Method for locking application program
An application program and user technology, applied in the field of communication, can solve problems such as effective protection and non-reporting, and achieve the effect of avoiding theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
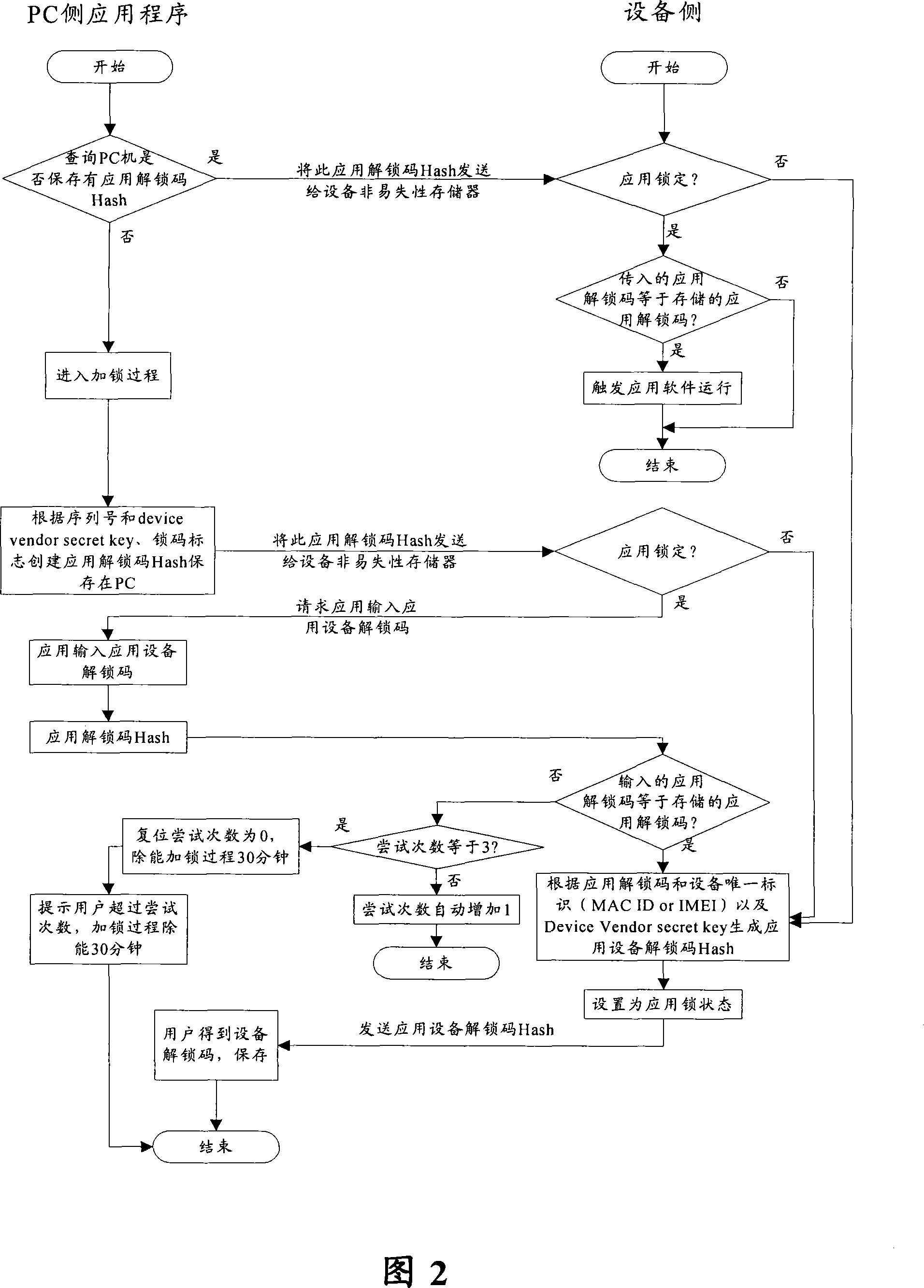
[0025] The present invention is applicable to all mobile terminals with PC-side software
[0026] In this embodiment, a method for locking an application program is provided. The method is applied to a communication environment including a terminal and a device connected to the terminal.
