Identity authentication method based on image recognition
A technology of identity authentication and image recognition, applied to individual input/output registers, instruments, time registers, etc., can solve the problems of forgery of personal information, loss of personal items, impersonation of others, etc., so that it is not easy to forge and be The effect of anti-theft, good operability, and improved confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to further explain the technical solution of the present invention, the present invention will be described in detail below through specific examples.
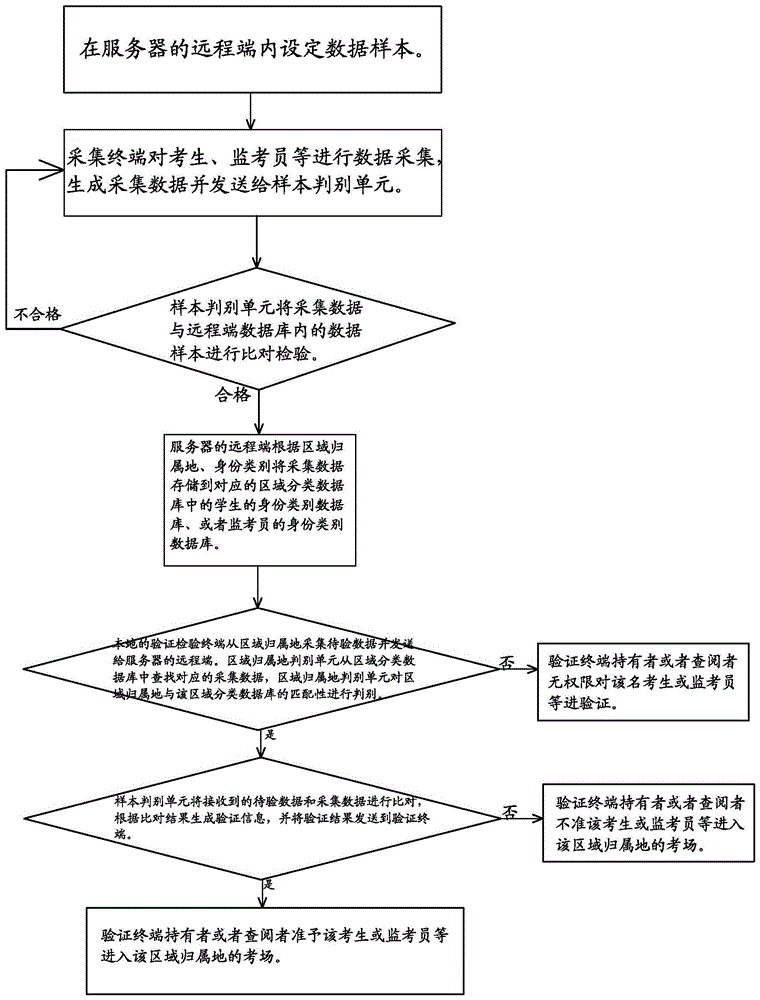
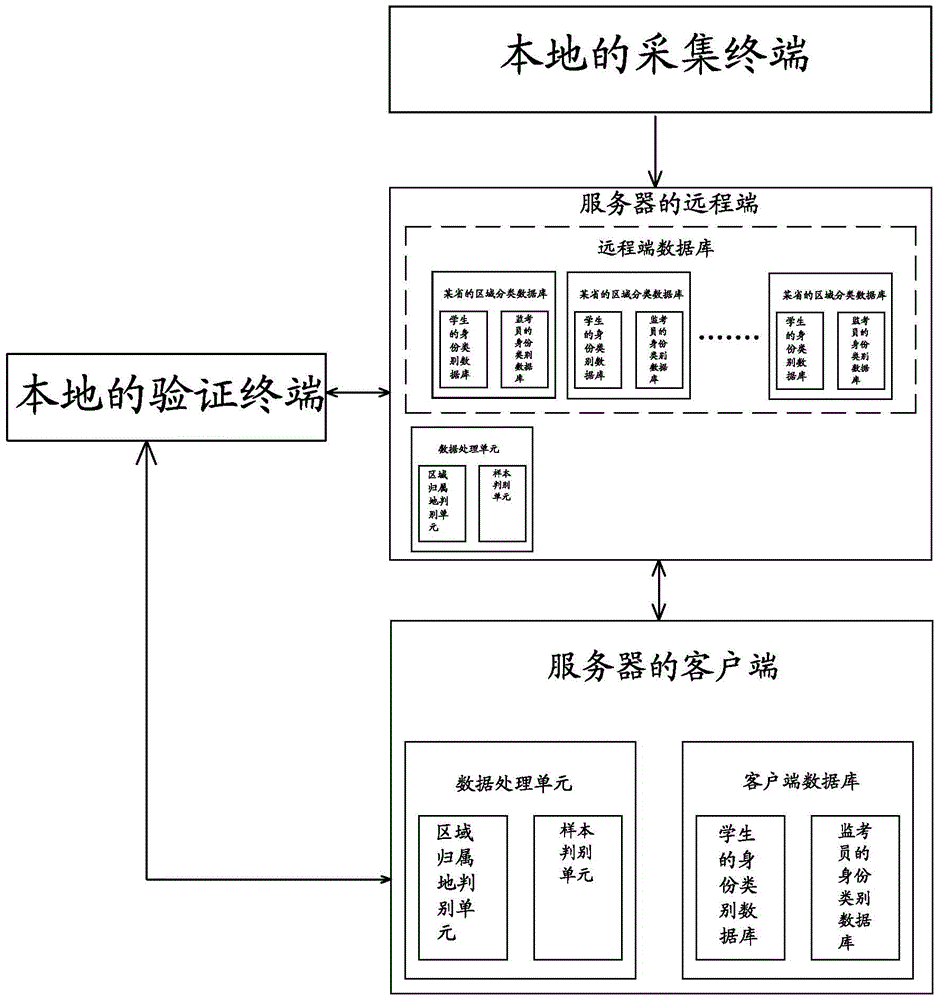
[0022] figure 1 It is the process flow of the entrance identity authentication method based on image recognition of the present invention. Such as figure 2 The present invention shown is realized by the following hardware, including a collection terminal, a server, and a verification terminal. The server includes a remote terminal and a client. The remote terminal is provided with a remote terminal database and a data processing unit. The remote terminal database includes multiple regional classification databases, and each regional classification database includes multiple identity category databases. The data processing unit includes a region attribution judging unit and a sample judging unit.
[0023] In addition, as an emergency solution, a data processing unit and a client database are additionally set...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com