Method for detecting user terminal and user terminal
A user terminal, user technology, applied in the direction of telephone communication, electrical components, branch equipment, etc., can solve the problem of mobile phone anti-theft function failure and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] In the method for determining whether a user terminal has been stolen provided in an embodiment of the present invention, anti-theft information may be preset, and the anti-theft information may include information for determining whether the user terminal has been stolen, and after determining that the user terminal has been stolen, perform anti-theft processing operations information on which it is based.
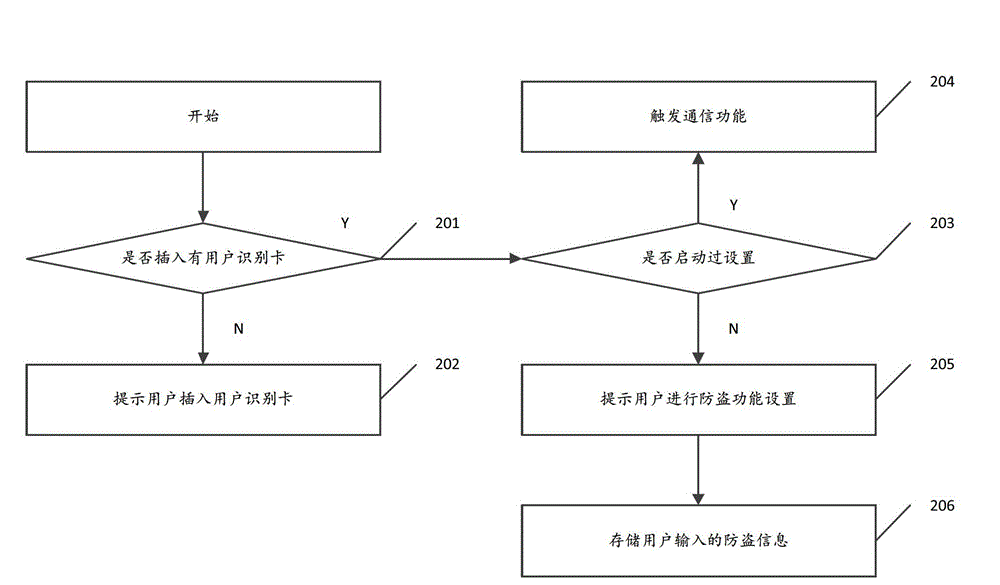
[0034] figure 2 Shown is the flow chart of setting anti-theft information for the first time provided by Embodiment 1 of the present invention, which specifically includes the following processing steps:
[0035] Step 201, after the user terminal is turned on, detect whether a subscriber identification card is inserted, if no subscriber identification card is inserted, go to step 202, if a subscriber identification card is inserted, go to step 203.
[0036] Step 202, prompting the user to insert a user identification card.
[0037] Step 203 , detecting whether t...
