Extraction Method of Encrypted Network Flow Voiceprint Feature Vector
A voiceprint feature and extraction method technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as the inability to effectively identify protocols, the inability of traffic classification systems to correctly classify private encrypted protocol traffic, and the inability to identify hidden protocols. , to achieve the effect of rich and reliable knowledge
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
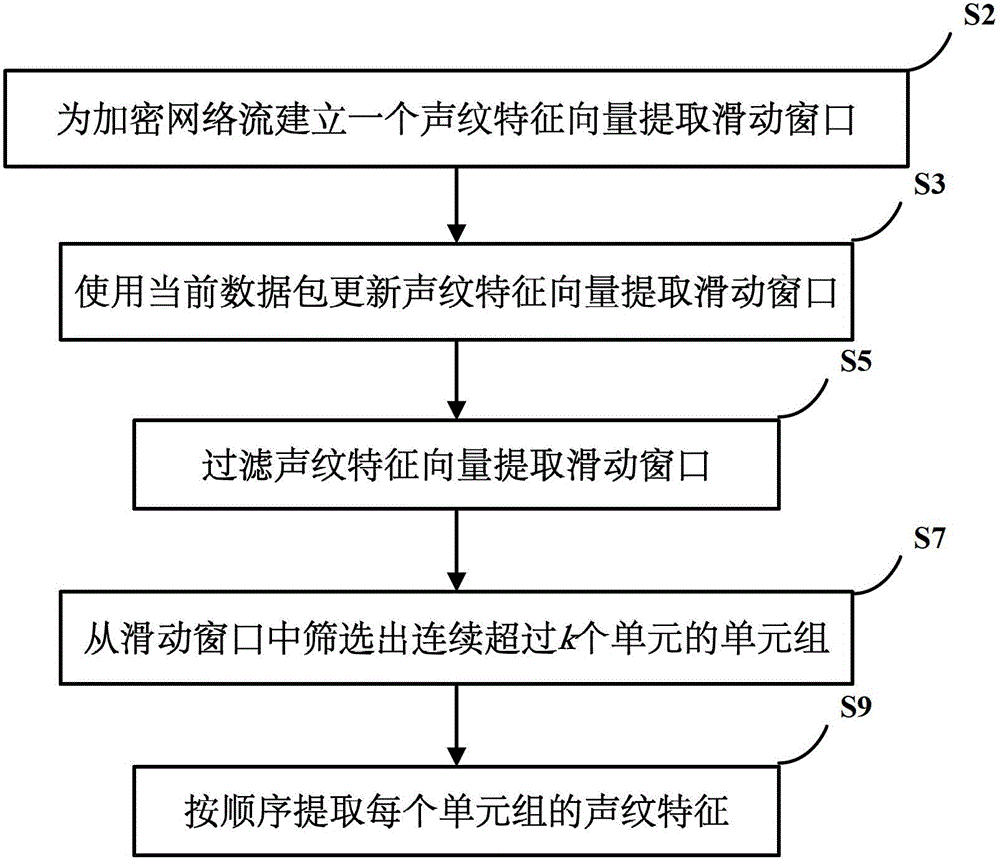
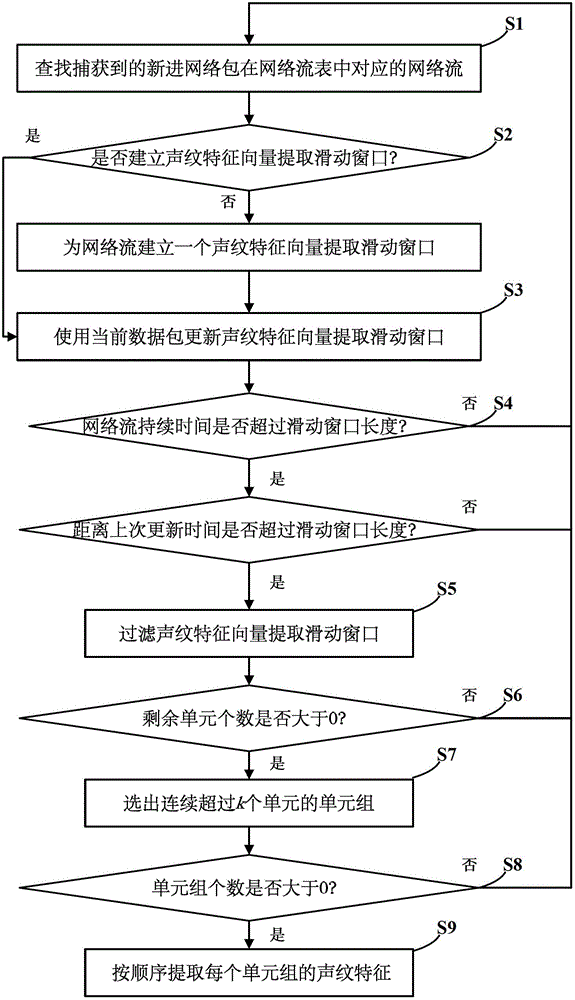
[0039] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
[0040] The statistical feature extraction method adopted by the current classification technology can only extract static statistical features from the network flow, which leads to the problem that the traffic classification system cannot correctly classify the private encryption protocol traffic, let alone effectively identify the protocol hidden in the encrypted proxy channel. The invention proposes a method for extracting feature vectors of encrypted network stream voiceprints. This method first uses a sliding window to record the time-series statistical characteristics of the encrypted network flow in a continuous period of time, then filters the processing units in th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com