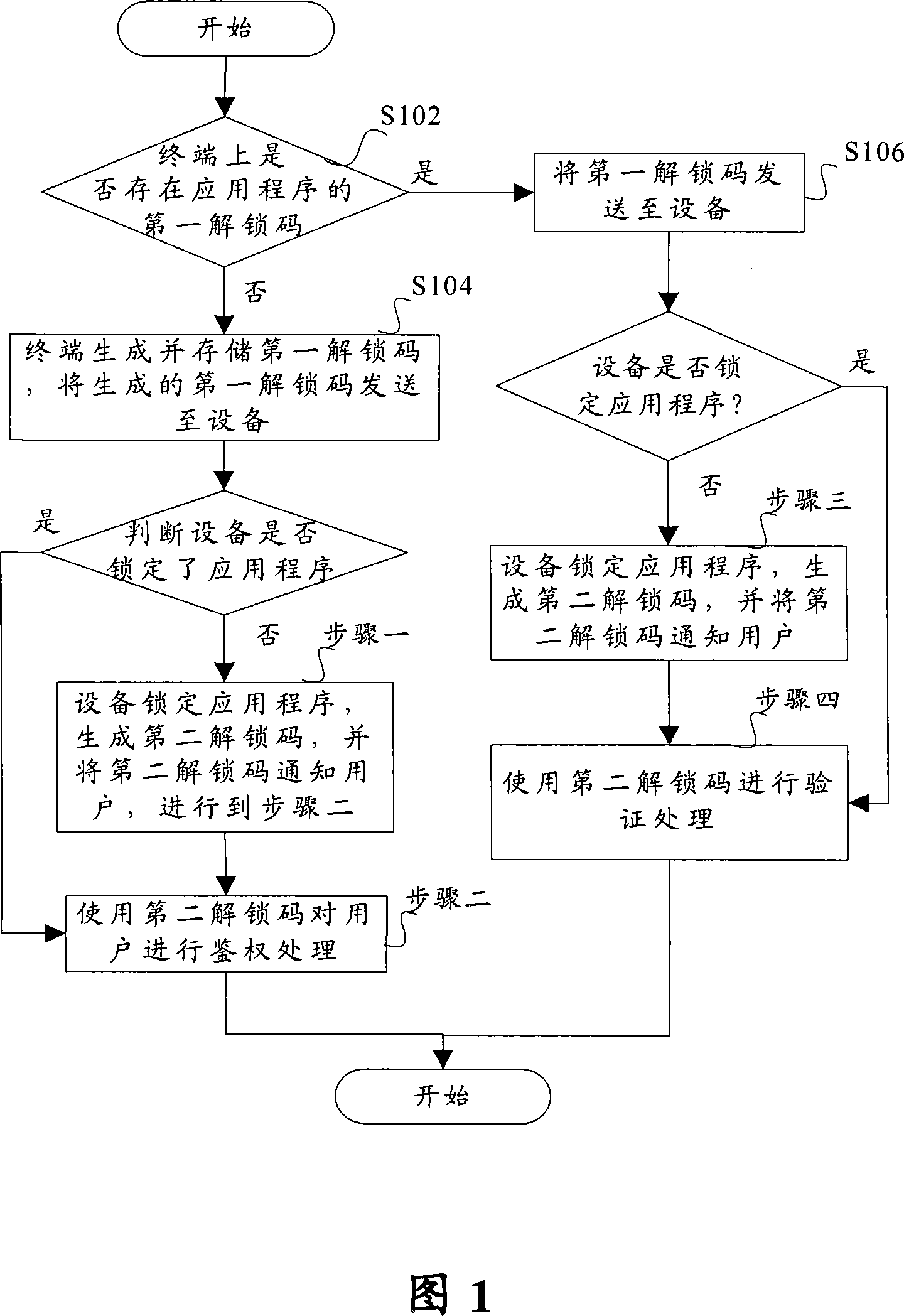
[0027] As shown in Figure 1, the method includes: step S102, when running the application program stored on the terminal, judging whether there is a first unlock code of the application program on the terminal;
[0028] Step S104, in the case of judging that the first unlock code does not exist on the terminal, the terminal generates and stores the first unlock code, and sends the generated first unlock code to the device; judges whether the device has locked the application program, and if the judgment result is no In the case of , go to step 1, otherwise go to step 2:
[0029] Step 1, the device locks the application program, generates a second unlock code, and notifies the user of the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com