Embodiment 2
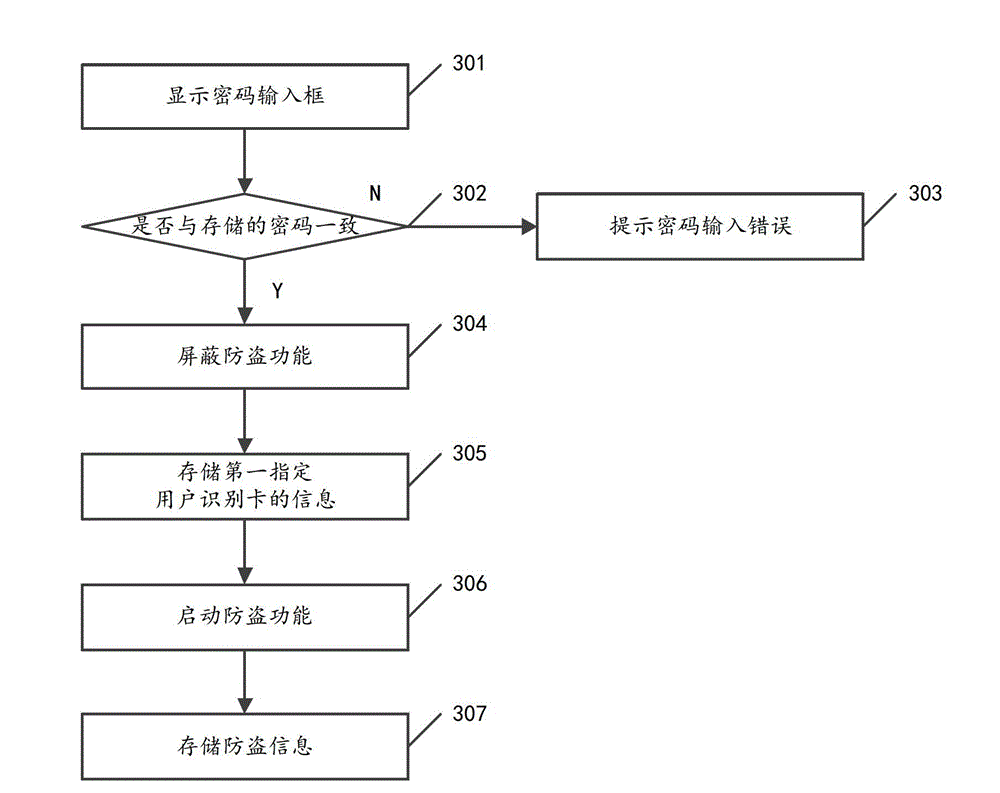
[0065] After the anti-theft information is preset, the anti-theft function can be activated to determine whether the user terminal is stolen, and after determining that the user terminal is stolen, trigger corresponding anti-theft processing operations.
[0066] Figure 4 Shown is the method for determining whether the user terminal is stolen provided by Embodiment 2 of the present invention, which specifically includes the following processing steps:
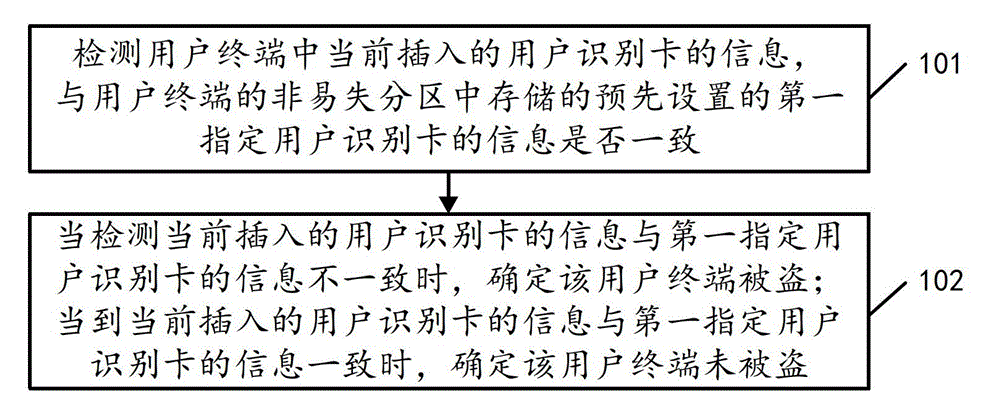
[0067] Step 401. When the preset trigger condition is satisfied, check whether the information of the subscriber identification card currently inserted in the user terminal is consistent with the preset information of the first designated subscriber identification card stored in the non-volatile partition of the user terminal, and if they are consistent , go to step 402, if not, go to step 403.
[0068] Wherein, the execution trigger condition can be flexibly set according to actual needs, for example, it can be triggered ever...
Embodiment 3
[0084] Based on the same inventive concept, according to the method for determining whether the user terminal is stolen according to the above-mentioned embodiments of the present invention, correspondingly, Embodiment 3 of the present invention also provides a user terminal, the structural diagram of which is as follows Figure 5 shown, including:
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com