Device, system and method for securing a negotiation of at least one cryptographic key between units
A technology of cryptographic keys and equipment, which is applied in transmission systems, digital transmission systems, secure communication devices, etc., and can solve problems such as rising slowly, computing consumption ratio exponentially rising, insecurity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] Unless stated otherwise, identical or functionally identical elements are provided with the same reference symbols in the figures.
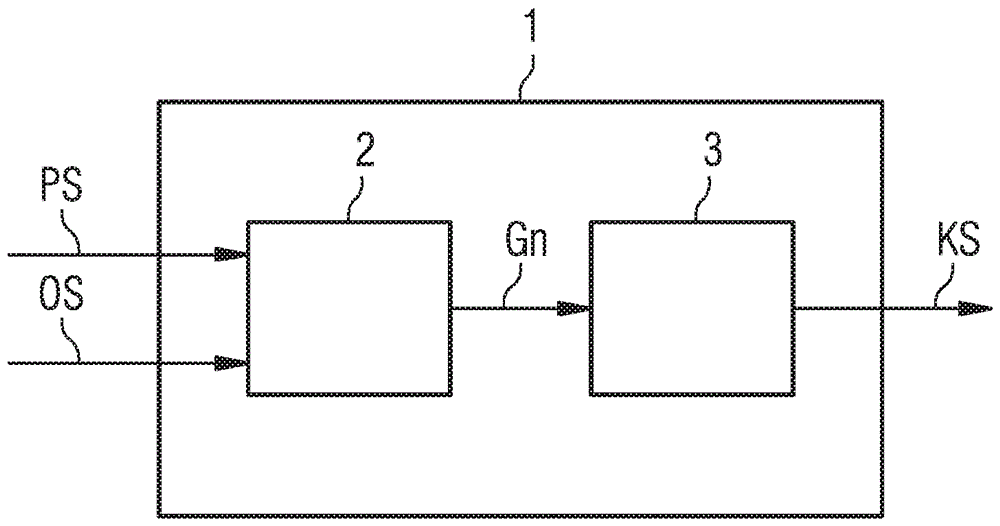
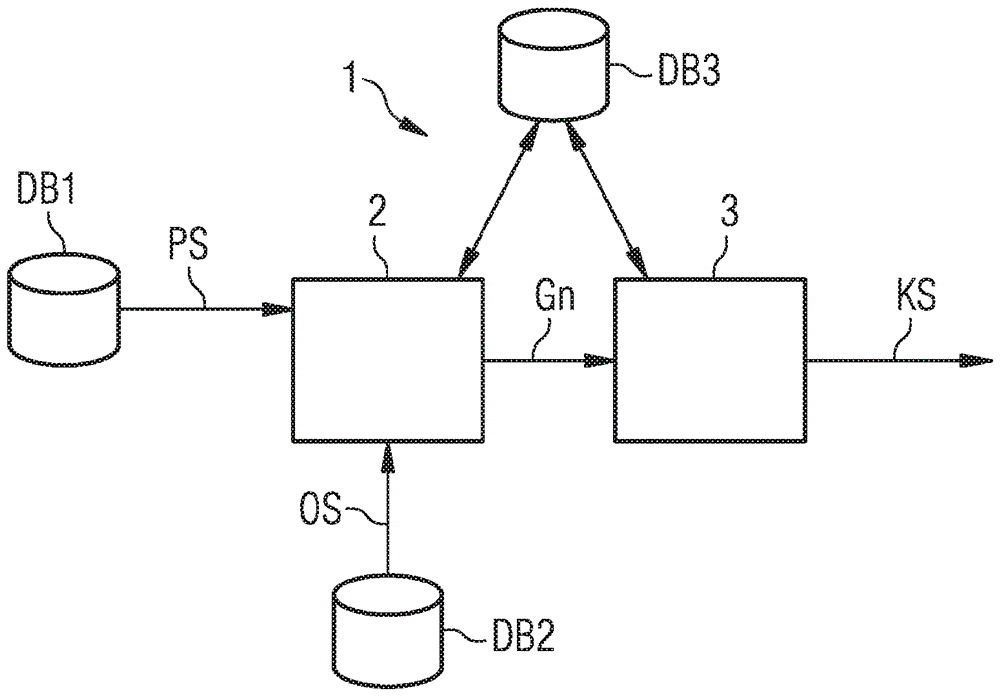
[0065] figure 1 A diagram is shown of a method for securing the negotiation of at least one cryptographic key according to an embodiment of the invention.
[0066] In this case, the equipment is manufactured in factory F. This device is a household device in the present example and is to be installed in building G after provision A. A device is, for example, a heating body whose thermal output is controlled by means of building automation, ie, the individual control of the devices in the building. Since not only a single heating element is installed in building G, but a large number of heating elements are installed, it is necessary for temperature regulation in building G that the individual heating elements communicate with each other and exchange measurement data relating to heat release, for example.
[0067] In the exemplary embodi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com