A Parallel Processing Method for Trajectory Prediction of Multiple Targets in Air
A technology of trajectory prediction and parallel processing, applied in multi-programming devices, resource allocation, etc., can solve the problems of shortening communication time, low processing capacity of computer nodes, and inability to meet the real-time performance of the system, so as to achieve balanced task allocation and reduce communication time Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0076] Example 1: The target data ph5 arrives (that is, the existing target data arrives and has not disappeared)
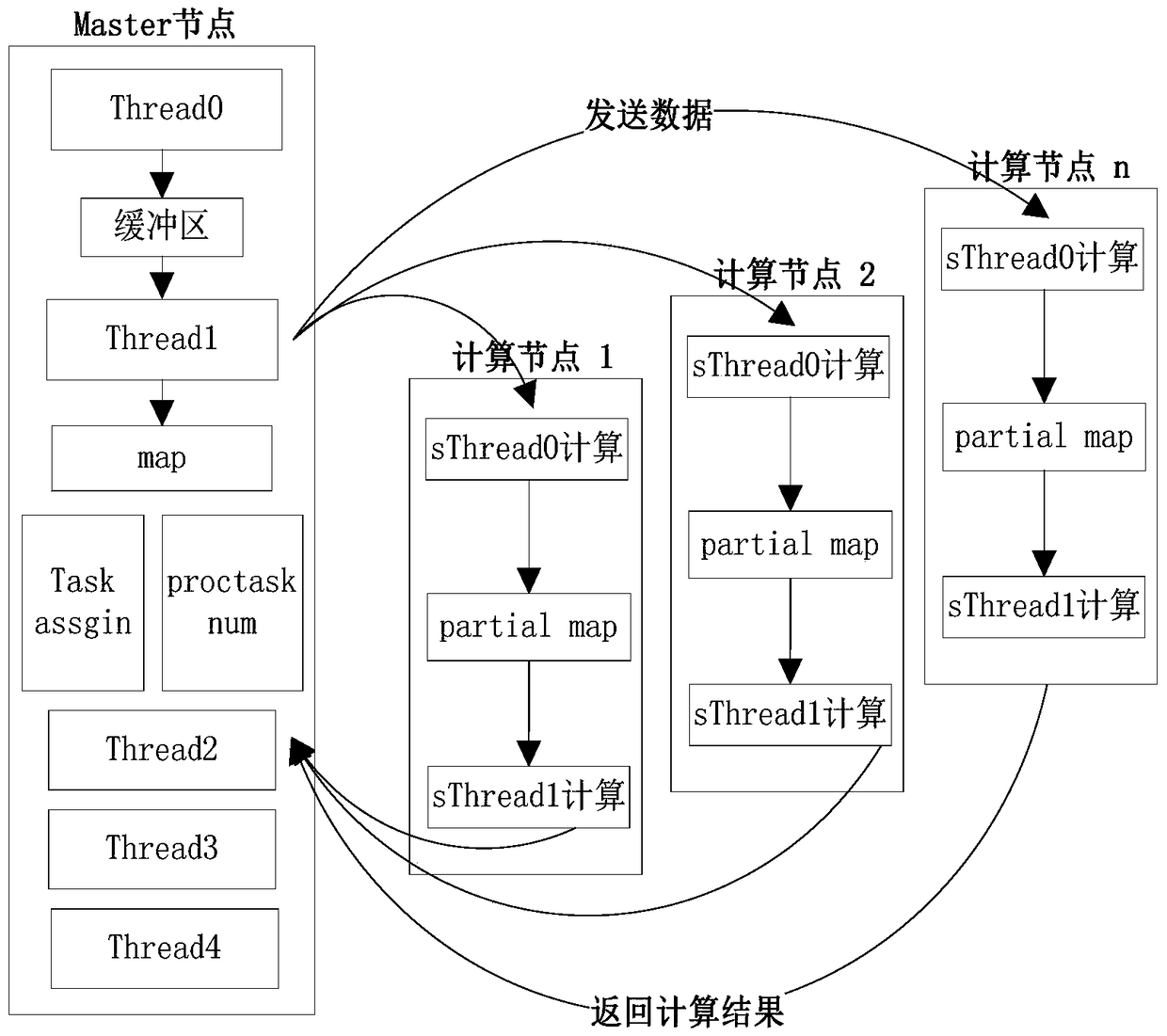
[0077] Step 1: Thread0 of the Master node receives the target data through the network interface, puts it into the opened buffer buffer, and receives the data of the ph5 target this time;
