Method and device for the secure operation of a switching device
A switchgear and working technology, applied to the parts of protective switches, electric switches, protective switches, etc., can solve problems such as insecurity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
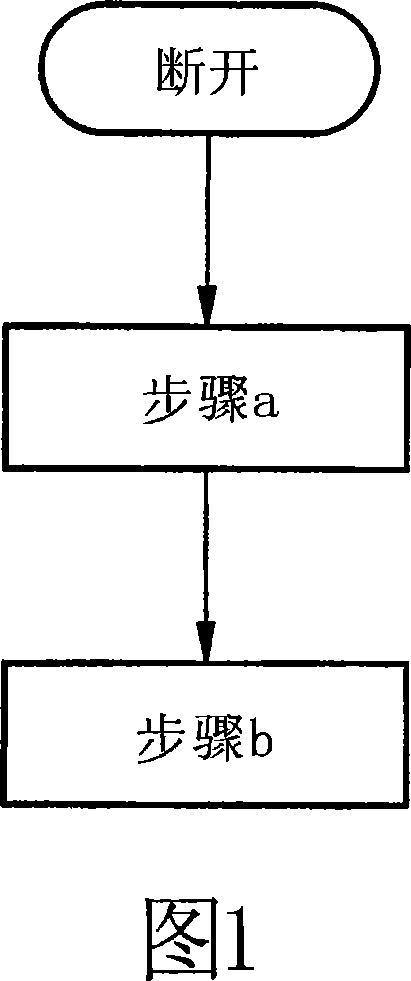
[0076] As shown in Figure 1, after receiving a disconnection signal, the method of the present invention mainly implements the following two steps:
[0077] Step a) identifying whether the movable contact bridge of at least one main contact exceeds a breaking point after opening; and
[0078] Step b) Interrupting further operation of the switching device if said trip point has not been exceeded after a predetermined duration has elapsed.
