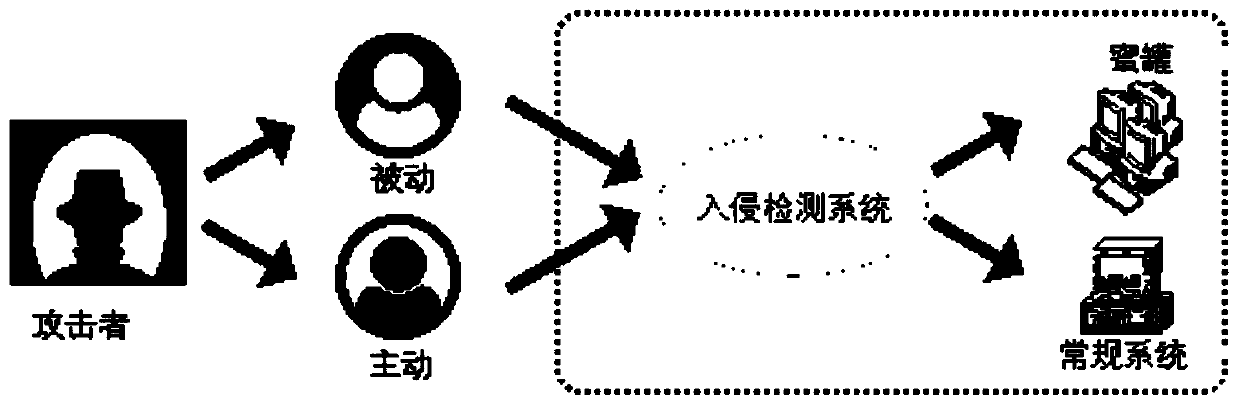
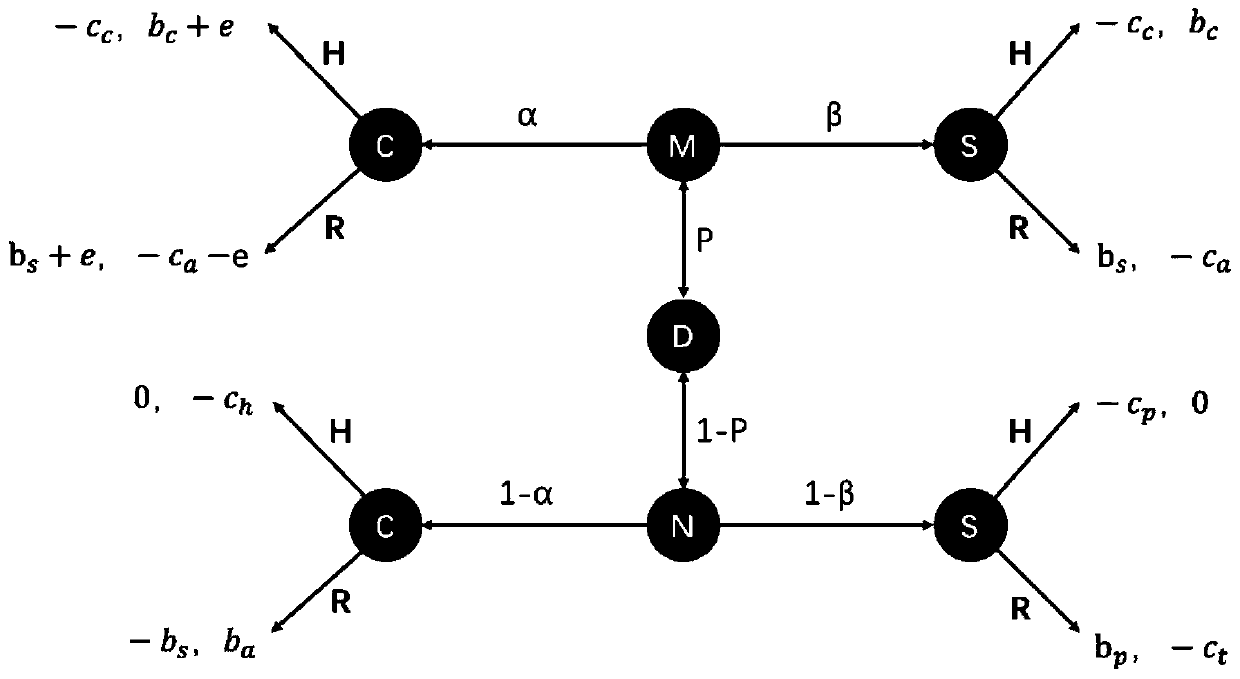
A network security defense method based on a Bayesian improved model
A network security, model technology, applied in the direction based on specific mathematical models, computing models, instruments, etc., can solve problems that have not been better studied
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] Hereinafter, the present invention will be further described in detail with reference to the drawings and specific embodiments.
[0068] An intelligent evaluation method for network security based on game theory includes the following steps:
[0069] Step 1. The defender sets the parameters of the income matrix and uses the Bayesian model to solve the convergence point Said Expressed as
[0070] Step 2. The defender sets the parameter a according to the demand, and the a is the probability that the attacker with N (ordinary user) identity adopts the C (conventional) strategy, and the historical revenue model is used to solve the convergence point Said Is the convergence point of the historical return model, expressed as x∈(0,1) in Time value.
[0071] Step 3: Defender settings (Choose the cumulative relative returns of strategies H and R) initial value (equivalent to setting α 0 , Which is the initial confidence of malicious users). Waiting for user access.
[0072] Step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com