Method and system for preventing copy card from embezzling service function
A technology for business functions and duplicating cards, which is applied in wireless communication, electrical components, security devices, etc., can solve problems such as duplicating card theft, achieve the effect of protecting users and standardizing network operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
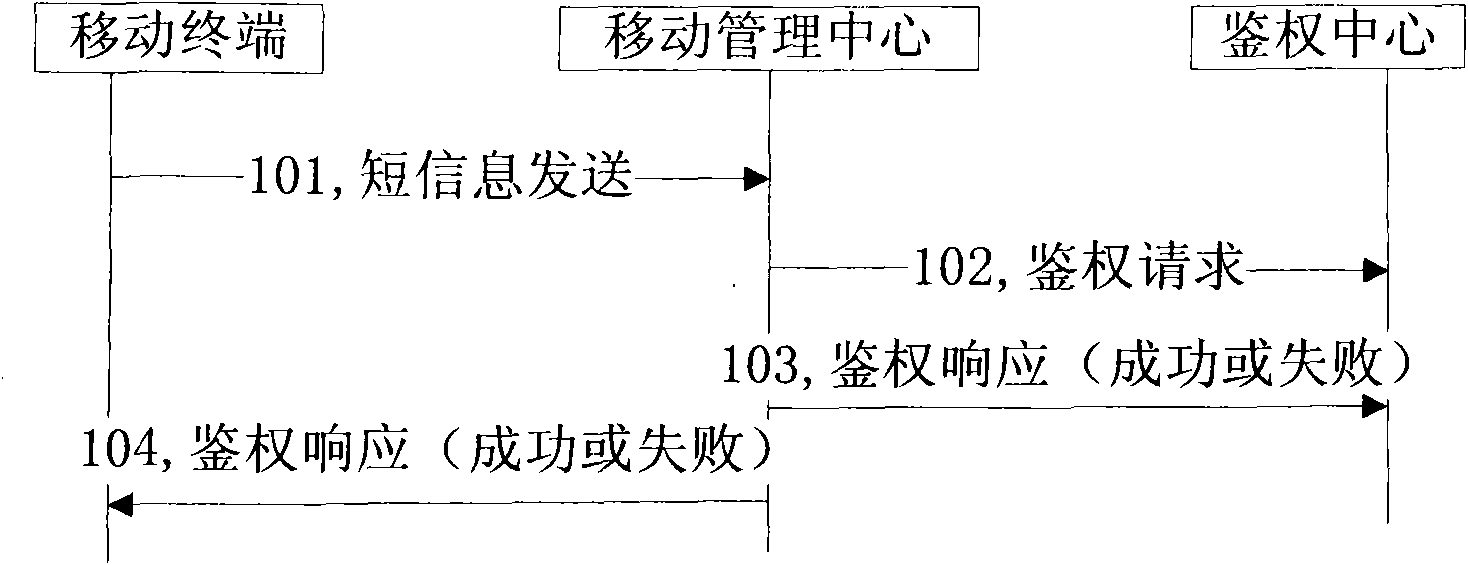
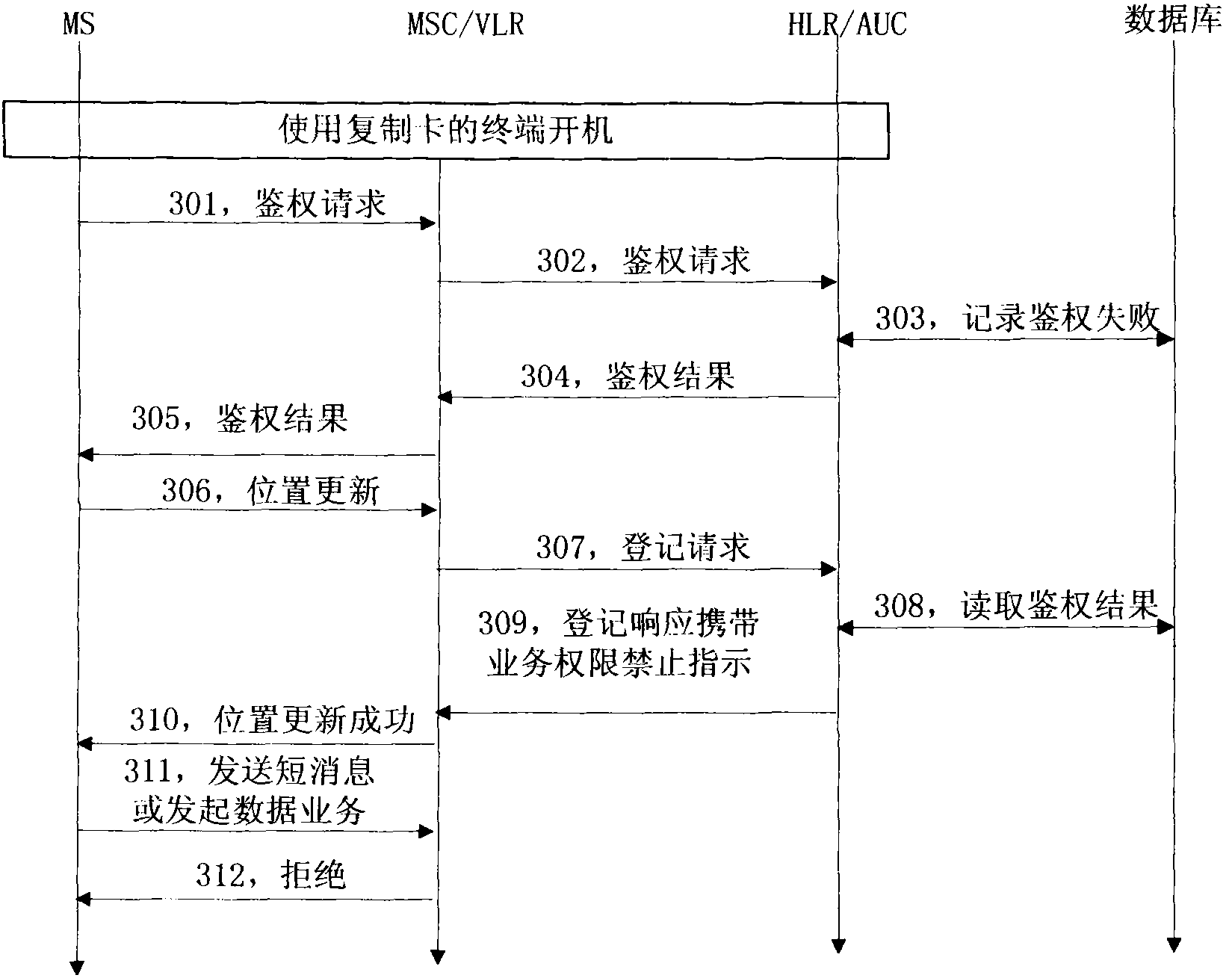
[0041] In the first embodiment, when the duplicate card is not registered with the authentication center, the authentication center notifies the MSC of the service right prohibition indication of the duplicate card through a registration response message.
[0042] Such as image 3 As shown, the method for preventing duplicating cards from embezzling business functions in Embodiment 1 specifically includes the following steps:
[0043] Step 301, when the user card is not registered with the authentication center, the terminal using the duplicate card is turned on, and the terminal initiates an authentication request to the MSC according to the requirements of the MSC;
[0044] Step 302, the MSC forwards the authentication request of the terminal to the authentication center;
[0045] Step 303, the authentication center authenticates the user card and obtains an authentication result, that is, judges that the authentication status of the user card is invalid, and records the au...
Embodiment 2
[0057] In the second embodiment, when the duplicate card is not registered with the authentication center, the authentication center notifies the MSC of the service right prohibition indication of the duplicate card through a qualification request response message.
[0058] Such as Figure 4 As shown, in the second embodiment, the method for preventing duplicating cards from embezzling business functions specifically includes the following steps:
[0059] Steps 401 to 405 correspond to image 3 Step 301 to step 305 in the same;
[0060] Step 406, the terminal sends a short message or initiates a data service;
[0061] Step 407, when the MSC finds that the user's qualification time limit expires or is invalid, it initiates a qualification request to the HLR;
[0062] Step 408, the HLR obtains the authentication result of the user card recorded in the database, checks that the authentication state of the user card is invalid, and determines that the user card is an illegal ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com