Access control method and equipment
An access control device and access control technology, applied in the network field, can solve the problems of limited personalized management and difficult control, and achieve the effect of personalized and refined management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
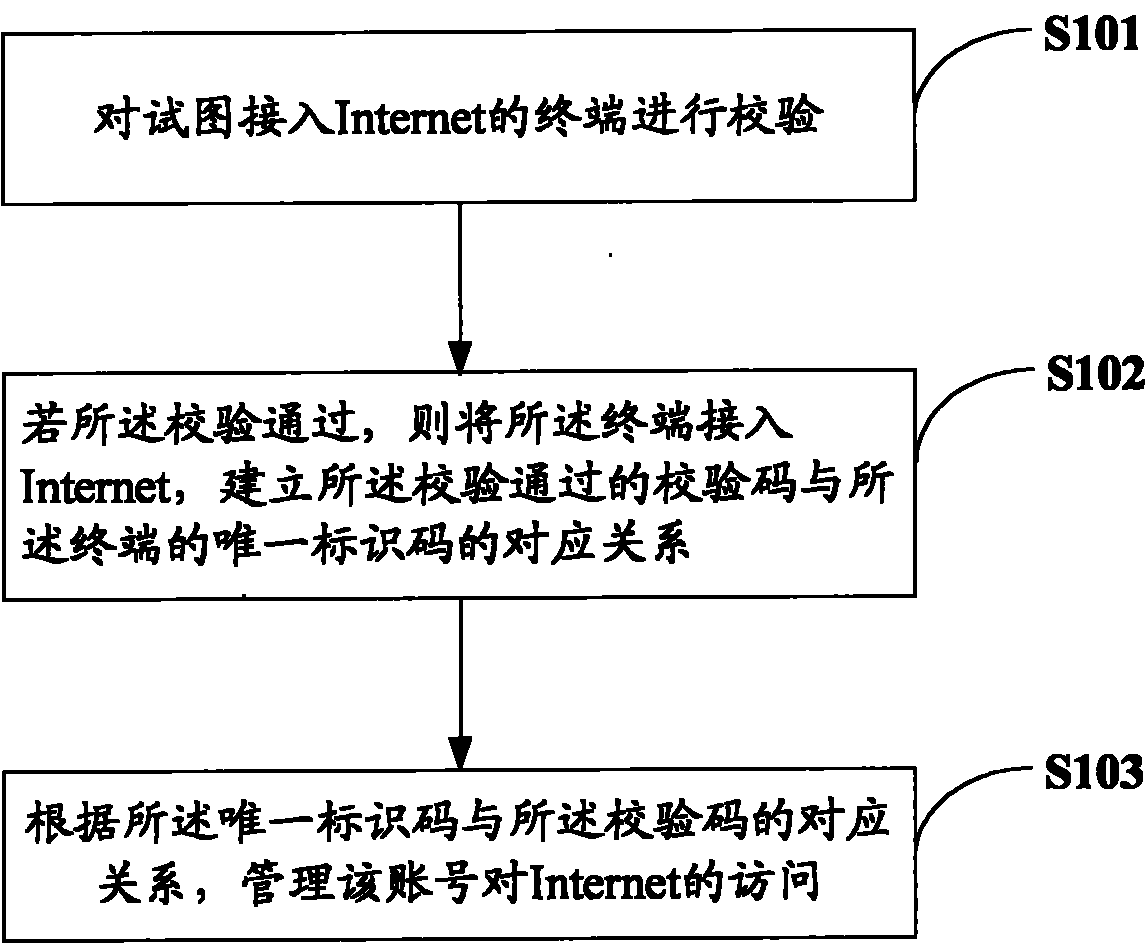
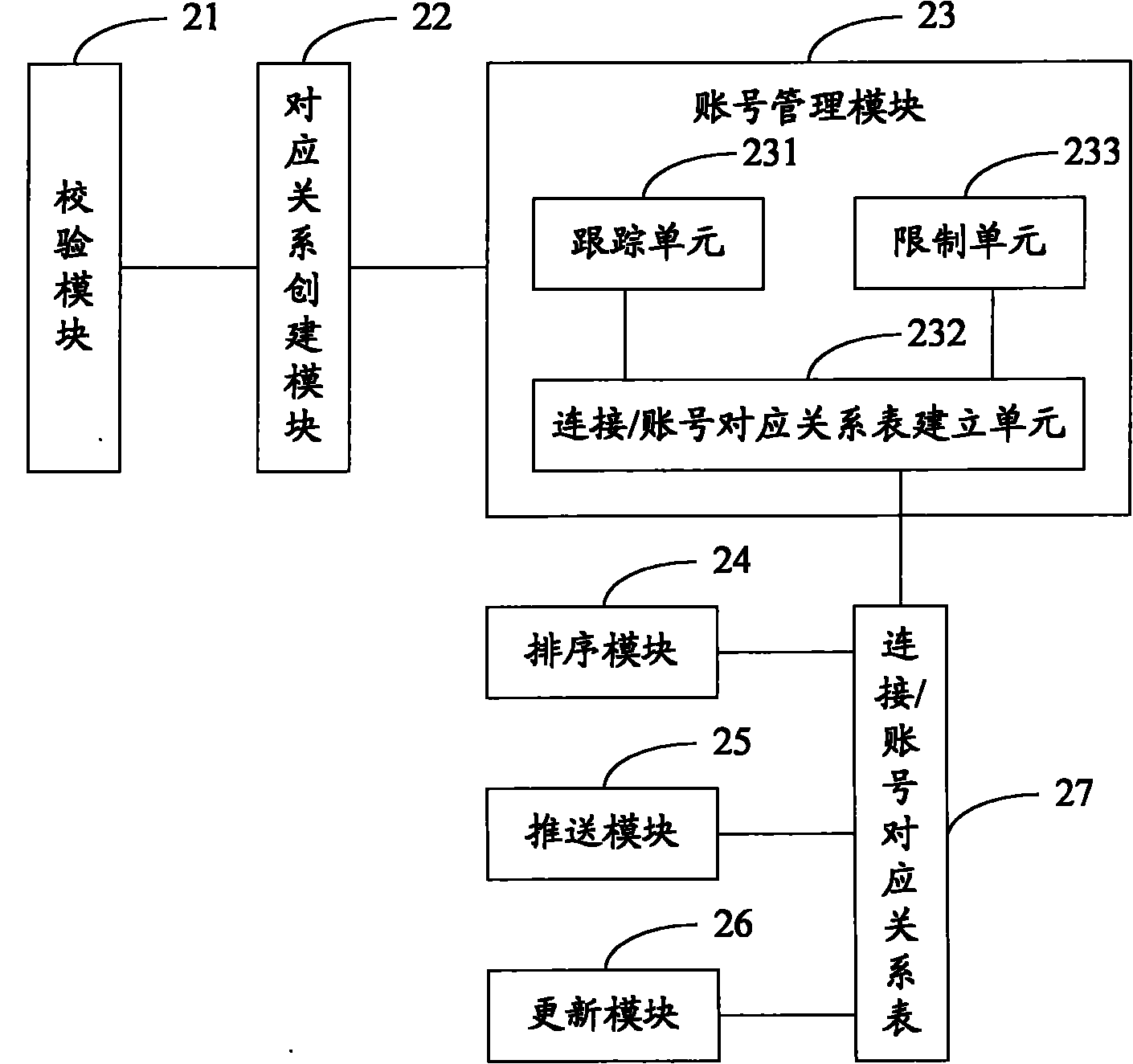
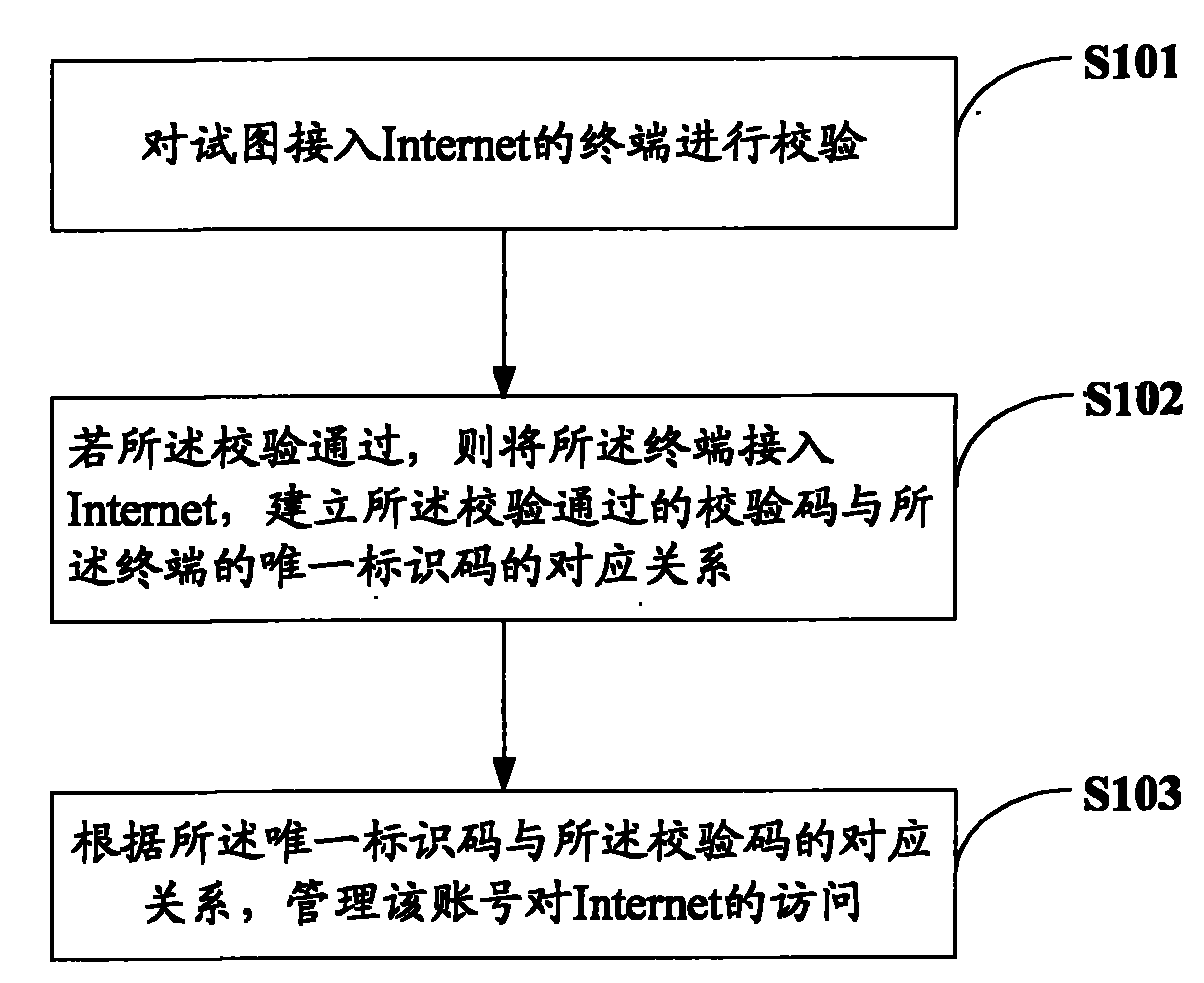
[0018] The embodiment of the present invention provides an access control method. The corresponding relationship between the verification code and the unique identification code of the terminal is established for the terminal that has passed the verification, and the unique identification code is compared with the unique identification code of the terminal. The corresponding relationship of the verification code manages the access of the account to the Internet. The embodiment of the present invention also provides corresponding access control equipment. Detailed descriptions are given below.
[0019] Please refer to figure 1 , The basic flow diagram of an access control method provided by an embodiment of the present invention mainly includes:
[0020] Step S101, verify the terminal trying to access the Internet.
[0021] Generally, a terminal accesses the Internet through an access control device. In the embodiment of the present invention, before a terminal such as a PC accesse...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com