Data overwriting method
A technology of data overwriting and data, which is applied in erasing methods, digital data protection, recording/reproducing/deleting methods, etc., can solve problems such as irregular coverage, waste of computer resources, etc., to increase difficulty, improve efficiency, and reduce consumption Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
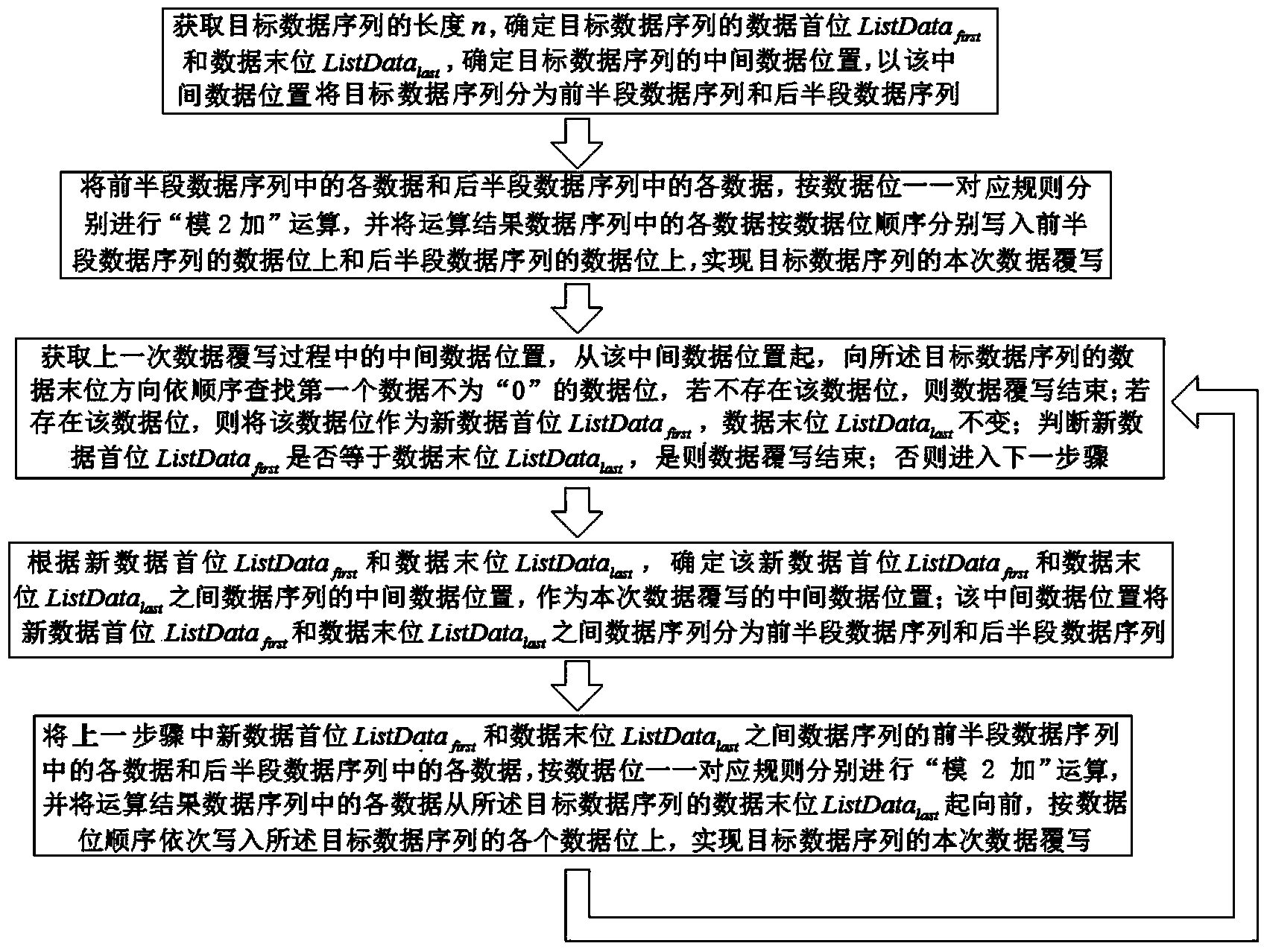
[0033] In the actual application process of the data overwriting method designed by the present invention, there are two specific embodiments, such as figure 1 Shown embodiment one, comprises the steps:
[0034] Step 001. Obtain the length n of the target data sequence, and determine the first data of the target data sequence ListData first And the end of the data ListData last , according to the length n, the data first ListData first And the end of the data ListData last determining the intermediate data position of the target data sequence, and dividing the target data sequence into a first half data sequence and a second half data sequence by the intermediate data position;
[0035] Step 002. Each data in the first half of the data sequence and each data in the second half of the data sequence are respectively subjected to a "modulo 2 addition" operation according to the data bit one-to-one correspondence rule, such as adding the first data bit in the first half of the ...
Embodiment 2
[0041] In the actual application process of the data overwriting method designed by the present invention, such as figure 2 The second shown embodiment includes the following steps:
[0042] Step 001. Obtain the length n of the target data sequence, and determine the first data of the target data sequence ListData first And the end of the data ListData last , according to the length n, the data first ListData first And the end of the data ListData last determining the intermediate data position of the target data sequence, and dividing the target data sequence into a first half data sequence and a second half data sequence by the intermediate data position;
[0043] Step 002. Each data in the first half of the data sequence and each data in the second half of the data sequence are respectively subjected to a "modulo 2 addition" operation according to the data bit one-to-one correspondence rule, such as adding the first data bit in the first half of the data sequence The d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com