Method for distributing patch
A patch and honeypot technology, applied in the field of network security, can solve problems such as inability to ensure computer system security, inability to adapt to large-scale network management, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Hereinafter, the present invention will be further described in detail in conjunction with the accompanying drawings and embodiments.
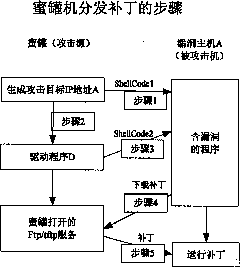
[0027] According to one embodiment of the present invention, a patch distribution method using honeypot technology is provided. By replacing the content of the attack message sent out by the honeypot, the method replaces harmful malicious code delivery with beneficial ones related to vulnerabilities. Patches are delivered and run on remote hosts, enabling targeted patch distribution. In this way, vulnerable hosts can be patched in time without introducing new attack traffic to the network.
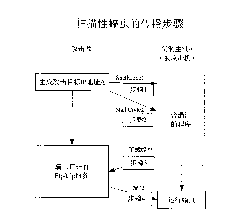
[0028] Scanning worms are typical malicious codes that attack vulnerabilities. In this embodiment, the attack mechanism of scanning worms needs to be used for patch delivery. The propagation steps of mainstream scanning worms are as follows: figure 1 shown.
[0029] Step 1: The worm on the attack source host randomly generates a target IP address...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com