Open file encrypting method without distinguishing file types
A transparent file encryption and file type technology, applied in the field of information security, can solve file renaming and other problems, and achieve the effect of solving system vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
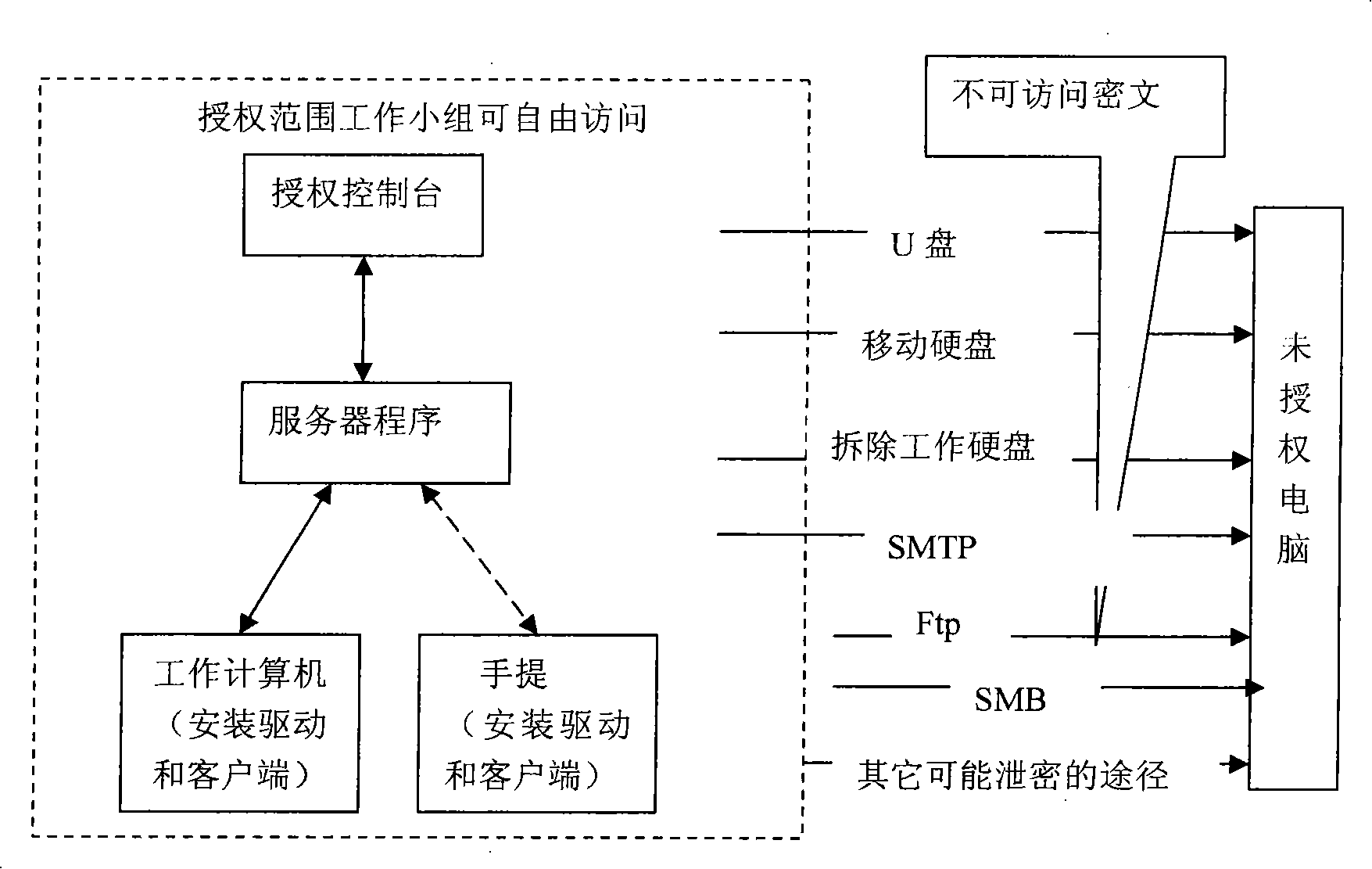
[0026] The architecture of the transparent file encryption system is as follows: figure 1 , the encryption system is composed of an encryption client program, an encrypted file driver, a server program, and an authorization console. All computers within the authorized range are installed with transparent file encryption drivers and clients. With these drivers and clients, authorized computers in the group can access documents in the group without any business process changes. Documents can be transmitted within the group by email or QQ transmission. These documents are actually encrypted, but visitors in the group can directly access them, because they are decrypted and can be accessed directly by applications while opening them. to plaintext.