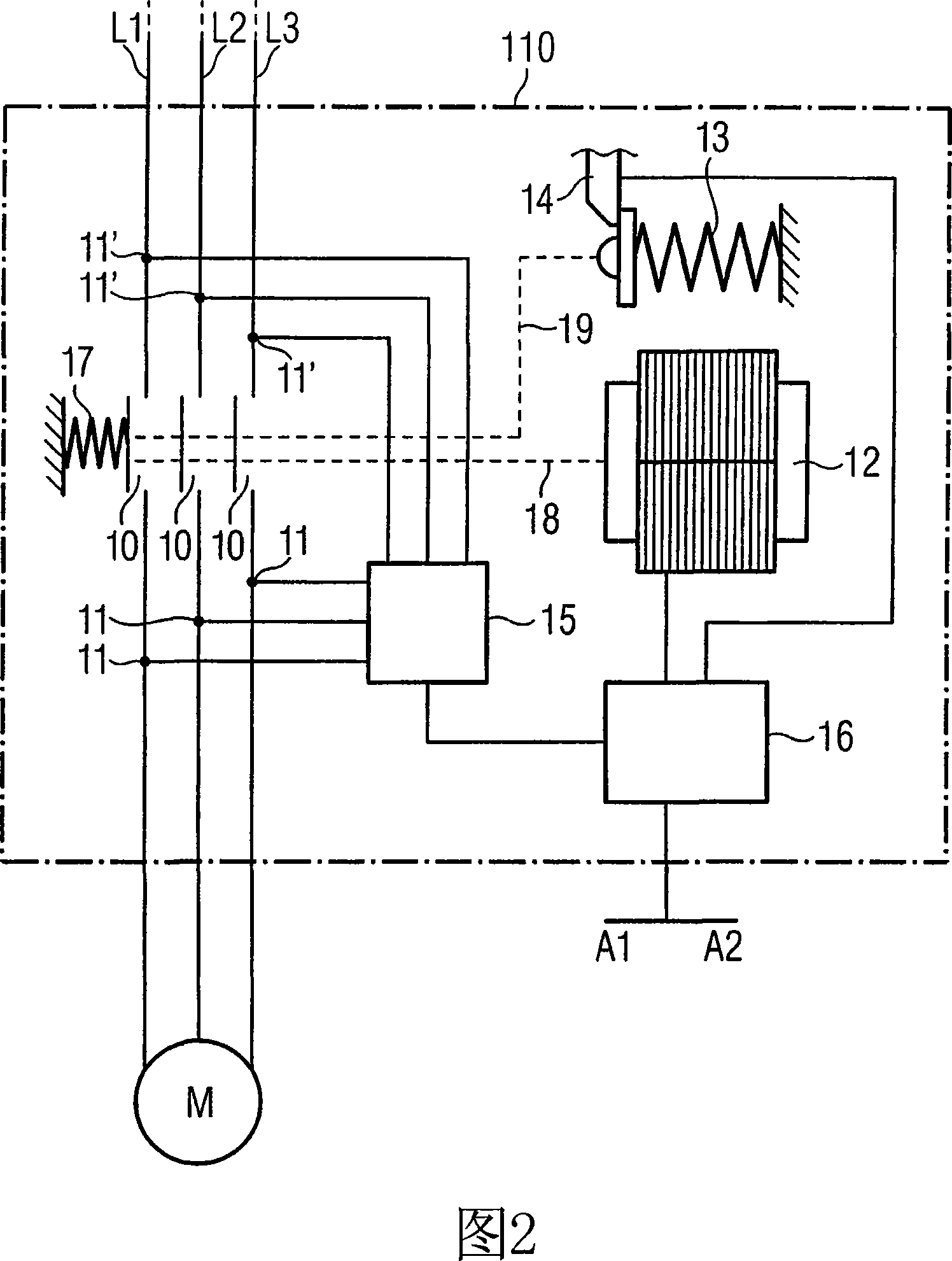
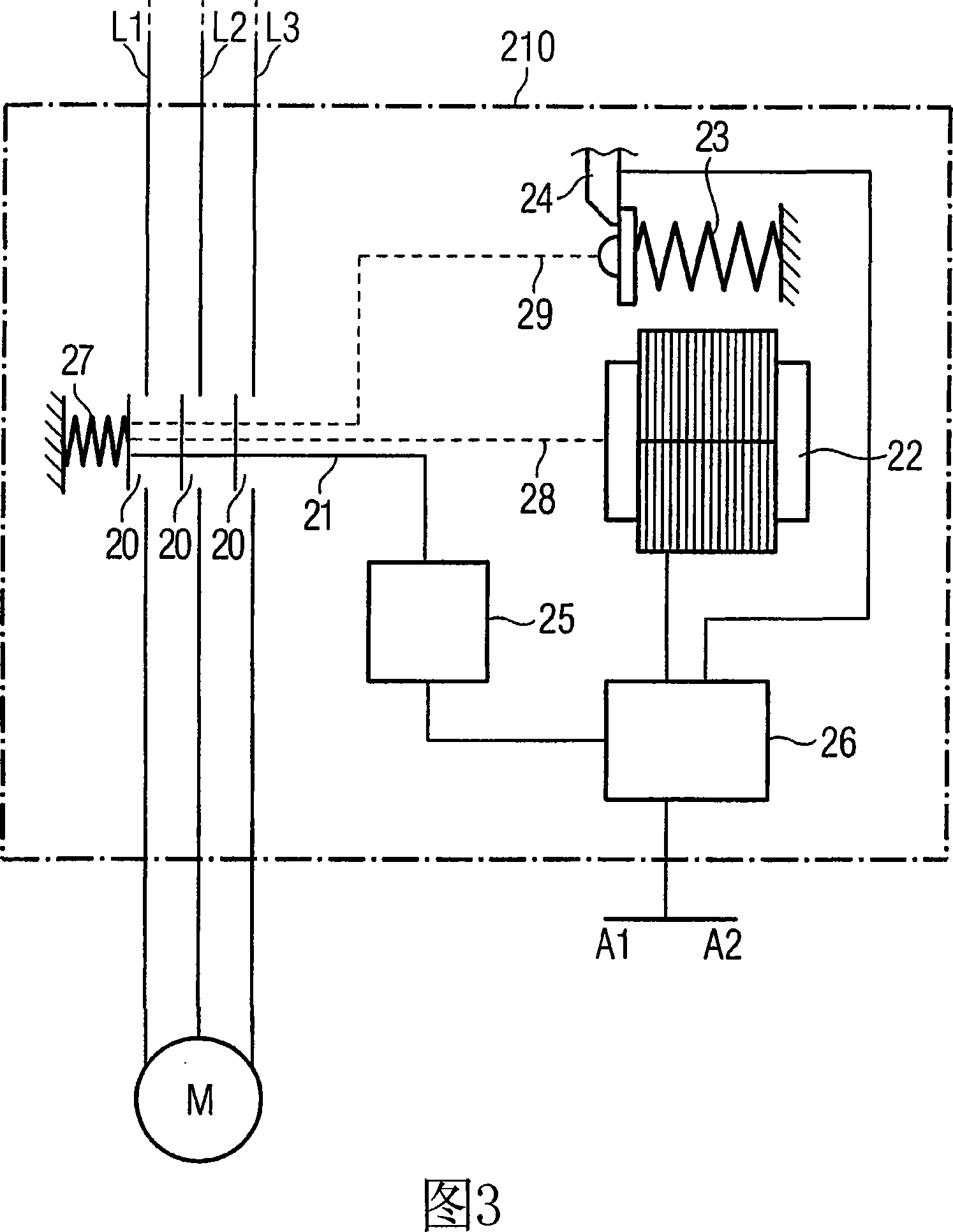
[0079]Accordingly, it shall be checked whether all main contacts of the switching device have been opened after the opening operation, i.e. in particular after receiving an opening signal requesting opening of the three main contacts of a three-pole switching device . According to the invention, this is achieved by checking whether a specific breaking distance traveled by the movable contact bridge when breaking is greater than a predetermined breaking point. If the detected opening travel of one of the contact bridges remains below this o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com