Mining method and device of attacking organization
A technology for attackers and organizations, applied in the field of network security, it can solve the problems of difficult to fight against continuously changing and upgraded attack methods, inability to perceive attacking organizations, and lack of data intelligence functions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
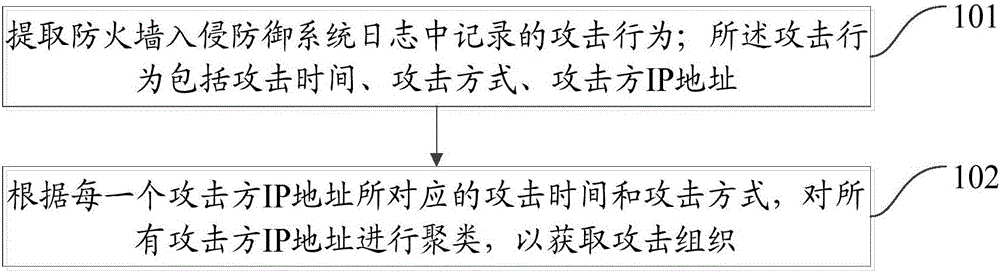
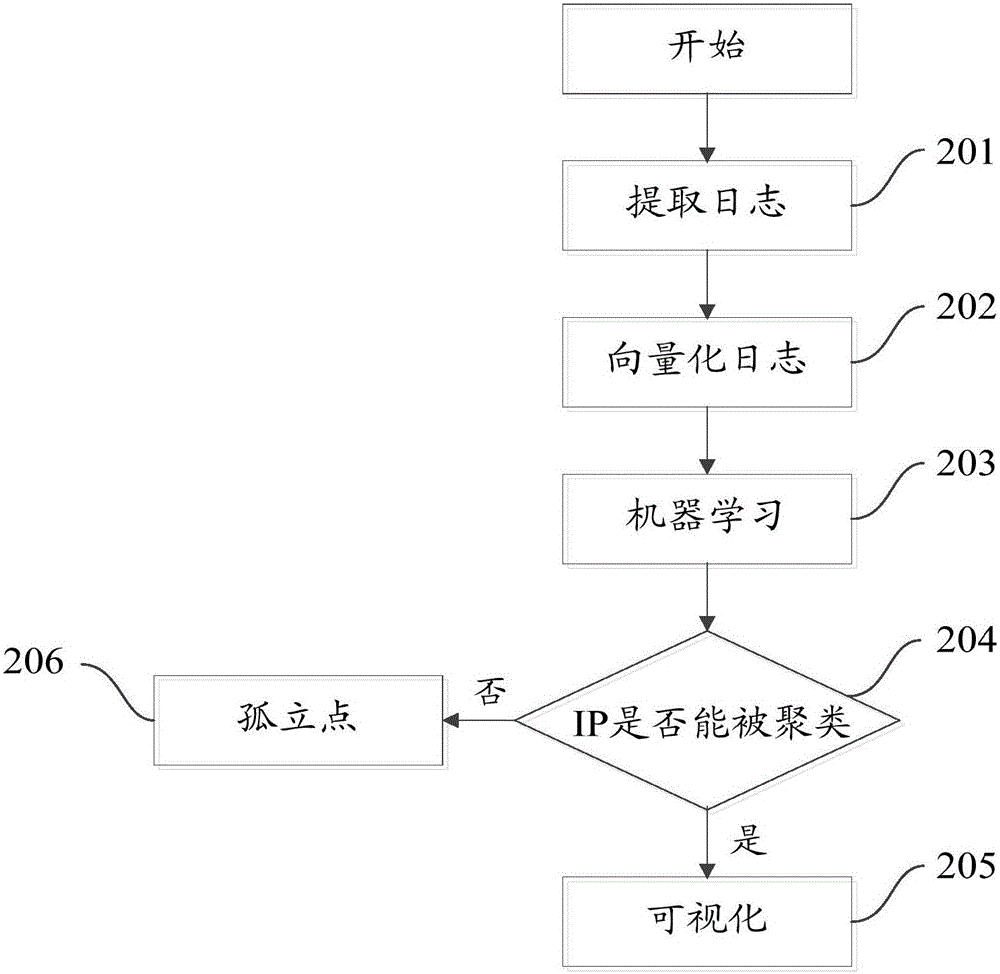
[0037] figure 1 It is a schematic diagram of the implementation flow of the mining method for attacking organizations in the embodiment of the present invention, the method includes:
[0038] Step 101: Extracting the attack behavior recorded in the log of the firewall intrusion prevention system; the attack behavior includes attack time, attack mode, and IP address of the attacker;
[0039] Specifically, the network attack behavior is identified, and the identified attack behavior is recorded in the log of the firewall intrusion prevention system (Intrusion Prevention System, IPS); at least one IP address of the attacker recorded in the log of the firewall IPS is extracted in different attacks. The attack method used by time.
[0040] Here, the identifying the network attack behavior may be to use a firewall to identify the network attack behavior; the firewall IPS log records the attack behavior identified by the firewall within a preset time, and the preset time may be one ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com