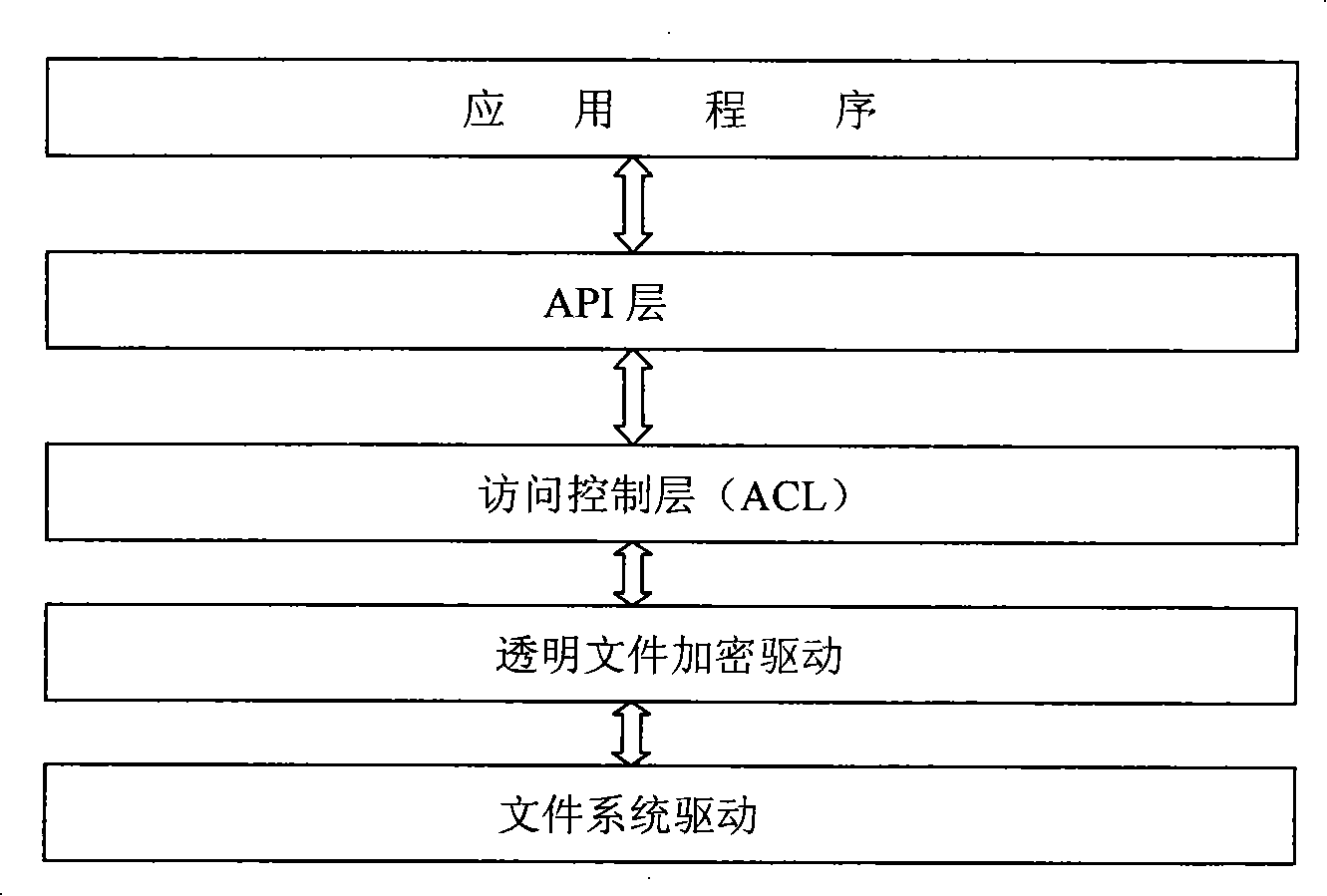
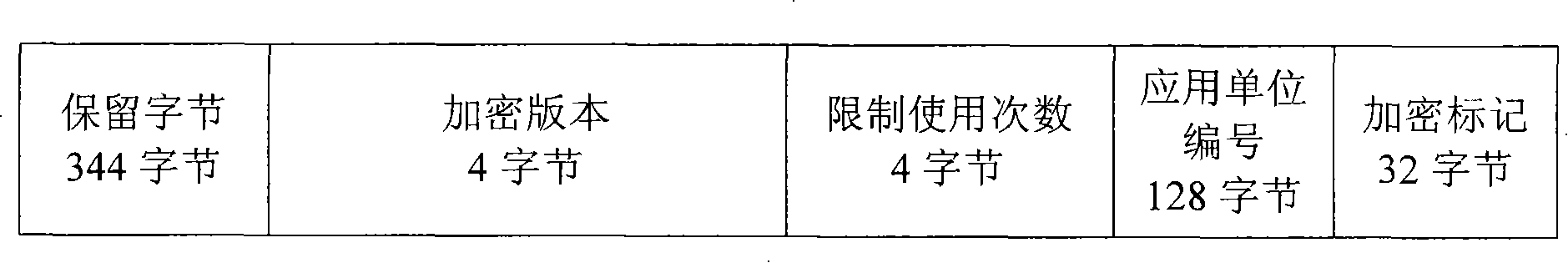
[0027] The location of the driver of the transparent file encryption system, such as figure 2 As shown, the tra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com