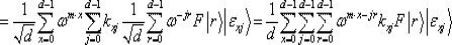Efficient Key Agreement Method and System Based on Fourier Transform
A Fourier transform and key agreement technology, applied in the field of efficient key agreement methods and systems based on Fourier transform, can solve the problems of weak security, difficult state of multi-particle entanglement, low communication efficiency, etc. High security, improved quantum communication efficiency, and enhanced security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
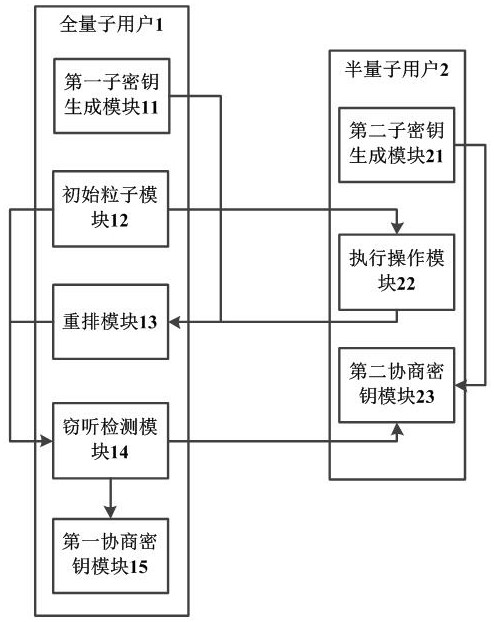
[0050] This embodiment discloses a high-efficiency key agreement system based on Fourier transform, and its structure diagram refers to figure 1 , the system includes full quantum user 1 and half quantum user 2; full quantum user 1 includes a first subkey generation module 11, an initial particle module 12, a rearrangement module 13, an eavesdropping detection module 14, and a first negotiated key module 15 ;
[0051] The semi-quantum user includes a second sub-key generation module 21, an execution operation module 22, and a second negotiated key module 23; wherein,
[0052] The first subkey generating module 11 is used to randomly generate the first subkey;
[0053] The second subkey generating module 21 is used to randomly generate the second subkey;
[0054] The initial particle module 12 is used to generate a plurality of single particles, and randomly arranges the single particles to generate a quantum sequence and publishes them; 4n single particles are generated in t...
Embodiment 2
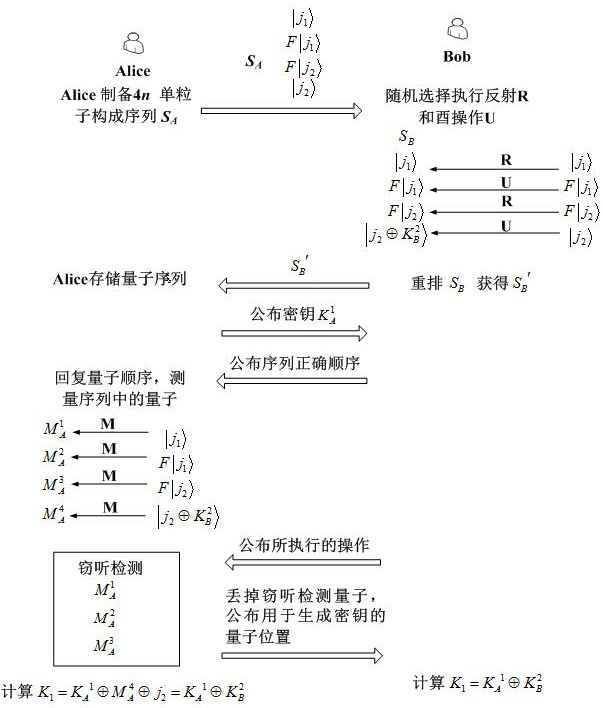
[0061] Based on the system of Embodiment 1, an efficient key agreement method based on Fourier transform is provided in this embodiment. The step-by-step flowchart of this method can be referred to figure 2 , including steps:
[0062] S1: The full quantum user and the half quantum user randomly generate the first subkey and the second subkey respectively;
[0063] The method in this embodiment is based on the key agreement between two users, where the full quantum user (Alice) is a full quantum node with complete quantum functions, and the half quantum user (Bob) is a half quantum node;
[0064] In this step, Alice and Bob randomly generate their respective subkeys for generating the final key: the first subkey and the second subkey ,in Represent Alice and Bob keys respectively and The a-th and b-th elements in , , , n is a positive integer, and d is a positive integer, which can be selected according to needs. Generally, when d is 8, it can meet the actual appl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com