Score Mellin transform-based optical image encryption method
A technology of Merlin transformation and encryption method, which is applied in the field of information security, can solve the problems of speed and cost limitations, and achieve high security, good resistance to attack, and enhanced security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] Embodiment 1: Image encryption based on double random phase encoding.
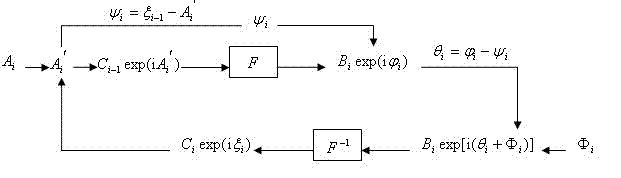
[0034] This implementation scheme is based on the principle of dual random phase encoding, and the encryption process comprehensively utilizes fractional Merlin transform and fractional Fourier transform. The encryption and decryption process can be expressed as follows:
[0035] Encryption process: (1-1)
[0036] Decryption process: (1-2)
[0037] in represents the input plaintext, represents the ciphertext, represents the decrypted image, express Fractional Merlin transform of order (assuming axis and The same order of transformation is carried out in the axial direction), express order of the Fractional Fourier Transform (assuming axis and The same order of transformation is carried out in the axial direction), and for distribution in independent white noise.
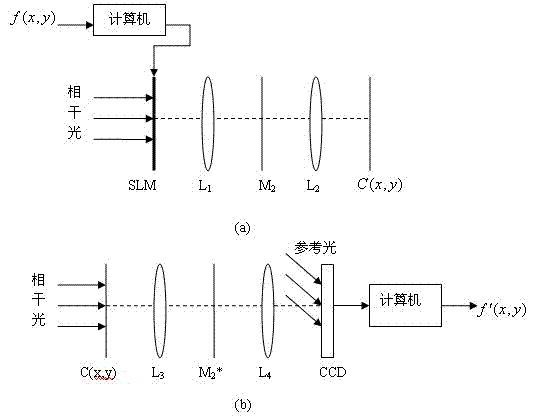
[0038] The schematic diagram of the optical image device of this embodiment is as follows figure 1 ...
Embodiment 2
[0043] Embodiment 2: Image encryption based on multi-order fractional Merlin transform.
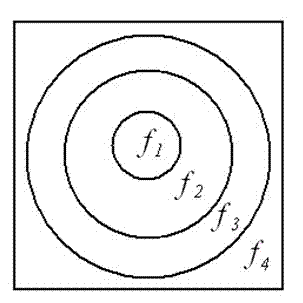
[0044] to image Fractional Merlin transform of different orders is carried out in different areas of different regions. Since the fractional Merlin transform is convenient for ring processing, the sub-image are annular regions with different inner and outer radii. by For example, put Decomposed into 4 ring domains. like figure 2 As shown, these rings are all centered on the center of the picture, where is a radius of the circle, is the inner radius of The outer radius is ring domain, is the inner radius of The outer radius is ring domain, is the inner radius of The outer radius is ring domain, where It is the distance from the center of the image to the top corner of the image. right conduct Order Fractional Merlin Transform to get ,in .
[0045] (2-1)
[0046] in Represents the two-dimensional fractional Merlin transform, Indicates the o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com