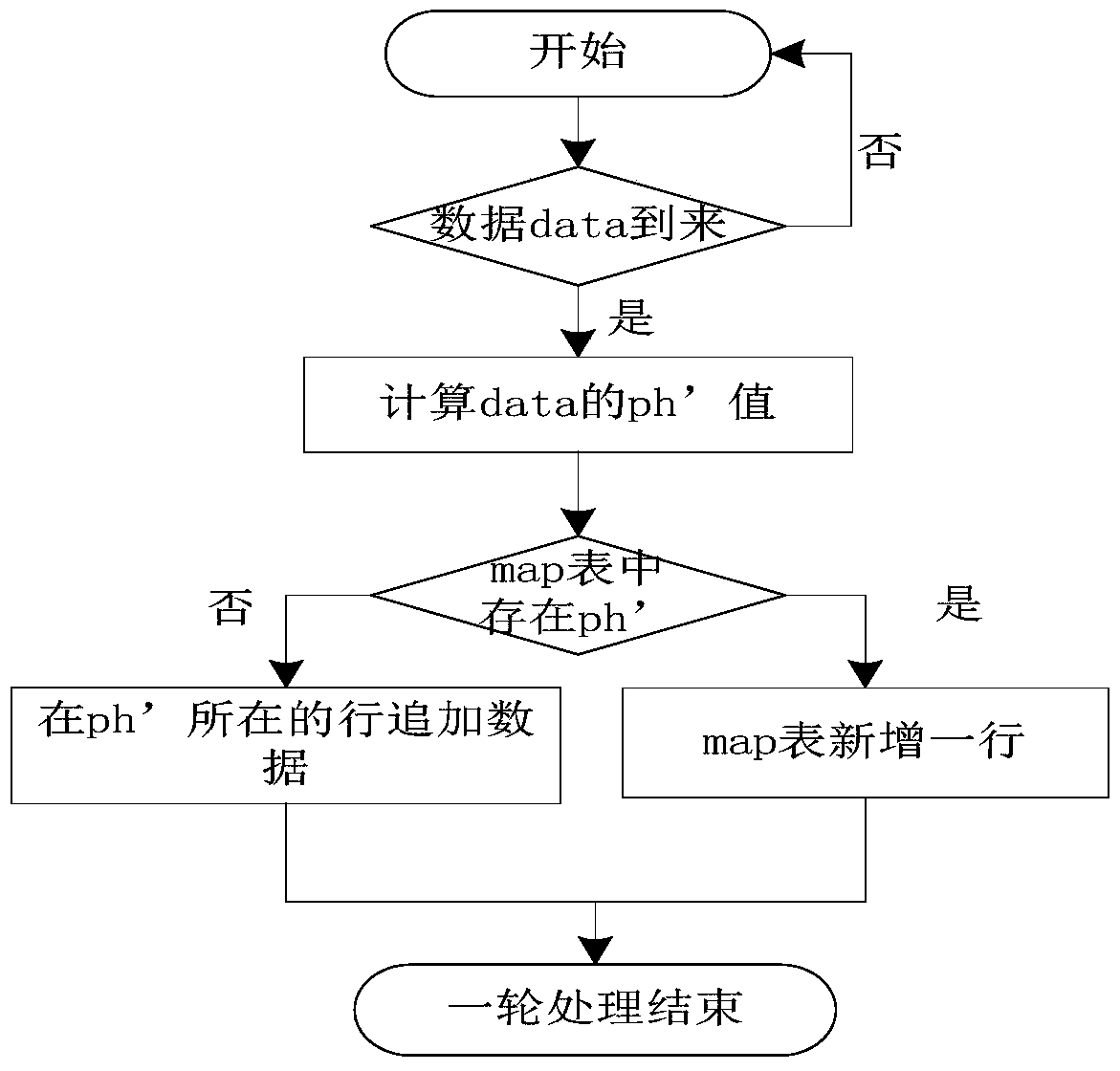
[0078] Step 2: Thread1 reads the data ph5 from the buffer, and queries the map table; at this time, there is data of the target ph5 in the map table, so add data to the value of the row where ph5 is located in the map table, and it becomes the form of Figure 5(2), At the same time record the arrival time of the target data;
[0079] Step 3: Check the length len of the data packet in the value of ph5, if len is less than the set sending threshold N, no data will be sent, and the processing of ph5 will end; if len is equal to the sending threshold N, then prepare to send data, first traverse Taskassign table ( Figure 6 ), find the computing node 1 where the target is located,...
