Software protection method and system
A software and protected technology, applied in software testing/debugging, program/content distribution protection, instruments, etc., can solve problems such as passiveness, inability to ensure that software ownership is not infringed, and the cost of rights protection rising.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
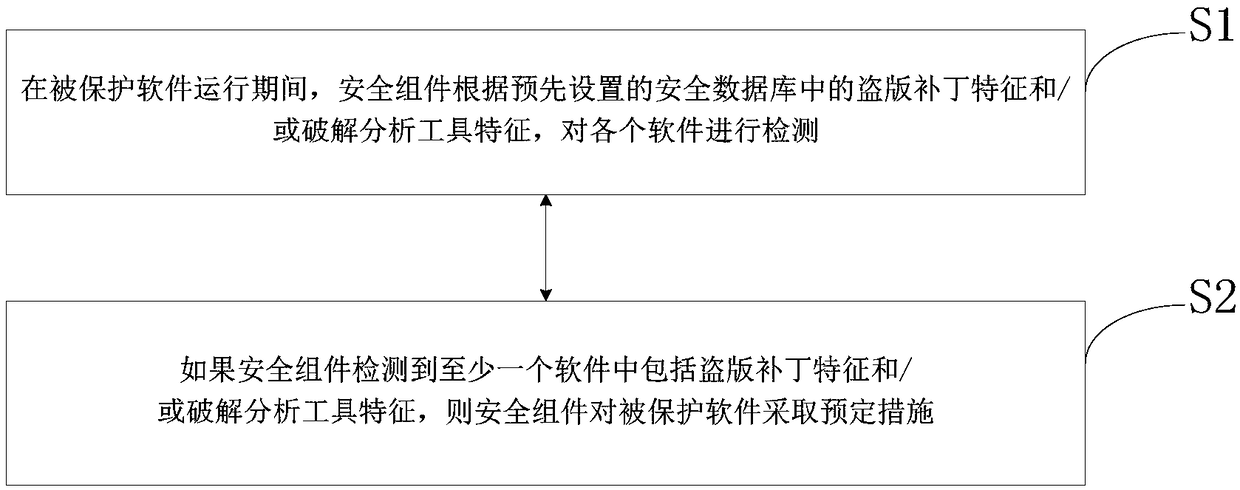
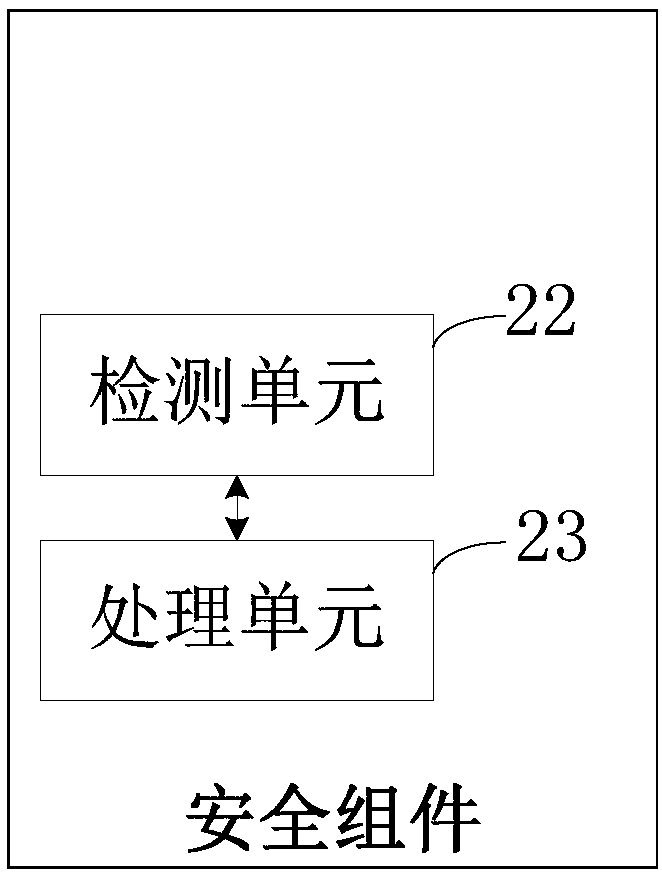
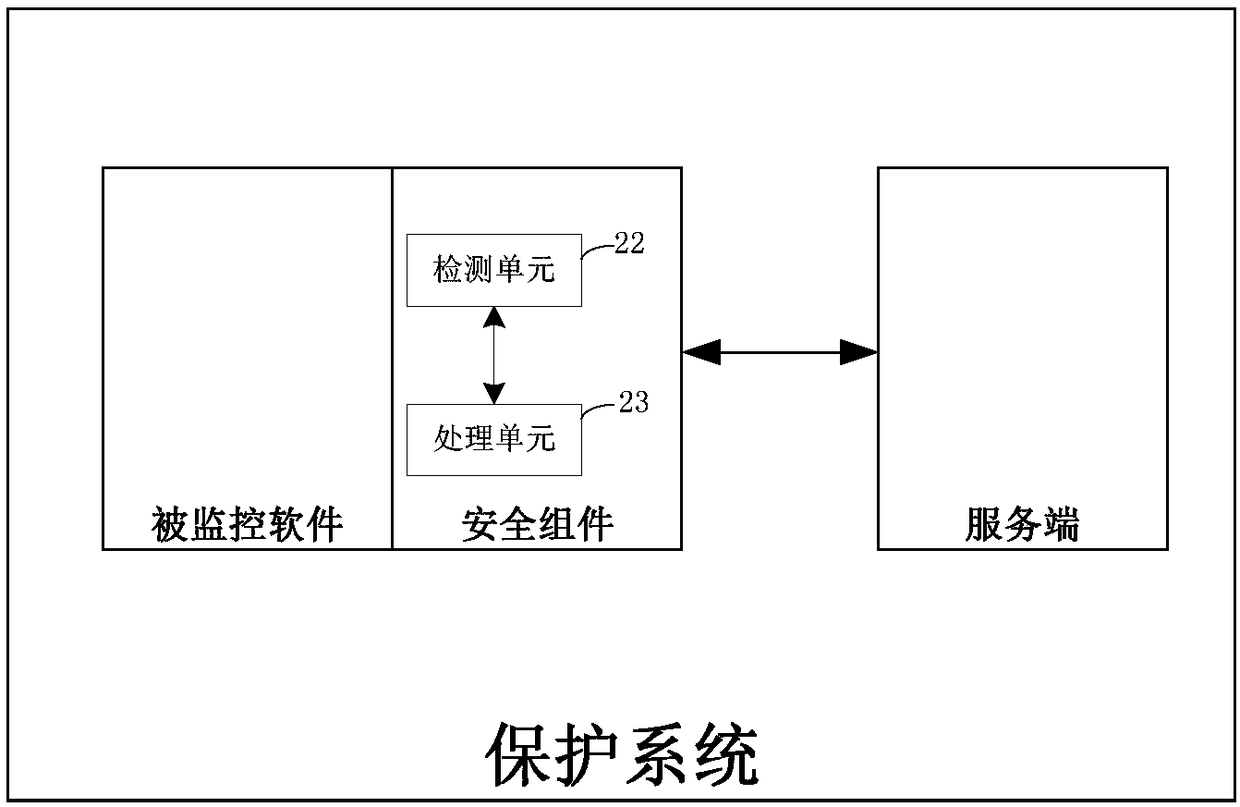
[0051] Such as figure 1 Shown is a software protection method according to an embodiment of the present invention, the method mainly uses a security component bound to the protected software to protect the protected software, wherein the security component can be an anti-hacking engine, for example, and the protected software The binding of software and security components can be understood as binding the functions of the two, so that when the user uses the protected software, the security component must be run at the same time, and it can also be understood that the protected software uses the security component as the "interface" for communication with the outside world , making it impossible for pirates to separate the security component from the protected software without affecting the function of the protected software. This protection method includes:
[0052] S1. During the operation of the protected software, the security component detects each software according to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com