Invite abuse prevention
A client and behavioral technology, applied in data processing applications, instruments, computing, etc., can solve problems such as increasing social networking sites
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0011] Overview
[0012] In order to establish connections in social networks, users can send and receive invitations to become part of each other's network. When the invitation is accepted, the user becomes a "friend" and can then transmit and share information. Unfortunately, this mechanism may be abused by attackers (such as spammers) who may create accounts and send out large numbers of invitations for illegal and / or undesired purposes.
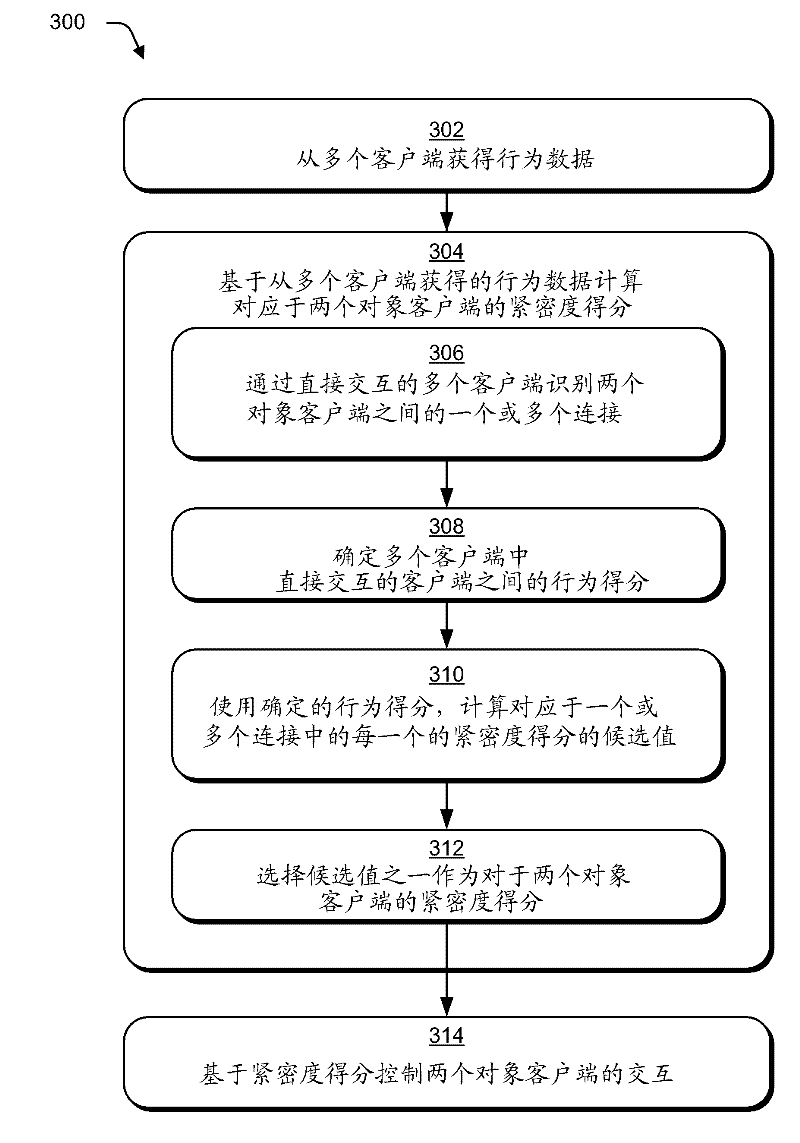
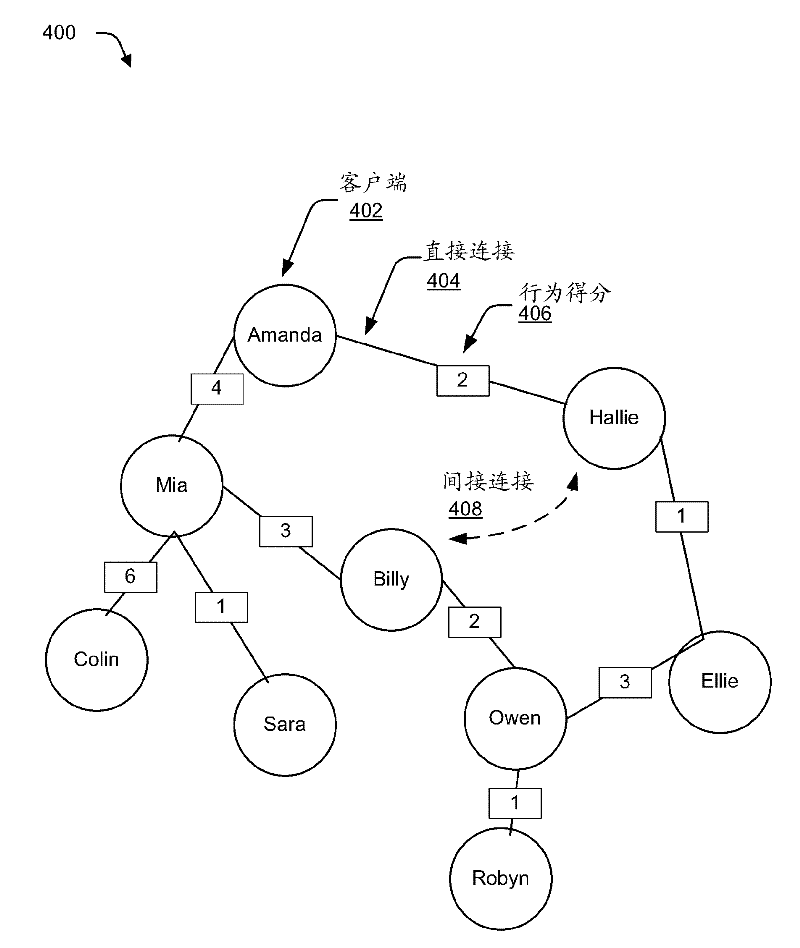
[0013] Describe techniques used to invite abuse prevention. In one implementation, data describing the mutual behavior of the client and one or more resources available via the service provider is obtained from multiple clients. Service providers can use data about mutual behavior to determine behavior scores between directly interacting clients. The determined behavior score can then be used to calculate the score between two object clients (ie, "potential friends") to control invitations and / or other interactions between the clients. Be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com