example 2
[0085] Example 2: The target data ph6 arrives (that is, the new target data arrives)
[0086] Step 1: Thread0 of the Master node receives the target data through the network interface, and puts it into the opened buffer buffer, and receives the data of the ph6 target this time;
[0087] Step 2: Thread1 reads the data ph6 from the buffer and queries the map table. At this time, the data of the target ph6 does not exist in the map table, so add data to the value of the row where ph6 is located in the map table, and record the arrival time of the target data at the same time;
[0088] Step 3: At this time, the length len of the data packet in the value of ph6 is 1, which is less than the set sending threshold N, then the data will not be sent, and the first round of processing for ph6 is over, and then the data of ph6 will come continuously. If the length is equal to the sending threshold N, use the task scheduling strategy to prepare to send data;
[0089] Step 4: Use the formu...
example 3
[0091] Example 3: Target disappearance processing, taking ph4 as an example
[0092] Step 1: Every time the Master node Thread1 inserts the incoming data ph4 into the map table, it will calculate the difference between the current time and the target timestamp record;
[0093] Step 2: If the difference is greater than N, it is considered that the previous ph4 target has disappeared, delete the previous record from the map table, and update the Taskassign table and Proctasknum table at the same time;
[0094] Step 3: consider the target ph4 as a new target, and handle it according to the arrival of a new target, as in Example 1;
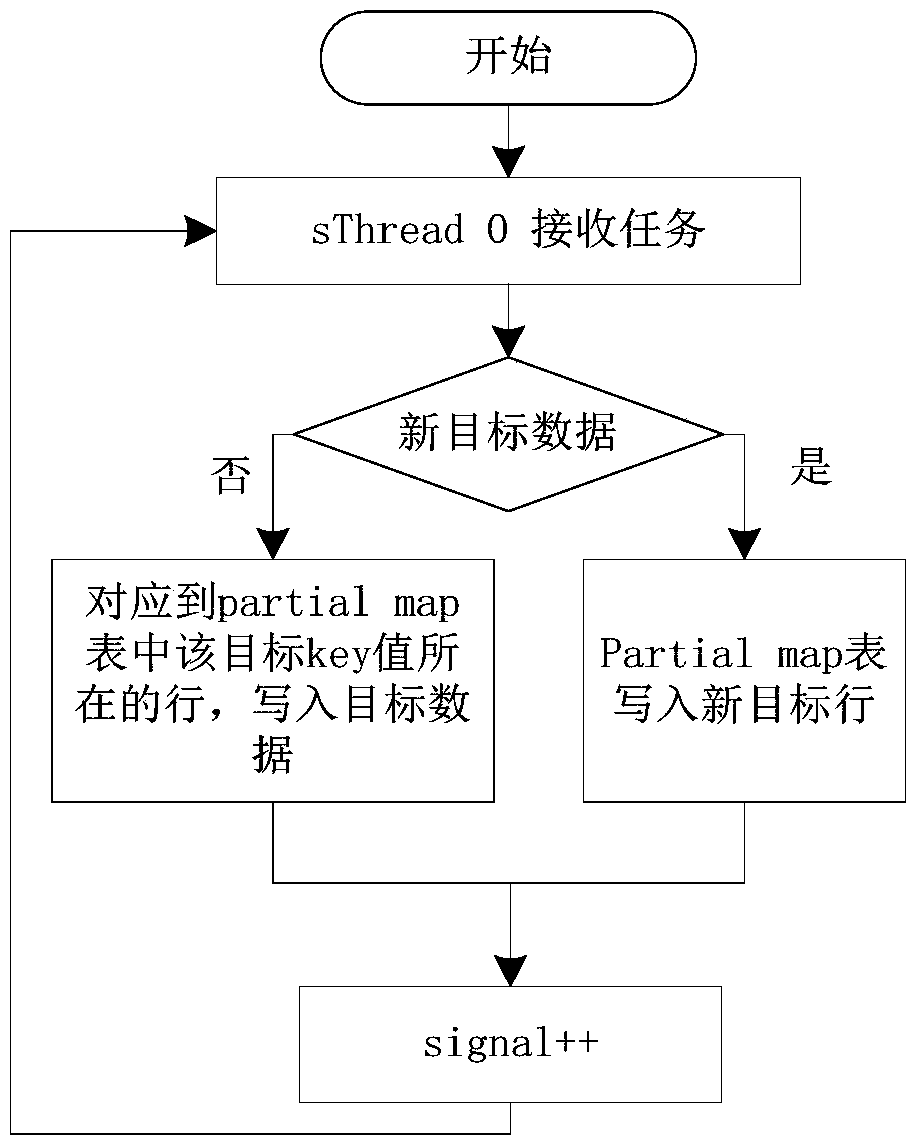
[0095] Step 4: sThread0 of the slave node uses the same method to maintain the partial map table, but the threshold at this time is at least N×T+a, where a is the upper limit of network transmission delay.
[0096] It can be seen from the above description of the implementation manners that those skilled in the art can clearly understand that the pre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com