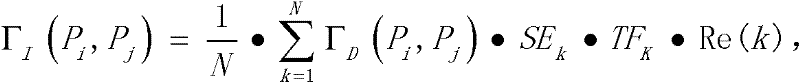Method for trust evaluation of nodes in network
A node and network technology, applied in the field of node trust evaluation in the network, can solve the problems of lack of adaptive adjustment ability to adapt to environmental factors, etc., and achieve the goals of enhancing system availability and effectiveness, resisting damage from malicious nodes, good adaptability and efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
[0026] The node trust evaluation method in the network of the present invention, the method is, for any node P in the network i and node P j , node P i Maintain a node P with j Interactive time-window-based list of records, node P i and node P j The interaction time contains at least one history record; save the interaction information of each node, and update the corresponding information after the interaction;
[0027] Node P i According to the expression Γ(P i , P j ) = ω 1 ·Γ D (P i , P j )+ω 2 ·ΓI (P i , P j ) to determine the node P j The overall trust degree Γ(P i , P j );
[0028] The calculation process of the corresponding parameters in the above formula is as follows,
[0029] Determining the direct trust degree Γ D (P i , P j ) and feedback trust degree Γ I (P i , P j ),
[0030] where f 1 , f 2 ,..., f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com