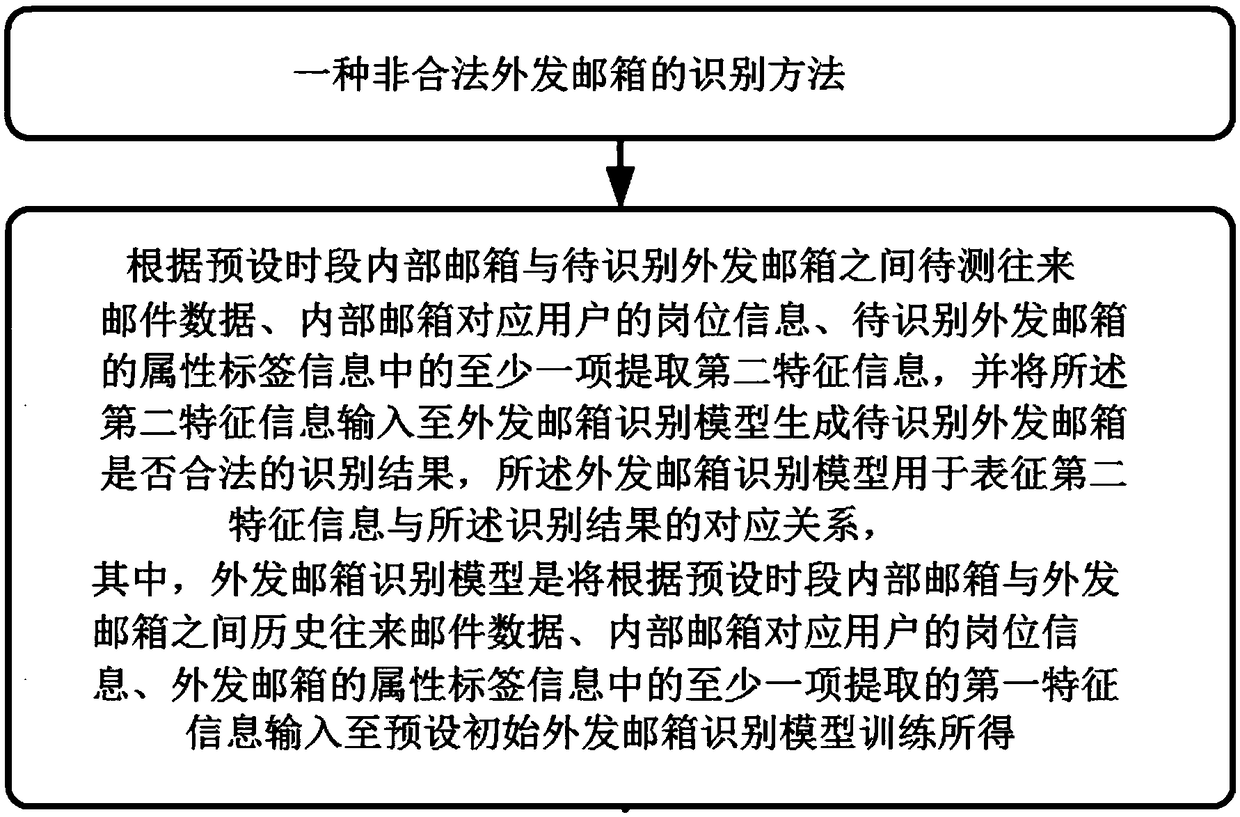
[0044] This embodiment provides a method for identifying an illegal outgoing mailbox, including the following steps:
[0045] S1, input the first feature information extracted according to at least one item of historical mail data between the internal mailbox and the outgoing mailbox, the post information of the corresponding user of the internal mailbox, and the attribute label information of the outgoing mailbox into the preset time period. The initial outgoing mailbox identification model is trained to obtain an outgoing mailbox identification model;
[0046] S2, extracting the second feature information according to at least one item of the mail data to be tested between the internal mailbox and the outgoing mailbox to be identified during the preset period, the position information of the user corresponding to the internal mailbox, and the attribute label information of the outgoing mailbox to be identified, The second feature information is input into the outgoing mailbo...
Embodiment 2
[0095] The same features of this embodiment and the first embodiment will not be repeated, and the different features of this embodiment and the first embodiment are:
[0096] This embodiment provides a method for identifying an illegal outgoing mailbox, including the following steps:
[0097] S1, input the first feature information extracted according to the historical mail data between the internal mailbox and the outgoing mailbox in a preset period and the attribute label information of the outgoing mailbox into a preset initial outgoing mailbox identification model to train an outgoing mailbox identification model ;
[0098] S2. Extract the second characteristic information according to the mail data to be tested between the internal mailbox and the outgoing mailbox to be identified during the preset period, and the attribute label information of the outgoing mailbox to be identified, and input the second characteristic information to the outgoing mailbox The identificati...
Embodiment 3
[0144] The same features of this embodiment and the first embodiment will not be repeated, and the different features of this embodiment and the first embodiment are:
[0145] In the specific steps of the identification method of this embodiment,
[0146] 2. According to the training data constructed by the features, establish a classifier for training and prediction.
[0147] (1) Case 1: If the positive and negative samples are unbalanced, and the legal outgoing mailboxes (customer mailboxes, supplier mailboxes, etc.) / private mailboxes are known to be greater than or equal to 0.7, the single-class (for example, oneclass svm) learning method is used to learn The logic of legal outgoing mailboxes (customer mailboxes, supplier mailboxes, etc.);
[0148] (2) Case 2: If the positive and negative samples are relatively balanced, and the legal outgoing mailboxes (customer mailboxes, supplier mailboxes, etc.) / private mailboxes are known to be less than 0.7, the classification model ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com