A method for solving configuration failure of radio resource control process
A radio resource control and configuration failure technology, applied in wireless communication, radio/inductive link selection arrangement, selection device, etc., can solve problems such as RRC process configuration failure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0050] Example 1.
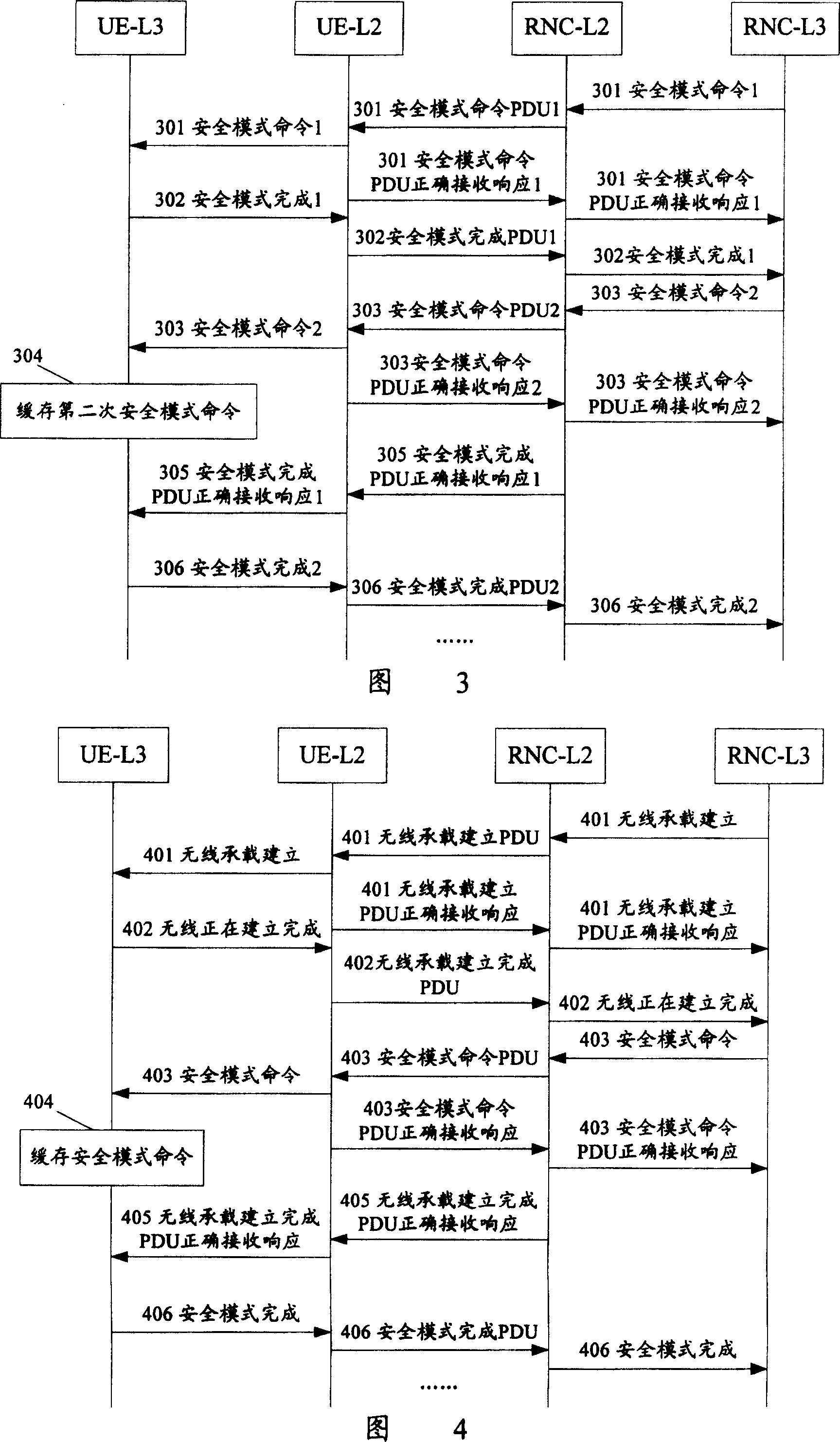
[0051] Fig. 3 is a safe mode control process with two consecutive successful configurations in a preferred embodiment of the present invention. In this embodiment, the IE "Ciphering ModeInfo" is included in the two consecutive safe mode command messages, and the time when the second safe mode command message arrives at the UE may be earlier than the first safe mode completion message PDU correctly receives the response. UE's time.
[0052] As shown in Figure 3, the two consecutive safe mode control procedures of the present invention include the following steps:
[0053] Step 301: RNC-L3 sends the first security mode command message to RNC-L2, which contains the IE "Ciphering Mode Info", RNC-L3 sends the security mode command message to UE-L2, and UE-L2 correctly receives the first security mode command message. After a safe mode command message PDU, upload it to UE-L3, and return the first safe mode command message PDU correctly received response to RNC-L2, RN...
Example Embodiment
[0066] Example 2.
[0067] In this embodiment, the IE "IntegrityProtection Mode Info" is included in the two consecutive safe mode command messages, and the time when the second safe mode command message arrives at the UE may be earlier than the first safe mode completion message PDU is correctly received The time the response arrives at the UE.
[0068] The processing flow of this embodiment is basically the same as the steps 301 to 306 described in Embodiment 1. the difference lies in:
[0069] 1. In this embodiment, the UE needs to modify the information element Reconfiguration in the variable INTEGRITY_PROTECTION_INFO in step 302, step 305, and step 306;
[0070] 2. In this embodiment, in steps 302 and 306, UE-L3 will perform integrity protection configuration after receiving the security mode command message.
[0071] Through the method of this embodiment, it is also possible to basically guarantee the normal progress of the two safe mode control processes.
Example Embodiment
[0072] Example 3.
[0073] In this embodiment, two consecutive security mode command messages may include IE "CipheringMode Info", or IE "Integrity Protection Mode Info", or both IE "Ciphering Mode Info" and IE "Integrity Protection Mode Info" , And the IEs contained in the two safe mode command messages have an intersection.
[0074] As mentioned above, this embodiment can include the following five situations: in the two consecutive safe mode control processes, the first safe mode command message contains the IE "Ciphering Mode Info", and the second safe mode command The message contains both IE "Ciphering Mode Info" and IE "Integrity Protection Mode Info"; or vice versa; or the first safe mode command message includes IE "Integrity Protection Mode Info", and the second safe mode command The message contains both IE "Ciphering Mode Info" and IE "Integrity Protection Mode Info"; or vice versa; or two consecutive safe mode command messages contain both IE "Ciphering Mode Info" and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com