Blockchain-based threat intelligence exchange sharing system and method
A sharing system and blockchain technology, applied in the field of blockchain-based threat intelligence exchange and sharing systems, can solve the problems of uncollectible, complex threat intelligence confidentiality and privacy issues, reduce network energy consumption, improve System stability and purity, the effect of improving system stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The following describes several preferred embodiments of the present invention with reference to the accompanying drawings, so as to make the technical content clearer and easier to understand. The present invention can be embodied in many different forms of embodiments, and the protection scope of the present invention is not limited to the embodiments mentioned herein.
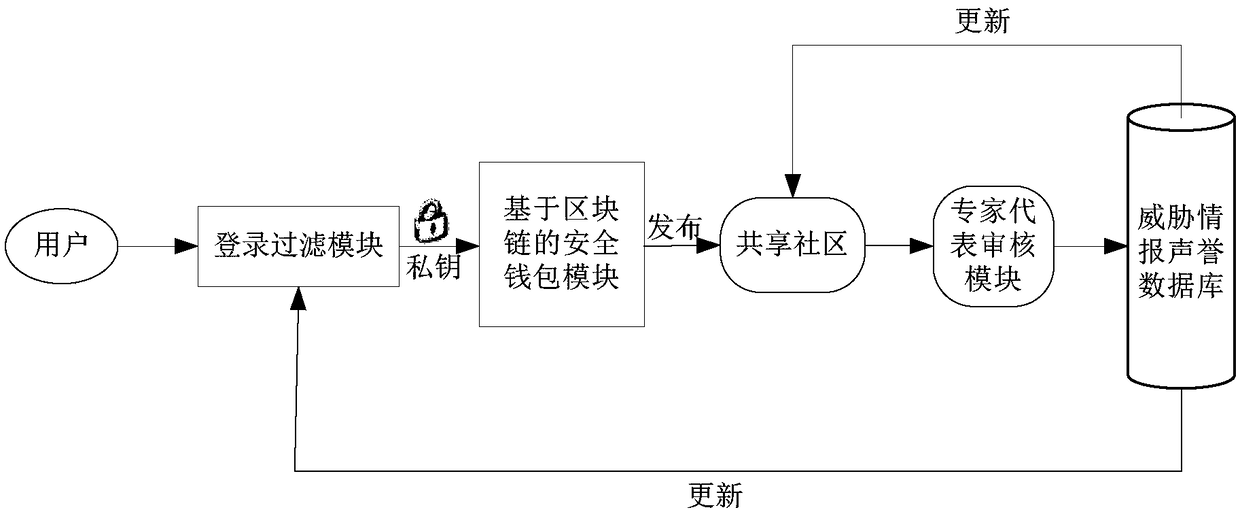
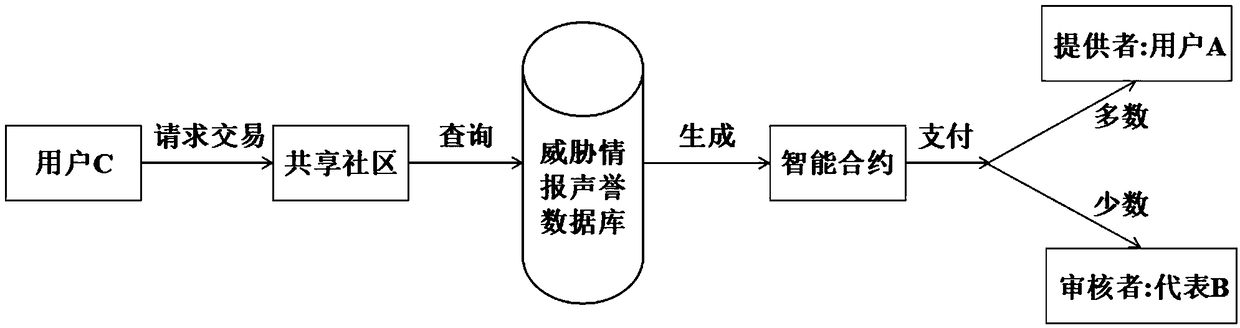
[0043] A preferred embodiment of the present invention consists of a login filtering module, a blockchain-based security wallet, a shared community, an expert review module based on the Delegated Proof of Stake (DPOS) consensus mechanism, and a threat intelligence reputation database. The system takes the threat intelligence of existing security vendors and individual security experts as the original input, and the subsequent threat intelligence input by individual users is verified by expert representatives selected by the DPOS consensus mechanism, and then stored in the threat intelligence reputation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com