System and method for in-place encryption
A technology of unencrypted and encrypted volumes, applied in the direction of internal/peripheral computer component protection, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] Various embodiments of the present disclosure are discussed in detail below. While specific implementations are discussed herein, it should be understood that this is done for illustration purposes only. A person skilled in the art will recognize that other components and configurations may be used without departing from the spirit and scope of the present disclosure.
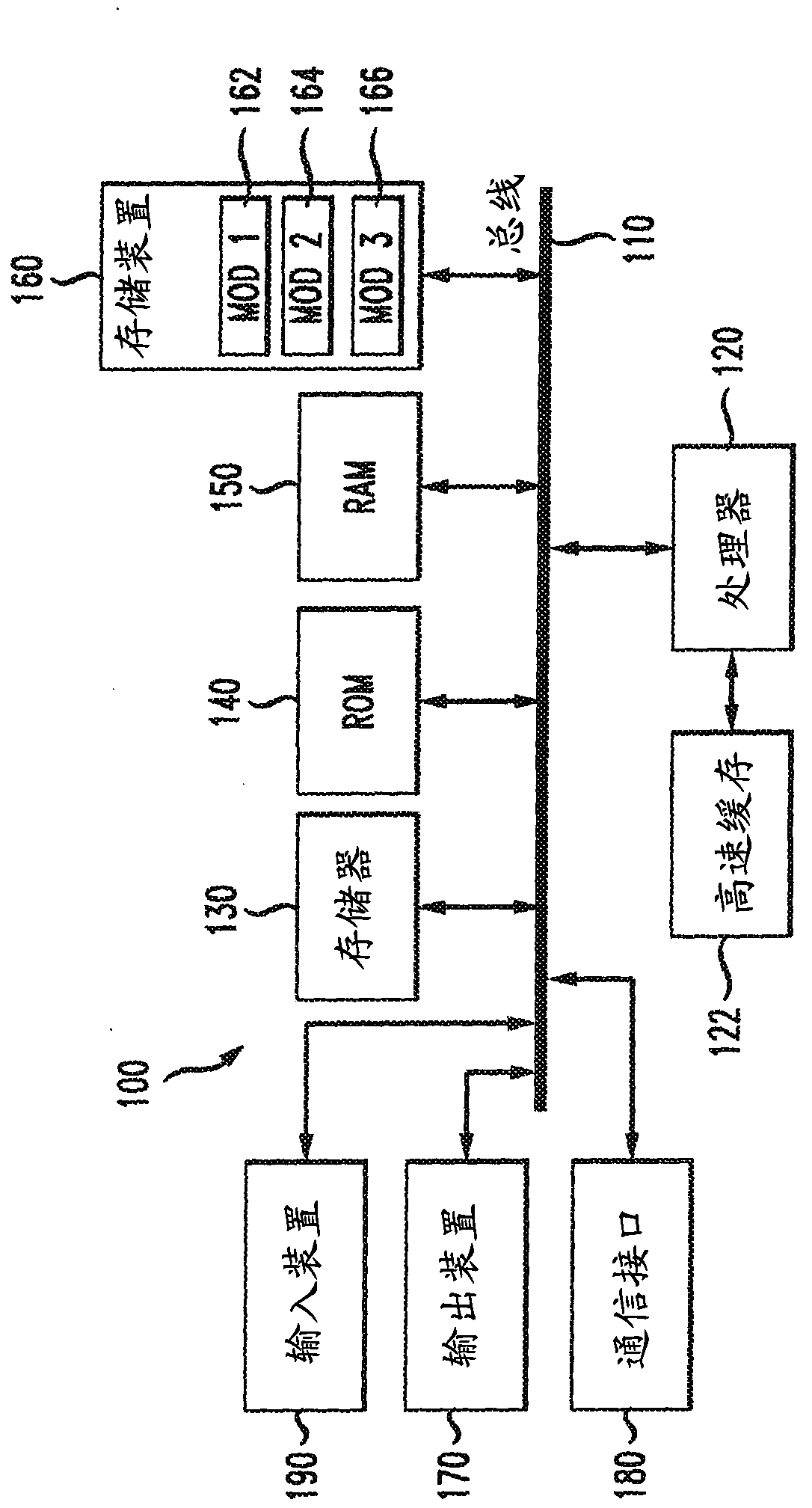
[0019] This disclosure addresses a need in the art to streamline and simplify the user experience for enabling and disabling encryption. Disclosed herein are the concepts that can be used to practice the invention in figure 1 A brief introductory description of a basic general-purpose system or computing device in . The following will be a more detailed description about the method and approach of in-situ encryption. Various variations illustrated by the various embodiments will be discussed herein. This disclosure now goes to figure 1 .
[0020] refer to figure 1 , the exemplary system 100 includ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com