A method and device for identifying transaction risks
A technology of risk identification and identification methods, applied in the direction of sale/lease transactions, character and pattern recognition, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
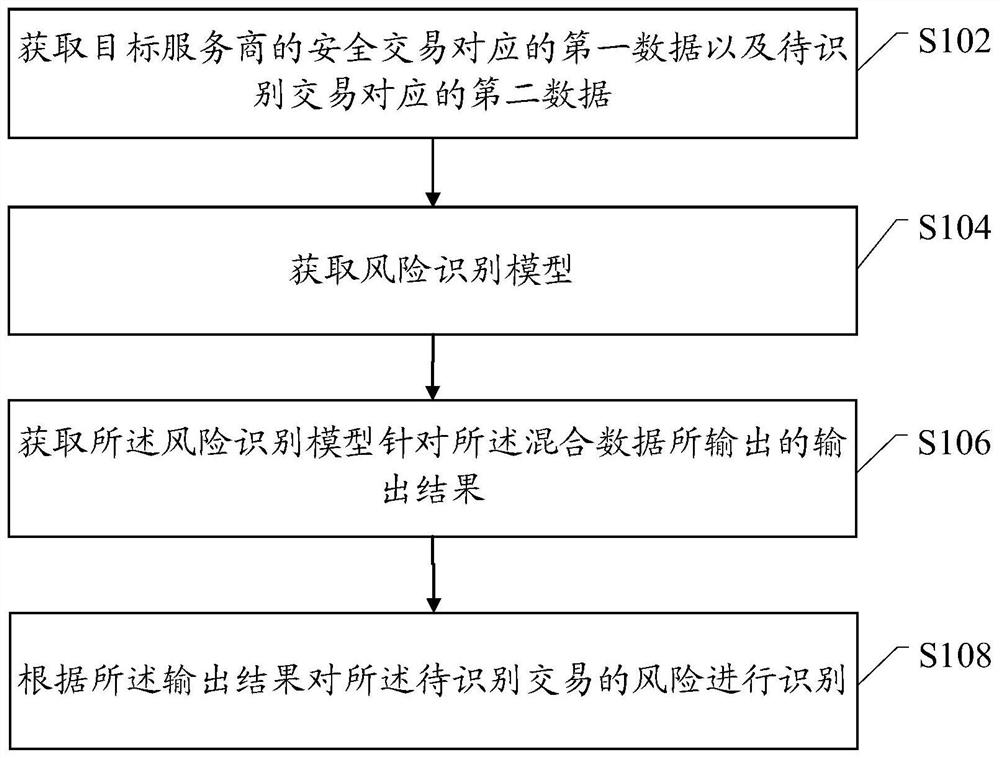
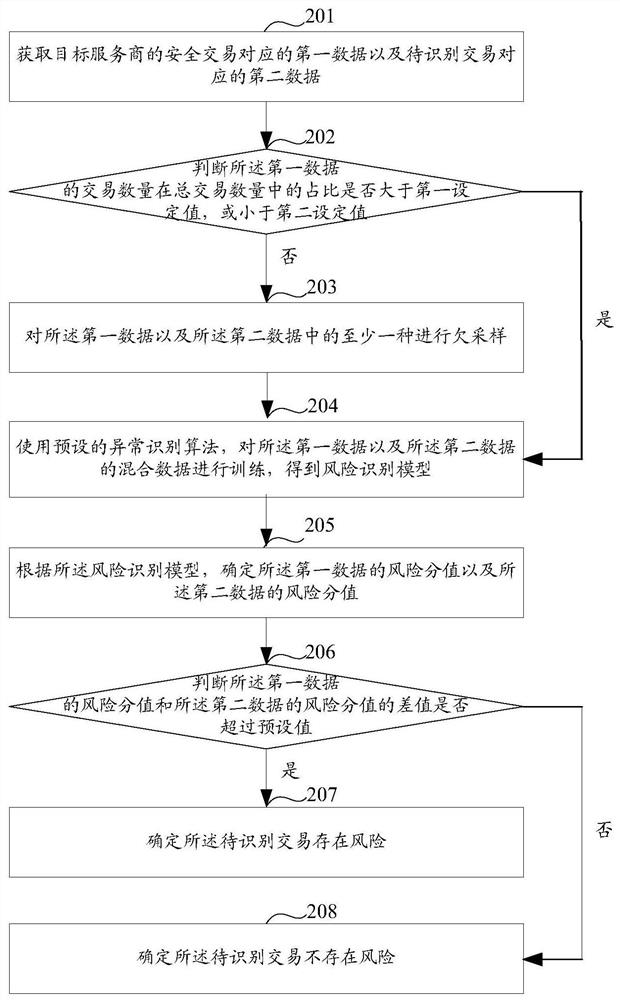
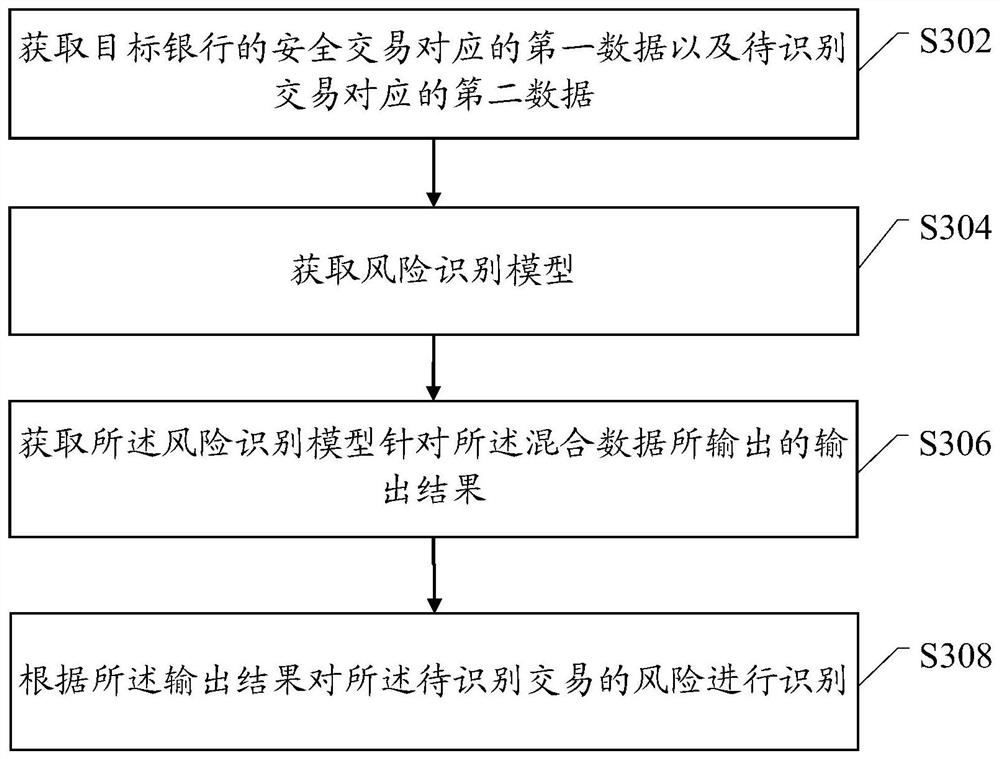
[0060] In Internet transactions, when a service provider receives a transaction request from a user, it needs to verify the user information carried in the transaction request. After the verification is passed, the service provider can process the user's transaction request, thereby realizing Internet transactions. However, in practical applications, there are some illegal users who will steal user information, and then use the user information to realize illegal transactions.
[0061]Taking bank transactions as an example, bank card service providers can realize bank transactions after verifying the bank card's BIN (Bank Identification Number), bank card user name, and bank card validity period. However, when information such as the BIN of the bank card, the user name of the bank card, and the validity period of the bank card are leaked, illegal users will easily steal the information of a type of bank card with the same BIN, and then use the stolen information to carry out il...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com